2. NETCU Commands
This chapter contains a detailed description of each NETCU command. The commands are in alphabetical order.
The commands are summarized by category in Chapter 1. That chapter also describes how to run NETCU and how to send NETCU output to a file.
The descriptions include the command:
· Purpose and any suggestions or restrictions that apply
· Format
· Parameters (if any)
· Qualifiers (if any)
· Examples, when possible
ADD ACCESS_LIST
Controls incoming access restrictions for a remote host. Incoming access restrictions affect only TCP connections for servers the master server process starts. Requires OPER privilege.
Define a service using the ADD SERVICE or MODIFY SERVICE command with the /ACCESS_LIST qualifier that points to the appropriate list number. The access list should be defined in SERVERS.COM.
Format
ADD ACCESS_LIST list condition ia [mask]
Parameters
list
Number of the incoming access restrictions list (1 to 65535).
condition
Condition of permitting or denying access. Valid keywords are PERMIT and DENY.
Any host you enter on the PERMIT list can access services. TCPware denies services to all other hosts. Use the DENY parameter when:
· You grant a network or group of hosts access to services, and
· You want to deny one or more hosts within the network or group from access to services
TCPware places (and honors) DENY entries before PERMIT entries except when there are duplicate host or network entries with a PERMIT that has a more restrictive mask, in which case the PERMIT entry comes first.
ia
Internet address of the network or host you enter on the list.
mask
Internet address mask. Specifies which bits are used when matching hosts against the incoming access list. TCPware uses the bits set when matching hosts against the ia. If you omit mask and the host portion of the ia is 0, TCPware uses the network or subnet mask. If the host portion is not 0, TCPware uses 255.255.255.255, where it matches the entire Internet address against ia.
Qualifier
/MESSAGE=”text”
Text message sent over the connection when TCPware denies access. Place the text in quotation marks (" "). Define one message for each incoming access list. If a message previously exists, the new text replaces it.
The message you define affects all hosts to which the specified list denies access. If omitted, TCPware closes the connection if the list denies the host access.
The below table lists special characters you can use that have special meaning in the message.
|
Use this character... |
In place of this character... |
|
\\ |
\ |
|
\r |
carriage return |
|
\n |
line feed |
|
\t |
tab |
|
\0 |
NULL |
Examples
1. Denies host 192.168.95.6 access to the server associated with list 56. Any host denied access by list 56 receives the message
550 You are not authorized to have access to this host
followed by a line feed and carriage return.
ADD ACCESS_LIST 56 DENY 192.168.95.6 /MESSAGE="550 You are not authorized to gain access to this host.\n\r"
2. Permits hosts on network 192.168.95.0 access to the server associated with list 56.
ADD ACCESS_LIST 56 PERMIT 192.168.95.0
3. Permits all hosts on network 172.16 access to the server associated with list 1203.
ADD ACCESS_LIST 1203 PERMIT 172.16.0.0 255.255.0.0
ADD ARP
Adds an entry to an Address Resolution Protocol (ARP) table. Each ARP table entry consists of an internet address paired with a physical address. Requires OPER privilege.
|
Note: You do not need to use this command under normal circumstances. ARP maps internet addresses to physical addresses automatically. Use this command in rare instances when a particular host does not support ARP.
|
Format
ADD ARP destination-ia physical-address
Synonym
SET ARP destination-ia physical-address
Parameters
destination-ia
Internet address or host name of the ARP table entry.
physical-address
Ethernet, FDDI, or HYPERchannel address of the host specified by the destination-ia.
The standard physical address is in the format aa-bb-cc-dd-ee-ff, where for HYPERchannel physical addresses:
|
aa |
is the global network address domain |
|
bb |
is the global network address network |
|
cc |
is the physical unit |
|
dd |
is the logical unit |
|
ee |
is the trunks-to-try mask |
|
ff |
is the flags mask |
If ee-ff is 00-00, the value becomes FF-00.
If you do not specify an ARP server address when configuring the HYPERchannel line (HYP-n) and use the ADD ARP command to populate the ARP table, a TCPware host can act as an ARP server. A TCPware host responds to ARP requests it receives for addresses in the ARP table that you add using the /PUBLISH qualifier.
Qualifiers
/LINE=line
Line id of the ARP table where you want NETCU to place the entry. When not specified, NETCU determines the ARP table based on the internet address.
You must specify the /LINE qualifier when the internet address is not a local address.
/LOCK
Prevents ARP messages from changing the value of the physical address.
/PERMANENT
Makes the entry permanent in the ARP table. Without /PERMANENT, the entry may disappear from the ARP table if:
· The host does not receive a datagram within 10 minutes that has the destination-internet-address/ physical-address pair
· The ARP table is full and the entry is the oldest entry in the table
If you enable Reverse Address Resolution Protocol (RARP) support for an Ethernet or FDDI line, TCPware only responds to RARP requests for entries marked /PERMANENT.
/PUBLISH
The local host responds to ARP requests for the specified internet address.
Example
Places an entry in the ARP table for line QNA-0 (/LINE=QNA-0) that defines the Ethernet address for host ALPHA. This entry is permanent (/PERMANENT).
ADD ARP ALPHA AA-02-04-06-08-10/PERMANENT/LINE=QNA-0
ADD EXPORT
Adds an entry to the EXPORT database that lets the NFS server export the server filesystems to a remote NFS client. Users at the NFS client can then mount the server filesystems. Requires write access to the TCPWARE:NFS_EXPORT.DAT file. The EXPORT database is dynamic. Entries you add to the database become valid immediately. You do not need to restart the server.
If you are adding entries to the EXPORT database for the first time, read the EXPORT Database section in Chapter 14 of the TCPware Management Guide.
Format
ADD EXPORT "nfs-path" vms-directory
Parameters
"nfs-path"
NFS-style pathname used to reference the exported directory. Typically expressed as a UNIX-style pathname. Enclose in quotation marks (" ").
