TCP/IP Defined - TCP/IP Protocols
An internet is a virtual network that allows users to communicate with all connected hosts as if the hosts were part of the local network. All details of the network are hidden from the user. The basis on which this virtual network exists is the TCP/IP protocol suite. These protocols establish the formats and the rules that must be followed for information to be exchanged between systems.
The TCP/IP Protocol Suite
The TCP/IP protocol suite is easily conceptualized in layers. TCP/IP consists of three layers of services that rest on a layer of hardware, as shown in Figure 9.
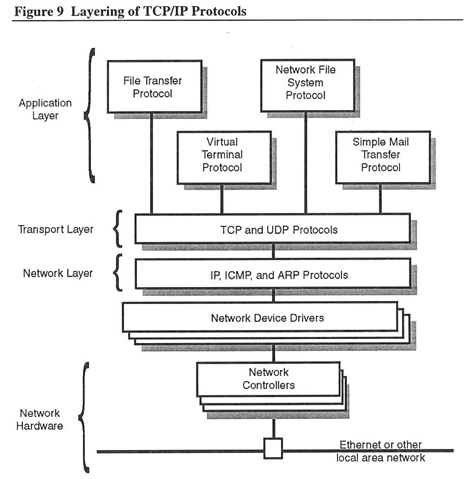
When a packet is transmitted over an internet, it passes through all the TCP/IP layers. Each layer adds its own header to the packet. The header includes control information related to the service provided by that layer. The layers consist of the:
- Network layer — Provides the packet delivery service across the network hardware interface for the host layer
- Transport layer — Provides the reliable data transport service to the application layer
- Application layer — Provides services to the user, including remote terminal login, file transfer, network file access, and electronic mail
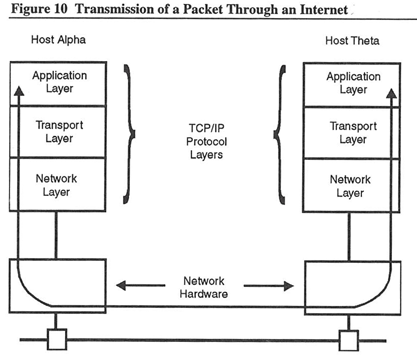
When a packet reaches its destination, it passes up through the layers. Each layer removes its header information before passing the packet to the next layer. Figure 10 shows the transmission path of a packet on an internet.
Network Layer Protocols
The network layer protocols provide a connectionless packet delivery service. A packet is the unit of transfer for a physical network. “Connectionless” describes the packet treatment: all packets are treated as separate entities. Network layer protocols provide efficient packet delivery by managing the addressing and routing of packets. The Internet Protocol (IP) provides the network layer protocol for TCP/IP.
Internet Protocol
The Internet Protocol (IP) is the foundation of TCP/IP. It sends and receives packets of information over the physical network. IP calls the packet a datagram. Each datagram includes its source and destination addresses, control information, and any actual data passed from or to the host layer. The IP datagram is the unit of transfer of an internet.
IP provides the mechanism by which hosts and gateways are able to route internet datagrams. IP routing is based on the destination address of each datagram. When IP receives a datagram, it checks the destination network number and a routing table. This routing table contains the addresses of known destination networks, gateways, and hosts. IP delivers datagrams with local internet addresses directly. It forwards datagrams with nonlocal addresses to their next destination based on the routing table information.
IP also monitors the size of the datagrams it receives from the host layer. If the datagram exceeds the length of the packet the physical network is capable of sending, IP fragments the single datagram into datagrams of lengths that are manageable by the underlying network hardware. The IP layer on the destination host reassembles the fragmented datagrams into the original single datagram before passing it to the higher level protocols.
IP requires that the higher level (transport or application layer) protocols reliably handle the data.
Internet Control Message Protocol
Although considered an independent protocol, the Internet Control Message Protocol (ICMP) performs an integral function of IP. ICMP allows hosts and gateways to exchange information about the communications environment of the internet. For example, ICMP can allow a gateway to inform a host of a more efficient route. ICMP information is encoded in the IP datagram.
Address Resolution Protocol
The Address Resolution Protocol (ARP) provides an address conversion function. A host can have a hardware address that is unrelated to its internet address. ARP provides a method of mapping internet addresses to hardware addresses. You use ARP most often in hosts connected to Ethernet networks.
