Network Security Defined - Network Security
What is Network Security?
Network security covers a wide range of issues. Such issues can include protecting the network and all associated devices, protecting the information stored in the system and traveling over the network, and protecting against users who don't have access permissions.
Many network users equate security with secrecy. Secrecy (also called confidentiality) is only one part of the network security puzzle. Indeed, there are three general types of network security: secrecy, integrity (accuracy), and availability. Depending on the organization's network environment, one type of security might be more important than another.
A secure network means that the systems on the network must be able to do all of the following:
- Prevent unauthorized users from accessing information.
- Prevent the system or users from corrupting information.
- Prevent unauthorized changes to information by users or intruders.
- Provide for system stability. The system should be able to recover quickly and completely from a software or hardware failure.
Providing Network Security
There are three basic steps that must be taken to provide network security. System Managers need to:
- Understand and identify possible threats to the network. A threat can be any kind of unauthorized access, corruption or compromise of data, or disruption of services.
- Determine the types of services needed to protect the system against threats.
- Assess the different methods available to implement the services.
The needs of individual network environments determine exactly which threats are worth protecting against and how expensive or disruptive that protection can be.
For example, a breach in network security in a bank could result in the loss of substantial amounts of money. A breach in network security in a research group could result in the loss of files, loss of time, and substantial inconvenience for the researchers. In both cases, system management would need to make a policy decision about the type of security service to implement.
The U.S. National Computer Security Center (NCSC) publishes the Trusted Computer System Evaluation Criteria (known as the Orange Book), which contains commonly used classifications for standalone computer systems. Trusted Network Interpretation (TNI), published by the same organization, interprets the policies in the Orange Book for systems attached to networks.
Identifying Security Threats
Various kinds of threats to network security can occur. Most are from unauthorized external users, but some can be from an internal source also. Common kinds include:
- A user pretending to be another user to gain access to the network or system
- A user observing (intercepting) the identity of another user and later pretending to be that user
- A user recording a communication and then repeatedly replaying that communication for unauthorized purposes
- An unauthorized user intercepting or manipulating another user's data during a communication; for example, reading and modifying information as it passes over the wire
- A user denying having taken part in all or part of a specific communication; for example, denying ever receiving a communication
- An unauthorized user denying service by interrupting, delaying, or preventing alegitimate user access to one or more services
- A third party observing the flow of traffic and deriving potentially damaging information from that observation.
On a network, an observer might be able to correctly interpret that a major activity is underway by observing the number, types, or frequency of messages on the network.
Identifying Security Services
After identifying potential threats to a network, you can determine the types of services to use to protect your network against the threats. You can use a variety of available services individually or in any combination. Some of these services include:
- Authentication services
These services are the single most important type of security service because they prove the identity of the user. There are a number of authentication variants. One is data origin authentication that determines the origin of data being received.
Other variants are single-entity authentication and mutual-entity authenticating. In single-entity authentication, one entity authenticates itself to another, such as when a user enters a password to log in.
In mutual entity authentication, both entities authenticate themselves to the other.
For example, when a user enters a password and the system to which the user logs in displays a password.
- Access control services
These services control what a user can do on the system, such as access certain resources. Access control services are usually implemented after users have proved their identity through authentication.
- Data confidentiality services
Unauthorized users are prevented from reading data by these services. They can be of two types: connection-oriented confidentiality services and connectionless confidentiality services.
Connection-oriented services guaranty the confidentiality of all data traveling across a specific connection. Connectionless services provide the confidentiality of a single message going across a network using a connectionless protocol.
It’s also possible to have selective field confidentiality for certain fields in a message.
- Data integrity services
These services guard against modification or replay of data as it travels across the network.
- Non-repudiation services
These service prevent denial of participation in a communication. You can do this by recording proof of origin, proof of receipt, or both.
- Traffic padding services
Illegal users are prevented from inferring information from the activities on the network when these services are in place. For example, false information can be transmitted during slack periods to prevent an illegal observer from guessing that network activity has changed.
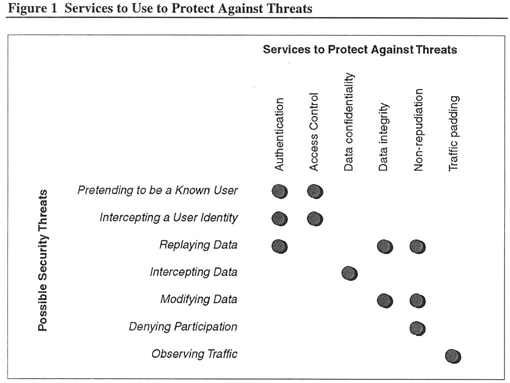
Matching Services with Security Threats
A single service can provide protection against a single threat to network security, however, it is more likely that a single service provides only partial protection against a threat. In some cases, more than one service is needed. Figure 1 summarizes the types of services you can combine to use against specific threats.
Methods to Provide Security Services
Security services can counter threats. The methods you use to implement security services do the actual work.
Different methods can frequently provide the same services. A single method can sometimes provide for multiple services. For example, you can implement access control in a number of different ways. A single method for encryption can be useful in a number of different services.
Some methods for providing security services include:
- Authentication exchange
This requires the exchange of single or mutual authentication information. The exchange protocols define what that information looks like. The Kerberos protocol (described later) is one example of Authentication exchange.
- Encryption
Control information or data is encoded in a form that only authorized persons or processes can read. There are two major types of encryption algorithms: private key and public key.
- Access control mechanisms
This method provides security by granting or denying designated users access to designated resources. A user could be granted access to one group of files and denied access to another. One way to grant or deny access to a user is to create one or more Access Control Lists (ACLs) for a resource. An ACL indicates which users are allowed access to certain resources and just how they can use the resources.
- Digital signatures
Frequently used to provide nonrepudiation services, Digital Signatures are similar to physical signatures on paper documents. This method typically uses encryption techniques to provide the Digital signature and for verification. A Digital signature can also provide data integrity services guaranteeing that the data in question was not modified.
- Traffic padding
Protects against traffic analysis. For example, false information can be inserted into the stream of transmitted data. In successful traffic padding mechanisms, attackers cannot tell the difference between false and real information.
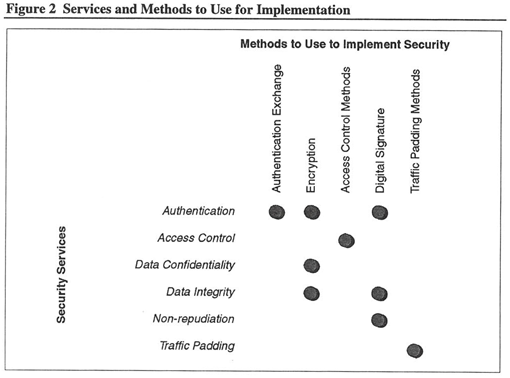
Matching Methods with Specific Services
Matching method types with security services is not always clear. Sometimes a single method might provide all or part of several services. Implementing a single service might require several methods.
Figure 2 shows the relationship between different services and the methods to implement the services. For example, you might use encryption to provide for authentication and data confidentiality.