Although nfs-path can be arbitrary, it usually reflects the actual OpenVMS directory path. The NFS client user must refer to the same nfs-path in naming the mount point.
vms-directory
Directory on the local OpenVMS server that you want to export. The directory must include the device specification, as in the following example:
$DISK1:[SALES.RECORDS]
When you export a directory, the NFS client user can potentially have access to all files and directories below the export point. The device you export should be a "public" device. The server does not implement volume protection. Also, the server only supports Files-11 ODS-2 structure level disks.
Qualifiers
|
Note: Many of the following qualifiers are specific to applications running on certain hosts. In these cases, it is critical to use the /HOST qualifier in combination with these qualifiers.
|
/HOST=(host[,host …])
Only specified host(s) can have access to the exported OpenVMS directory. NETCU allows either host names or internet addresses. Use the parentheses only if you specify a list of hosts (separated by commas). If you omit /HOST, any host can mount the exported directory.
/CONVERT={STREAM_LF | STREAM_CRLF}
/NOCONVERT
/CONVERT converts files on reads
to either STREAM_LF (the default) for UNIX systems or STREAM_CRLF for PC
systems.
/NOCONVERT disables this conversion and must be
specified when using the server together with TCPware’s NFS client.
/EXPLICIT_MOUNT
/NOEXPLICIT_MOUNT
/EXPLICIT_MOUNT prevents users
from subsequently mounting subdirectories of the mount point.
/NOEXPLICIT_MOUNT (the default) allows subdirectory
mounts.
/FILENAME={ SRI | ODS5 | PATHWORKS | PATHWORKS_CASE }
Uses the SRI International, or ODS5, or PATHWORKS filename
mapping schemes.
SRI is the default scheme between UNIX and OpenVMS
systems.
ODS5 uses minimal mapping to get around ODS-5 file
naming restrictions. If the disk or system doesn’t support ODS-5, it falls
through to SRI.
PATHWORKS specifies non-case-sensitive filename
mapping.
PATHWORKS_CASE specifies case-sensitive filename
mapping.
/HIGHEST_VERSION
/NOHIGHEST_VERSION
/HIGHEST_VERSION returns only the highest version of files in directory requests. /NOHIGHEST_VERSION (the default) does not. All file versions still exist in either case.
/PRIVILEGED_PORT
/PRIVILEGED_PORT requests that incoming requests originate from privileged ports only.
/PROXY_CHECK
/PROXY_CHECK specifies that mount requests only originate from users having mappings in the PROXY database.
/RFM=option
Record format (RFM) of newly created files. The options are STREAMLF, STREAMCR, STREAM, FIXED, and UNDEFINED.
/SERVER_ACCESS
/NOSERVER_ACCES
/SERVER_ACCESS requests the
server to do access checking.
/NOSERVER_ACCESS (the default) requests that both
the server and client do the checking.
/SUPERUSER_MOUNT
Requests that only the superuser can mount a file system.
/VERSION={ DOT | SEMICOLON (default) | ALL | HIGHEST }
DOT changes the file version
display for exported filesystems to file.ext.version
(a dot) for UNIX compatibility instead of the usual file.extension;version
(a semicolon).
SEMICOLON (default) uses the regular semicolon.
ALL exports files with version numbers intact
rather than the default of leaving the highest numbered version unnumbered.
HIGHEST is a synonym for /HIGHEST_VERSION.
Do not use DOT with SEMICOLON.
/WRITE
/NOWRITE
/WRITE (the default) requests
that the client have read-write access to the filesystem.
/NOWRITE requests that the client have read access
only.
Example
Exports the directory SALES.RECORDS on device $DISK1: as path /vax/records to hosts ORCHID and ROSE. Any subdirectories below SALES.RECORDS are also accessible. However, hosts ORCHID and ROSE cannot have access to or mount directories above SALES.RECORDS or other SALES subdirectories.
ADD EXPORT “/vax/records” $DISK1:[SALES.RECORDS] /HOST=(ORCHID,ROSE)
ADD GROUP
Adds an entry to the NFS GROUP database that associates an OpenVMS user with an NFS group or list of groups. Requires SYSPRV privilege and write access to the TCPWARE:GROUP.DAT file.
If the GROUP database does not exist, use the CREATE GROUP command first to create an empty one. Use the REMOVE GROUP command to remove a group from the database.
|
Note: The GROUP database is static. Use the REL command when you modify it.
|
Format
ADD GROUP nfs-group vms-identifier
Parameters
nfs-group
NFS group number found in the /etc/group file on the server. For example, if the users group appears in the /etc/group file as:
users:x:15:
use 15 as the nfs-group.
vms-identifier
Associates either an OpenVMS rights identifier or UIC (or wildcarded UIC) with the NFS group. Only associate one vms-identifier per NFS group. Use either of the following formats to enter the value:
|
Format |
Description |
|
"Name" |
OpenVMS rights identifier or username |
|
"Value" |
UIC value in [group,member] or %Xnnnnnnnn format; you can use wildcard entries such as [200,*]. |
"Name" and "value" correspond to the columns associated with entries in the OpenVMS rights database. To have access to this database, use the commands:
$ SET DEFAULT SYS$SYSTEM
$ RUN AUTHORIZE
UAF> SHOW/IDENTIFIER
*
For example, the following line may appear in the rights database:
Name Value
Attributes
----- ----- ----------
USER [000200,000200]
Qualifier
/HOST=(host[,host...])
Server host(s) on which the group identification is valid. If omitted, any remote host is valid for the group. /HOST accepts either host names or internet addresses. Use the parentheses with multiple host entries.
