Network Security Defined - Encryption
Encrypting information is an important security method and provides one of the most basic security services in a network: authentication exchange. Other methods, such as Digital Signatures and data confidentiality, also use encryption.
Encryption Techniques
Encryption techniques use several kinds of algorithms: two major types are those that use keys and those that do not use keys.
Simple encryption techniques that do not use keys transform the information to be encrypted. You could encrypt a message written in English text by adding 1 to the ASCII value of each letter. This sort of algorithm is easy to decipher and not very secure: all you need to know is the algorithm.
Much more secure algorithms use some sort of key along with the data. Two major types of encryption algorithms are private key encryption and public key encryption. A private key is also called a single key, secrete key, or symmetric key. A public key is also called an asymmetric key.
Private Key Encryption
In private key encryption algorithms, there is only one key. You use the same key value for both encryption and decryption. To ensure security, this key must remain secret and only the individuals involved can know the key. Kerberos is an example of an authentication protocol that uses private key algorithms.
The keys used in private key encryption are generally fairly small and the encryption algorithms are relatively fast to compute.
The major problem with private key encryption is distributing the key to everyone who needs it. Plus, the channel used to distribute the key must be secure. Compromising the key exposes all the information encrypted with that key.
With private key encryption, you need to change the keys fairly often.
You can also use private key schemes to provide digital signatures. However, digital signatures using public key encryption are more versatile and, in general, more secure.
Data Encryption Standard
The most commonly used private key algorithm is the Data Encryption Standard (DES). Developed by IBM, DES was made a U.S. Government standard in 1976. The algorithm is well known and widely implemented in commercial and government applications. Kerberos uses the DES algorithm to encrypt messages and create the private keys used during various transactions.
DES uses the same algorithm for encryption and decryption. The key can be just about any 64-bit number. Because of the way the algorithm works, the effective length is 56 bits. As far as is known, DES has not been broken and is generally believed to be secure.
The U.S. Government forbids export of hardware and software products that contain certain DES implementations. American exporters must adhere to this policy even though implementations of DES are widely available outside of the United States.
Public Key Encryption
Two keys, used together, are needed in public key algorithms. One key remains secret while the other becomes public. You can use each key for both encryption and decryption. Public key encryption helps solve the problem of distributing the key to users.
Some examples of public key encryption include using:
- Certificates to ensure that the correct public and private keys are being used in the transaction.
- Digital Signatures to provide a way for the receiver to confirm that the message came from the stated sender.
Only the user knows the private key and it must be kept secret. The user’s public key becomes publicly known and anyone communicating with the user can use it.
Plaintext — which is human-readable text — that is encrypted with the private key can be deciphered with the corresponding public key. In addition, plaintext encrypted with the public key can be deciphered with the corresponding private key.
Many applications of public key encryption require that when information is encrypted with a private key, the receiver can learn the corresponding public key. Once the public key is known, the receiver can decipher the information.
The best known public key encryption algorithm is RSA, named after its inventors, Rivest, Shamir, and Adleman. Another algorithm is Algomal.
All public key algorithms have some disadvantages. The encryption and decryption algorithms use large keys, often 100 or more digits. Large keys use substantial computing overhead that makes implementation rather slow. However, you can resolve key management and computing overhead problems by using smart cards and fast machines.
In addition, most public key encryption algorithms, at least in the United States, are based on patented technologies. This implies that vendors must pay royalties to whoever created the algorithms. In one way or another, that cost is passed on to the customer. Because these algorithms are patented, it is unlikely that public domain implementations will exist.
Certificates
Certificates issued by a Certification Authority ensure that a public key belongs to the user who claims to own it. The Certification Authority has its own private and public keys.
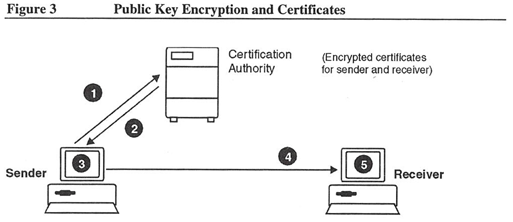
In a certificate-based public key system, the Certification Authority assigns a unique name to each user and issues them a certificate. The certificate issued by the Authority consists of the user's unique name and public key and is encrypted with the authority's private key. Suppose you need to send private information to someone and want to ensure that only that person can read the information. To do this, you need to encrypt the information with the receiver's public key. (See Figure 3). To do this you:
- Request a copy of the receiver's certificate from the Certification Authority.
- Obtain the receiver's encrypted certificate from the Certification Authority.
- Decrypt the certificate using the Certification Authority's public key. This exposes the receiver's public key.
- Encrypt your message using the receiver's public key then send the message.
The certificates verify which public key belongs to which user; they don’t contain any secret information. Users can keep certificates in open databases accessible to anyone.
A certificate has a finite lifetime, usually measured in months or years. When the certificate expires, the Authority needs to remove it from any public directories it maintains. However, the Authority should keep a secure copy of the certificate to resolve any disputes that might arise.
Digital Signatures
Handwritten signatures on documents are considered proof of authorship, ownership, or identity. Handwritten signatures can be unique and unforgeable. Both the signature and the document are physical things, which the signer cannot repudiate.
In computer communications, documents are easily modified after they are signed. Also, signatures can be copied from one document to another. In both cases, there is no evidence that the document was modified or the signature copied. This problem can be avoided by using a public or private key to encrypt the signature or the message.
Public key encryption algorithms let a receiver confirm that a message came from the stated sender. One way to do this is to use Digital Signatures. A Digital Signature is distinct for each specific transaction. It cannot be forged. The message itself does not need to be confidential.
A Digital Signature (shown in Figure 4) consists of applying a one-way hash function to the message and then encrypting the hash with the sender’s private key. A one-way hash function:
- Is very difficult or impossible to compute in the opposite direction.
- Maps values from a large domain into a smaller one. This means that the Digital Signature sent over the network can be smaller than the message itself.
In this protocol, the sender and receiver agree beforehand upon the one-way hash and Digital Signature algorithm.

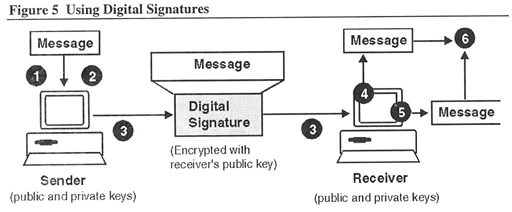
Using a Digital Signature to send and then verify a message involves actions by the sender and the receiver (see also Figure 5).
The sender needs to:
- Produce a one-way hash of a message.
- “Sign” the hash with the sender's Digital Signature (the private key).
- Encrypt the message with the receiver’s public key.
- Send the message and Digital Signature.
The receiver needs to:
- Apply the same hash function to the received message using its private key.
- Verify the signed hash with the sender's public key.
- Compare the sender's hash with the hash generated by the receiver.
If both hash functions match, the receiver knows that the message is from the stated sender and that no one has tampered with the message.