Reverse Address Resolution Protocol
Diskless machines use the Reverse Address Resolution Protocol (RARP) to find their IP addresses from a server before they can communicate using TCP/IP.
Transport Layer Protocols
The transport layer protocols provide the data transport services to the application layers. The Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) form the bridge between the user or application programs (such as an electronic mail facility) and the lower level protocols (such as IP).
A primary function of the transport layer protocols is multiplexing. This term refers to directing message traffic to abstract delivery points called ports. When a host is running several application programs at once, the transport layer protocols direct incoming datagrams to the appropriate port so that they can reach the correct application program. Multiplexing allows many applications to access an internet at the same time.
User Datagram Protocol
The User Datagram Protocol (UDP) is a transaction-oriented protocol that transports data to or from the application layer. UDP requires very little overhead because it provides no protection against datagram loss or duplication. Applications that require orderly and reliable data transport should use the Transmission Control Protocol (TCP).
Transmission Control Protocol
The Transmission Control Protocol (TCP) provides reliable, process-to-process data transport by supplying the error checking facilities that IP or UDP do not provide.
TCP is a stream-oriented protocol. TCP guarantees that large amounts of data are transferred in order, so that the destination host receives all data in the same order as the source host sends it. TCP also guarantees that data is neither duplicated nor lost between the source and destination hosts.
Application Layer Protocols
The application layer protocols represent the highest level in the protocol layering model. These protocols convey the user request to the transport layer. They provide the internet services, such as file sharing, mail transfer, and remote terminal login.
The application protocols are often described in terms of the client-server model. This model views the local host as a client that initiates a networking request. The remote host, or server, then provides the service to the client. When referring to software that implements the TCP/IP application layer protocols, a client utility initiates a request, and a server process provides the service to the client utility.
The user on the local host typically invokes a client utility, such as TELNET or FTP, that initiates the networking request. The client utility contacts the server process on the remote host. The server process usually performs the network service without user intervention.
For example, a user on host Homer invokes the client-FTP utility and requests that it open a connection with host Plato. The server-FTP process on Plato answers the request, thereby establishing a connection, and is now ready to service file transfer requests. The user on Homer enters commands "directly" to Plato to, for example, list directories or to rename, delete, or transfer files.
File Transfer Protocol
The File Transfer Protocol (FTP) allows a user to log in to a remote host and perform file operations. FTP file operations include listing remote directories, copying files to or from the remote host, and renaming or deleting remote files.
When a user invokes FTP on a local host, a client-FTP utility establishes a connection with the remote host's server-FTP process. The server and client use this first connection to pass information. When the client requests a file transfer, the server and client open a second connection over which to pass the data.
When client-FTP establishes a connection with a server, FTP requests a username and password before allowing the user access to the server host. This protects files by denying access to unauthorized users. FTP supports all popular file formats, including ASCII and binary.
The FTP protocol uses TCP for reliable data transport.
Network File System Protocol
The Network File System (NFS) protocol allows users to access remotely a server host's filesystem as if it were part of the user's local filesystem. A client user can issue requests to create or remove files and directories, look up files, transfer files, set attributes on files, read and write files, and more. The server host performs the file operation and returns the requested information or status.
The NFS protocol uses UDP for data transport. Users can optionally request FTP as the transport protocol.
Simple Mail Transfer Protocol
The Simple Mail Transfer Protocol (SMTP) is an electronic mail facility that transfers mail messages between a client and server hosts.
SMTP is a store-and-forward mail system. When the client-SMTP utility tries to deliver mail but finds the server host unavailable, SMTP stores the mail at the client host. SMTP periodically attempts mail delivery until the server host can accept the mail. Furthermore, SMTP provides end-to-end reliability.
The client host keeps a copy of the mail message until the server host successfully receives the message.
The SMTP protocol uses TCP for reliable data transport.
TELNET or Virtual Terminal Protocol
TELNET (also known as the Remote Login Protocol) allows a user at a client host to interactively log in to a server host.
TELNET defines a device called a network virtual terminal (NVT). The NVT provides a standard network-wide representation of a terminal. This implies that the client and server have an agreed upon convention for how a terminal appears over the network.
TELNET also allows the client and server to negotiate options that can enhance their communications. By agreeing on certain options, TELNET clients and servers can, for example, change the format of the data they exchange from ASCII to binary.
The TELNET protocol uses TCP for reliable data transport.