Examples
1. Associates NFS group number 15 on server host IRIS with the "value" [200,*], meaning "any user in group 200."
NETCU> ADD GROUP /HOST=IRIS
_Group: 15
_Identifier: [200,*]
The nfs-group number derives from the entry in the /etc/group file on the server for the users group:
> cat /etc/group
staff:*:10:
users:*:15:
2. Associates NFS group number 15 with the OpenVMS rights identifier, USERS. As in the above example, the nfs-group number derives from the entry in the /etc/group file on the server. Assuming that the USERS rights identifier exists in the rights database, any user granted this identifier would be in the group corresponding to GID 15 in NFS.
NETCU> ADD GROUP 15 USERS
The resulting ADD GROUP entry would appear in the GROUP database as follows:
NFS GROUP Database V6.1 Copyright (c)
Process Software
Group Name Value Host(s)
----- ---- ----- ------
15 USERS %X8001000C
ADD MULTICAST_GROUP
Adds a multicast host group address to the table of joined addresses for the interface or all interfaces. Once you add a multicast group address to an interface, applications can receive datagrams sent to that address. Requires OPER privilege.
Format
ADD MULTICAST_GROUP internet-address
Parameter
internet-address
Internet address or host name of the multicast host group address.
Qualifier
/LINE=line-id
Line ID of the interface on which to add the address. If omitted, TCPware adds the address to all active interfaces.
Example
Adds the all-routers multicast address (224.0.0.2) to all active interfaces. Once added, applications receive datagrams sent to the multicast address.
NETCU> ADD MULTICAST_GROUP 224.0.0.2
ADD PROXY
Registers an NFS or remote user as an OpenVMS username in the NFS PROXY database. Requires SYSPRV privilege and write access to the TCPWARE:NFS_PROXY.DAT file.
|
Note: If you omit the /CLIENT or /SERVER qualifier, or do not define the TCPWARE_NFS_DYNAMIC_PROXY logical accordingly, you must use the RELOAD PROXY command to reload the database. (For details, see Reloading the PROXY Database in Chapter 14 of the TCPware Management Guide.)
|
Format
ADD PROXY vms-username
Parameter
vms-username
OpenVMS username to which you want to map an NFS user ID. The username must appear as in the OpenVMS User Access File (SYSUAF.DAT).
Qualifiers
The /HOST, /UID, /GID, or /NFS qualifiers make the PROXY entry more restrictive. When you omit a qualifier, NFS interprets it as a wildcard. For example, the command ADD PROXY SMITH/UID=210 creates an entry that lets a user with UID=210, but with any GID and from any host, use OpenVMS username SMITH.
/HOST=(host[,host...])
Host(s) from which the UID/GID identification is valid. Specify at least one host name. If omitted, NETCU allows any remote host with the matching identification.
/HOST accepts either host names or internet addresses. Use parentheses for multiple hosts.
/UID=uid
User’s ID (UID). If omitted, NETCU accepts any UID for the vms-username.
/GID=gid
User’s group ID (GID). If omitted, NETCU accepts any GID for the vms-username.
/CLIENT
/CLIENT notifies the client to immediately update its loaded PROXY database with an entry for vms username. This overrides any default action specified using the TCPWARE_NFS_DYNAMIC_PROXY logical.
/SERVER
/SERVER notifies the server to immediately update its loaded PROXY database with an entry for vms-username. This overrides any default action specified using the TCPWARE_NFS_DYNAMIC_PROXY logical.
Examples
The following examples range from most restrictive to least restrictive:
1. Registers a user with UID=210 and GID=5 at host ROSE to OpenVMS username SMITH for the NFS server only.
NETCU> ADD PROXY SMITH /UID=210 /GID=5 /HOST=ROSE /SERVER
2. Registers a user with UID=210 and GID=5 to OpenVMS username SMITH and dynamically reloads the PROXY database on both the client and server.
NETCU> ADD PROXY SMITH /UID=210 /GID=5 /CLIENT /SERVER
3. Registers any user with GID=5, any UID, and at any host to OpenVMS username JONES.
NETCU> ADD PROXY JONES /GID=5
4. Registers any user from host ORCHID to OpenVMS username JONES.
NETCU> ADD PROXY JONES /HOST=ORCHID
ADD ROUTE
Adds an entry to the routing table. Requires OPER privilege. (See also REMOVE ROUTE.)
Format
ADD ROUTE destination-ia {line | gateway-ia}
Synonym
SET ROUTE destination-ia {line | gateway-ia}
Parameters
destination-ia
Internet address or host name of the destination host or network. Specify 0.0.0.0 to add a default gateway or use the SET GATEWAY command.
line
Line ID of the direct route interface. If you specify a value for line, you cannot specify a gateway-ia.
gateway-ia
Internet address or host name of the gateway for the host or network (see the /GATEWAY qualifier below).
Qualifiers
/GATEWAY
Datagrams sent to the gateway. Do not use if specifying a line ID. If omitted, TCPware sends the datagrams to the destination IP address over the interface specified by line.
{/HOST | /NETWORK}
Use either one of these qualifiers to specify the type of route.
/HOST creates a host route for the host destination-ia identifies. /NETWORK creates a network route that leads to the network destination-ia identifies.
If you omit both, TCPware determines the type of route by looking at the host number part of destination-ia. If the host number is zero (0), TCPware assumes the route is a network route.
/LOCK
Disables ICMP redirect messages from changing the specified route.
/MASK=mask
Internet address mask for the Classless Inter-domain Routing (CIDR) protocol. The mask specifies the bits to use for the network portion of a mask. Thus the traditional network masks would be specified as:
Class A Network 255.0.0.0 Class B Network 255.255.0.0 Class C Network 255.255.255.0
If the mask is omitted, the destination address is derived by first checking interfaces for the same network number and, if one is found, the mask for that interface is used. Otherwise, the address is examined to determine if it is Class A, B, C, D, or E and a mask is created based on the class.
Network routes are sorted such that the routes with the most restrictive mask are searched before routes with a less restrictive mask. For example, a route with mask 255.255.255.0 is searched before a route with mask 255.255.0.0.
Do not create noncontiguous subnet masks. For example, a mask of 255.0.255.0 is not allowed.
Examples
1. Places a new route in the local host’s routing table. This route indicates that any traffic for network 172.16.10.0 (/NETWORK) must use gateway 172.16.1.5 (/GATEWAY). /LOCK indicates that an ICMP redirect message cannot modify this route.
NETCU> ADD ROUTE 172.16.10.0 172.16.1.5/NETWORK/GATEWAY/LOCK
2. Adds a host route to the routing table (/HOST) and directs all datagrams for host 172.16.4.3 to gateway 172.16.1.16 (/GATEWAY).
NETCU> ADD ROUTE 172.16.4.3 172.16.1.16/HOST/GATEWAY
3. Adds a route for the directly connected 172.16 network through the QNA-0 line.
NETCU> ADD ROUTE 172.16.0.0 QNA-0
4. Adds a default route to gateway 172.16.0.5 (equivalent to SET GATEWAY 0.0.0.0)
NETCU> ADD ROUTE 0.0.0.0 172.16.0.5/GATEWAY
ADD SECONDARY
Adds an additional internet address recognized as a local address. Requires OPER privilege.
|
Note: It may be necessary to add a route to have the address be reachable from the system that the address is added to.
|
Format
ADD SECONDARY ia
Parameter
ia
Internet address you want recognized as a local address.
Qualifier
/CLUSTER_LOCK
Instructs the VMScluster node to take the OpenVMS cluster-wide resource lock before adding the secondary address. If another node in the VMScluster holds the lock, the node queues for the lock and adds the address when it acquires the lock.
Examples
1. 192.168.95.101 becomes an additional local address for the interface address(es).
NETCU> ADD SECONDARY 192.168.95.101
2. The VMScluster node queues for a resource lock on the specified address. When the node takes the lock, it adds the address as an additional local address. This node acquires the lock when no other node holds the lock or the node that holds the lock releases it (such as when you shut down TCPware or the node).
NETCU> ADD SECONDARY 192.168.95.101 /CLUSTER_LOCK
ADD SERVICE
Instructs NETCP to start listening for connections on the specified port for the TCP or UDP protocol. Requires OPER privilege.
The TCPWARE:NETCP.LOG file logs each connection serviced. You can review this file for details on server errors and to monitor access and security violations.
Format
ADD SERVICE port protocol [image]
Parameters
port
Name or port number the service uses. Any service name or port number (except 0) defined in the TCPWARE:SERVICES. file.
protocol
Protocol that services the connection. The below table lists the valid values.
|
Enter this value... |
For... |
|
BG_TCP |
UCX-based servers on TCP |
|
BG_UDP |
UCX-based servers on UDP |
|
TCP |
TCPDRIVER-based servers |
|
UDP |
UDPDRIVER-based servers |
|
STREAM, DGRAM |
INETDRIVER-based servers |
If you use the BG_TCP or BG_UDP protocol values:
· You MUST specify /USERNAME=username and /INPUT=file. The file in this case is the name of the service’s startup command file. DO NOT use the image parameter. BG_TCP and BG_UDP run images from the startup command file only.
· Use only the default create_server_process internal action routine (see the /ROUTINE qualifier).
· DO NOT use the /OUTPUT or /ERROR qualifier.
image
File specification of the server you want executed. DO NOT use with BG_TCP or BG_UDP; use the /INPUT qualifier instead.
Qualifiers
/ACCESS_LIST=list
Incoming access restrictions list that controls which hosts have access to the server. Access restrictions affect TCP connections only.
If you define a list using this qualifier and do not add entries to the list, no hosts have access to this server. If the list contains entries, only the specified hosts have access. If you do not define an incoming access restrictions list, all hosts have access. The list value must be a number between 1 and 65535. 0 (no list) is the default.
Use the ADD ACCESS_LIST command to define list entries, the REMOVE ACCESS_LIST command to remove list entries, and the SHOW ACCESS_LISTS command to display entries.
/ADDRESS=ip-address
Adds the service for the specified address or hostname only. The default is 0.0.0.0.
/BACKLOG=number-backlogged-connections
Number of backlogged connections allowed for listening TCP services. If omitted, the value /BACKLOG=0 is used to indicate the default connection backlog (usually 128).
/INACTIVITY_TIMER=(TIME:minutes, CHECK_INTERVAL:minutes)
Sets an inactivity timer to kill idle NOLISTEN server processes (see the /NOLISTEN qualifier) for the TCP protocols (not used for UDP). A process is idle if there is no CPU activity for the number of minutes specified:
|
TIME:minutes |
Idle NOLISTEN processes are terminated after this amount of time (the default is infinite) |
|
CHECK_INTERVAL:minutes |
Checks for idle NOLISTEN processes each of these time intervals (the default is one minute) |
/LIMIT=number-servers
Maximum number of active servers that can reside on this host for the specified port(s). TCPware always uses /LIMIT=1 for UDP ports, regardless of what you enter. For example, to add a service on port 21 supporting one active server, use /LIMIT=1. NETCP waits for the current service to process before it listens for a new connection on the same port.
/LOG
/NOLOG
/LOG (on by default) starts logging of non-error events to the NETCP.LOG file. /NOLOG stops logging.
/NOLISTEN
Instructs NETCP to create the server process only when it detects a connection and not to hand off a socket or I/O channel. The default is to create the server process while listening for a connection. Use for the TCP protocols only (not for UDP).
/OPTION=option
Passes the process’s STREAM device (INETn:) created using one of the following options:
|
Option |
Description |
|
NONE (default) |
No special options |
|
HANDOFF |
Specifies to use a special handoff mechanism for passing the INETn: device to the created server process. |
|
[NO]KEEPALIVE |
Specifies whether to use keep-alives for a STREAM (INET) or BG_TCP service. By default, these services are NOKEEPALIVE. |
|
[NO]MULTITHREADED |
Specifies whether the BG_TCP server is a multithreaded one; if so, the master server, once started, does not listen for additional connections. By default, all servers are NOMULTITHREADED. |
|
SHARE |
Specifies that TCPware set the INET device for shared access, allowing another process to assign the channel. This option is primarily for WIN/TCP servers. |
TCPware ignores this qualifier if specified for non-STREAM services or services that do not use the create_server_process routine (see the /ROUTINE qualifier).
/ROUTINE=routine-name
NETCP internal action routine called when TCPware establishes a connection for the service. The below table lists the available routines.
|
Routine |
Purpose |
Protocol |
|
create_rservice |
Creates a Berkeley R service using NORMAL authorization checks |
STREAM |
|
create_rservice_secure |
Creates a Berkeley R service using SECURE authorization checks |
STREAM |
|
create_server_process |
Creates a detached process |
Any |
|
create_telnet_session |
Creates an interactive TELNET session |
TCP or STREAM |
|
ident_protocol |
Starts the IDENT Server |
TCP, UDP |
|
port_mapper_server |
Starts the Port Mapper |
TCP, UDP |
|
report_tclb_metric |
Creates a load balancing reply service |
UDP |
|
time_protocol |
Starts the Time service |
Any |
The default routine is create_server_process. This routine is appropriate for all user-written servers (and must be used for BG_TCP and BG_UDP protocol values).
/USERNAME=username
Use primarily with UCX devices (BG_TCP or BG_UDP protocol). If used with other devices, creates a detached process under the specified username.
Other Qualifiers
The following qualifiers are a subset of those the DCL RUN/DETACHED command uses. In most cases, OpenVMS provides default values for any qualifiers that you do not specify.
Always use /UIC and /PRIVILEGES to ensure that the new process has OPER privilege. All server processes should have at least TMPMBX and NETMBX privileges.
See the DCL documentation for complete details on each of the following qualifiers.
/ACCOUNTING
/NOACCOUNTING
/AST_LIMIT=quota
/AUTHORIZE
/NOAUTHORIZE
/BUFFER_LIMIT=quota
/DUMP
/NODUMP
/ENQUEUE_LIMIT=quota
/ERROR=filespec
/EXTENT=quota
/FILE_LIMIT=quota
/INPUT=filespec
/IO_BUFFERED=quota
/IO_DIRECT=quota
/JOB_TABLE_QUOTA=quota
/MAXIMUM_WORKING_SET=quota
/OUTPUT=filespec
/PAGE_FILE=quota
/PRIORITY=n
/PRIVILEGES=(privilege[,...])
/PROCESS_NAME=process-name
/QUEUE_LIMIT=quota
/RESOURCE_WAIT
/NORESOURCE_WAIT
/SERVICE_FAILURE
/NOSERVICE_FAILURE
/SUBPROCESS_LIMIT=quota
/SWAPPING
/NOSWAPPING
/UIC=uic
/WORKING_SET=quota
If you omit /INPUT, /OUTPUT, or /ERROR, NETCP supplies the TCP, UDP, or INET device name for the connection when it creates the process. If you use /PROCESS_NAME=process-name, NETCP uses up to 10 characters of the process-name. In addition, NETCP appends an underscore (_) and an ASCII decimal server number to the process-name to ensure that the process-name is unique.
Examples
1. Starts the DAYTIMED server for host BART only. Since the qualifiers do not specify any values, NETCU uses the OpenVMS default values.
NETCU> ADD SERVICE DAYTIME TCP TCPWARE:DAYTIMED /ADDRESS=BART
-
/PROCESS_NAME=DAYTIMED -
/NOACCOUNTING -
/NOAUTHORIZE -
/INPUT=NLA0: -
/OUTPUT=NLA0: -
/ERROR=NLA0: -
/UIC=[SYSTEM] -
/PRIVILEGES=(NOSAME,NETMBX,TMPMBX)
2. Starts the MYSERV service (defined in the TCPWARE:SERVICES. file) running over the BG_TCP (UCX) protocol, using the MYSERV_STARTUP.COM file, and creating a detached process under username SMITH.
NETCU> ADD SERVICE MYSERV BG_TCP -/INPUT=TK100:[MYSERV]MYSERV_STARTUP.COM /USER=SMITH
CHECK GATED CONFIGURATION
Checks the syntax of a GateD configuration file. If no input file is specified, TCPware checks the default configuration file, TCPWARE:GATED.CONF. This command does not affect a running GateD process.
Format
CHECK GATED CONFIGURATION [file]
Parameter
file
Name of the configuration file to check. If omitted, defaults to TCPWARE:GATED.CONF.
Example
Checks the syntax of a GateD configuration file called TEST.CONF located in the user’s current working directory.
NETCU> CHECK GATED CONFIGURATION TEST.CONF
CREATE EXPORT
Creates an empty NFS EXPORT database. Requires write access to the TCPWARE:NFS_EXPORT.DAT file.
|
Note: NFS server installations create an empty EXPORT database. Use this command to supersede an existing EXPORT database only.
|
Format
CREATE EXPORT
Example
Shows the current EXPORT database, overwrites it, and shows that the database is now empty.
NETCU> SHOW EXPORT
NFS EXPORT Database V6.1 Copyright (c) Process Software
Path Directory Host(s)
---- --------- -------
/usr $DISK1:[SALES.RECORDS] SIGMA
NETCU> CREATE EXPORT
NETCU> SHOW
EXPORT
%TCPWARE-NETCU-I-NOENTRIES, no EXPORT entries found
CREATE GROUP
Creates an empty NFS GROUP database. Requires write access to the TCPWARE:NFS_GROUP.DAT file.
|
Note: Client installation creates an empty GROUP database. Only use this command to supersede an existing GROUP database.
|
Format
CREATE GROUP
Example
Shows the current GROUP database, overwrites it, and shows that the database is now empty.
NETCU> SHOW GROUP
NFS GROUP Database V6.1 Copyright (c) Process Software
Group Name Value
Host(s)
----- ---- ----- -------
15 GROUP %X8001000B
15 GROUP_16 %X8001000E
NETCU> CREATE GROUP
NETCU> SHOW
GROUP
%TCPWARE-NETCU-I-NOENTRIES, no GROUP entries found
CREATE PROXY
Creates an empty NFS PROXY database. Requires write access to the TCPWARE:NFS_PROXY.DAT file.
|
Note: Client and server installation creates an empty PROXY database. Only use this command to supersede an existing PROXY database.
|
Format
CREATE PROXY
Example
Shows the current PROXY database, overwrites it, and shows that the database is now empty.
NETCU> SHOW PROXY
NFS PROXY Database V6.1 Copyright (c) Process Software
Username UID GID
Host(s)
-------- --- --- -------
BART 1116 15
MARGE 1115 15
LISA 1117 16
HOMER -2 -2
NETCU> CREATE PROXY
NETCU> SHOW
PROXY
%TCPWARE-NETCU-I-NOENTRIES, no PROXY entries found
DEBUG/IP
Displays information about IP datagrams sent and received over the network. Use this information to debug IP network problems. Requires LOG_IO privilege, along with either SYSPRV or BYPASS privilege.
The DEBUG/IP command displays the system time for the packet as mm:ss.cc (minutes, seconds, and hundredths of a second).
Press Ctrl/C to end the display and return to the NETCU prompt.
Format
DEBUG/IP
Qualifiers
/DATA=byte-count
Maximum number of data bytes to display (the default is 16 bytes).
/DECODE
Shows all IP packets in TCPDUMP output format. You can combine /DECODE with any other qualifier except /OCTAL and /DECIMAL, since TCPDUMP output is in hex format.
/HEADER
Displays the IP header in bytes. By default, TCPware does not display the header since the important information contained in it appears in a decoded format.
{/OCTAL | /DECIMAL | /HEXADECIMAL}
Displays the data bytes in octal, decimal, or hexadecimal format. Hexadecimal is the default, which also displays printable ASCII characters for the bytes
You can only specify one of these qualifiers.
/LINE=line-id
Displays IP datagrams for the indicated line only.
{/SIA | /LIA}=(ia[,mask])
For transmitted packets, displays only packets the specified local internet address(es) sends. For received packets, displays only packets the specified local internet address(es) receives. For example, you can use this on a system with multiple interfaces to capture traffic to and from any particular interface.
This flag is optional if only one interface exists on the local system. If you omit the mask value, the parentheses are optional.
{/DIA | /RIA | /FIA}=(ia[,mask])
For transmitted packets, displays only packets the specified internet address(es) receives. For received packets, displays only packets the specified internet address(es) sends.
If you omit the mask value, the parentheses are optional.
|
Note: For the /SIA (/LIA) and /DIA (/RIA, /FIA) qualifiers, if you do not specify the mask value, TCPware determines the mask based on whether the host number portion of the address is 0 or non-zero. If non-zero, the mask is 255.255.255.255. If zero, the mask is the address mask for the network.
|
/PROTOCOL=n
Displays only packets for the specified IP protocol.
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
Example
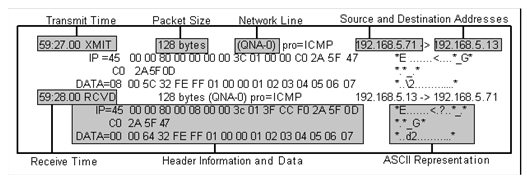
NETCU> DEBUG/IP/HEADER
Returns information such as the following about IP datagrams for all network connections:
DEBUG/TCP
Displays information about TCP segments sent and received over the network. Use this information to debug TCP network problems. Requires LOG_IO privilege, along with either SYSPRV or BYPASS privilege.
The DEBUG/TCP command displays the system time for the packet as mm:ss.cc (minutes, seconds, and hundredths of a second).
Press Ctrl/C to end the display and return to the NETCU prompt.
Format
DEBUG/TCP
Qualifiers
/DATA=byte-count
Maximum number of data bytes to display (the default is 16 bytes).
/DECODE
Shows all IP packets in TCPDUMP output format. You can combine /DECODE with any other qualifier except /OCTAL and /DECIMAL, since TCPDUMP output is in hex format.
/HEADER
Displays the TCP header in bytes. By default, TCPware does not display the header since the important information contained in it appears in a decoded format.
{/OCTAL | /DECIMAL | /HEXADECIMAL}
Displays the data bytes in octal, decimal, or hexadecimal format. Hexadecimal is the default, which also displays printable ASCII characters for the bytes. You can only specify one of these qualifiers.
{/SIA | /LIA}=(ia[,mask])
For transmitted packets, displays only packets the specified local internet address(es) sends. For received packets, displays only packets the specified local internet address(es) receives. For example, you can use this on a system with multiple interfaces to capture traffic to and from any particular interface.
This flag is optional if only one interface exists on the local system. If you omit the mask value, the parentheses are optional.
{/DIA | /RIA | /FIA}=(ia[,mask])
For transmitted packets, displays only packets the specified internet address(es) receives. For received packets, displays only packets the specified internet address(es) sends. If you omit the mask value, the parentheses are optional.
|
Note: For the /SIA and /DIA qualifiers, if you do not specify the mask value, TCPware determines the mask based on whether the host number portion of the address is 0 or non-zero. If non-zero, the mask is 255.255.255.255. If zero, the mask is the address mask for the network.
|
{/SPN | /LPN}=port
For transmitted packets, displays only packets the specified port number sends. For received packets, displays only packets you the specified port number receives.
{/DPN | /RPN | /FPN}=port
For transmitted packets, displays only packets the specified port number receives. For received packets, displays only packets the specified port number sends.
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
Example
NETCU> DEBUG/TCP
Returns information such as the following about TCP segments for all network connections:
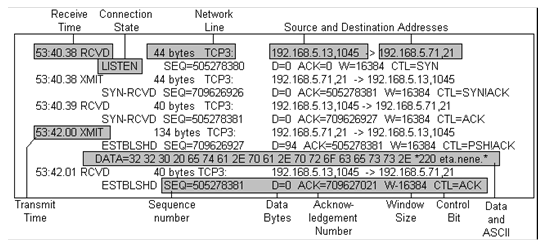
The system can display the following control bits after CTL=:
|
URG |
Urgent pointer |
|
ACK |
Acknowledgment; if set, the ACK field contains the value of the next sequence number the sender expects to receive |
|
PSH |
Push function |
|
RST |
Reset the connection |
|
SYN |
Synchronize sequence numbers |
|
FIN |
Finished connection: no more data from the sender |
DEBUG/UDP
Displays information about UDP datagrams sent and received over the network. Use this information to debug UDP network problems. Requires LOG_IO privilege, along with either SYSPRV or BYPASS privilege.
The DEBUG/UDP command displays the system time for the packet as mm:ss.cc (minutes, seconds, and hundredths of a second). Press Ctrl/C to end the display and return to the NETCU prompt.
Format
DEBUG/UDP
Qualifiers
/DATA=byte-count
Maximum number of data bytes to display (the default is 16 bytes).
/DECODE
Shows all IP packets in TCPDUMP output format. You can combine /DECODE with any other qualifier except /OCTAL and /DECIMAL, since TCPDUMP output is in hex format.
/HEADER
Displays the UDP header in bytes. By default, TCPware does not display the header since the important information contained in it appears in a decoded format.
{/OCTAL | /DECIMAL | /HEXADECIMAL}
Displays the data bytes in octal, decimal, or hexadecimal format. Hexadecimal is the default, which also displays printable ASCII characters for the bytes. You can only specify one of these qualifiers.
{/SIA | /LIA}=(ia[,mask])
For transmitted packets, displays only packets the specified local internet address(es) sends. For received packets, displays only packets the specified local internet address(es) receives. For example, you can use this on a system with multiple interfaces to capture traffic to and from any particular interface.
This flag is optional if only one interface exists on the local system. If you omit the mask value, the parentheses are optional.
{/DIA | /RIA | /FIA}=(ia[,mask])
For transmitted packets, displays only packets the specified internet address(es) receives. For received packets, displays only packets the specified internet address(es) sends. If you omit the mask value, the parentheses are optional.
|
Note: For the /SIA and /DIA qualifiers, if you do not specify the mask value, TCPware determines the mask based on whether the host number portion of the address is 0 or non-zero. If non-zero, the mask is 255.255.255.255. If zero, the mask is the address mask for the network.
|
{/SPN | /LPN}=port
For transmitted packets, displays only packets the specified port number sends. For received packets, displays only packets the specified port number receives.
{/DPN | /RPN | /FPN}=port
For transmitted packets, displays only packets the specified port number receives. For received packets, displays only packets the specified port number sends.
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
Example
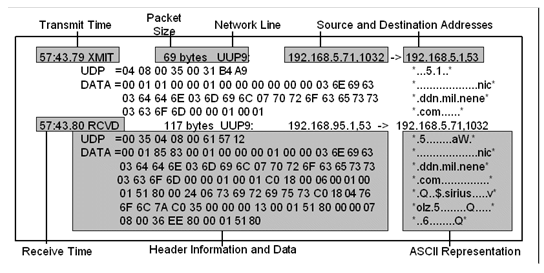
NETCU> DEBUG/UDP/HEADER/DATA=1000
Displays information about UDP datagrams for all network connections, includes the IP header information in bytes, and specifies the maximum number of data bytes to display (1,000), as in the following example:
DEFINE/KEY
Associates an equivalence string and a set of attributes with a key on the terminal keyboard. You must use the /KEY qualifier in this command.
Format
DEFINE/KEY key-name equivalence-string
Parameters
key-name
Name of the key you want to define.
The below table lists the key-names in the first column. The remaining three columns indicate the key designations on the keyboards for the three different types of terminals that allow key definitions. All definable keys on VT52 terminals are on the numeric keypad. On VT100-type terminals, you can define the # and % keys as well as all the keys on the numeric keypad.
You can define three types of keys on terminals with LK201 keyboards: keys on the numeric keypad, on the editing keypad (except the $ and ^ arrow keys), and on the function key row across the top of the terminal. You cannot define function keys F1 through F5.
The # and % keys and the F6 through F14 VT200 keys are reserved for command line editing. You must issue the DCL command SET TERMINAL/ NOLINE_EDITING before defining these keys. You can also press ^V to enable keys F7 through F14 (^V does not enable the F6 key).
|
Key-name |
LK201 |
VT100-type |
VT52 |
|
PF1 |
PF1 |
PF1 |
[blue] |
|
PF2 |
PF2 |
PF2 |
[red] |
|
PF3 |
PF3 |
PF3 |
[gray] |
|
PF4 |
PF4 |
PF4 |
n/a |
|
KP0,…,KP9 |
0,…9 |
0,…9 |
0,…9 |
|
PERIOD |
. |
. |
. |
|
COMMA |
, |
, |
n/a |
|
MINUS |
- |
- |
n/a |
|
ENTER |
Enter |
ENTER |
ENTER |
|
LEFT |
‹ |
‹ |
‹ |
|
RIGHT |
fi |
fi |
fi |
|
Find (E1) |
Find |
n/a |
n/a |
|
Insert Here (E2) |
Insert_Here |
n/a |
n/a |
|
Remove (E3) |
Remove |
n/a |
n/a |
|
Select (E4) |
Select |
n/a |
n/a |
|
Prev Screen (E5) |
Prev_Screen |
n/a |
n/a |
|
Next Screen (E6) |
Next_Screen |
n/a |
n/a |
|
HELP |
Help |
n/a |
n/a |
|
DO |
Do |
n/a |
n/a |
|
F6, …, F20 |
F6,…,F20 |
n/a |
n/a |
equivalence-string
String that you want to appear when you press the key. If the string contains spaces, enclose the equivalence string in quotation marks (" ").
Qualifiers
/ECHO
/NOECHO
/ECHO (the default) echoes the equivalence string on your screen after you press the key. /NOECHO does not echo the equivalence string on your screen. Do not use /NOECHO with the /NOTERMINATE qualifier.
/IF_STATE=(state-name,…)
/NOIF_STATE
/IF_STATE defines which if-state you establish with the /SET_STATE qualifier is in effect. If you omit /IF_STATE or use /NOIF_STATE (the default), TCPware uses the current if-state. See the /SET_STATE qualifier for details.
/LOCK_STATE
/NOLOCK_STATE
/LOCK_STATE specifies that the state set by the /SET_STATE qualifier remains in effect until explicitly changed. /NOLOCK_STATE (the default) specifies that the state set by /SET_STATE is in effect only for the next definable key that you press or for the next read terminating character that you type. Use /LOCK_STATE only with /SET_STATE.
/SET_STATE=(state-name,…)
/NOSET_STATE
/SET_STATE defines the if-state to use when you press the defined key. The state-name is any alphanumeric string. The parentheses are for establishing multiple states. By including several state-names, you can define a key to have the same function in all the specified states. If you omit /SET_STATE or use /NOSET_STATE (the default), the currently locked state is in effect.
/TERMINATE
/NOTERMINATE
/TERMINATE terminates the current equivalence string when you press the defined key. Terminating the string usually executes the string. /NOTERMINATE (the default) lets you create key definitions that insert text into command lines, after prompts, or into other text you type.
Example
Sets the F1 key on the keyboard to the SMITH SECRET”::[USERS] string, sets the state to 1, and locks the state for that definition.
NETCU> DEFINE/KEY F1 “““SMITH SECRET””::[USERS]” /SET_STATE=1/LOCK_STATE
DEFINE TIMEZONE
Specifies the local time zone name that was either previously compiled into TCPware or is a name from a selected time zone in the time zone database files.
Format
DEFINE TIMEZONE localzone
Parameter
localzone
The name of the local time zone; for example, MST.
Qualifiers
/LOG
Displays a list of the time zones that are loaded, and a list of the compiled-in zones that were selected but not loaded because they were compiled-in.
/SELECT=(rule1 [,rule2 [,…]])
Specifies a list of countries or time zones to load. Specifying a country loads all time zones in that country.
/FILES=(FILE1 [,FILE2 [,…]])
Specifies a list of files from which to load the time zone data. The default is TCPWARE:TIMEZONES.DAT. Locally-written rules are normally added to TCPWARE:TIMEZONES.LOCAL.
Example
1. This example defines the time zone to use as the United States local time zone MST.
NETCU> DEFINE TIMEZONE mst
2. This example defines the time zone to MST and loads Arizona time zone rules.
NETCU> DEFINE TIMEZONE mst/SELECT="us/arizona"
DISABLE FORWARDING
Disables forwarding of IP datagrams not destined for this host. Requires OPER privilege. TCPware disables forwarding by default. You should normally disable forwarding to prevent TCPware from routing datagrams between networks.
Format
DISABLE FORWARDING
Synonym
DISABLE GATEWAY
DISABLE REDIRECTS
Disables returning ICMP redirect messages to sending hosts. This can be set if this host is to act as a router. Requires OPER privilege. Disabling redirects is only valid if forwarding is also enabled through ENABLE FORWARDING. ENABLE REDIRECTS is the default if forwarding is enabled.
Format
DISABLE REDIRECTS
DUMP GATED STATE
Tells GateD to dump its internal state into a text file. If you omit the filename, the default is TCPWARE:GATED.DUMP.
|
Note: The NETCU processing of this command is completed before GateD finishes processing it.
|
Format
DUMP GATED STATE [file]
Parameter
file
Name of the file to which to dump. If omitted, defaults to TCPWARE:GATED.DUMP.
Example
Tells the GateD process to dump its internal state information to a file called TEMP.DUMP in the user’s current working directory.
NETCU> DUMP GATED STATE TEMP.DUMP
DUMP NAMED
These commands are used for debugging NAMED:
|
Commands |
Description |
|
DUMP NAMED CACHE |
Dumps the current contents of the NAMED cache to a file, TCPWARE:NAMED_DUMP.DB, in an RFC 883 format |
|
DUMP NAMED STATS |
Dumps the current NAMED statistics to the TCPWARE:NAMED.STATS and the TCPWARE:NAMED.MEMSTATS files |
Format
DUMP NAMED CACHE
DUMP NAMED STATISTICS
DUMP NAMED STATS
Examples
1. Dumping the NAMED cache to the TCPWARE:NAMED_DUMP.DB file:
NETCU> DUMP NAMED CACHE
%TCPWARE_NETCU-S-NORMAL, normal successful completion
; Dumped at Thu May 1
09:14:39 2021
;; ++zone table++
;95.168.192.in-addr.arpa (type 2, class 1, source NAMED.temp_sirius_rev)
; time=862478265,lastupdate=862396837, serial=237,
; refresh=86400, retry=600, expire=3600000, minimum=86400
; ftime=862396837, xaddr=[0.0.0.0], state=0041, pid=0
; z_addr[1]: [192.168.1.92]
; nene.com (type 1, class 1, source NAMED.HOSTS)
; time=0, lastupdate=862396105, serial=6002,
; refresh=0, retry=1800, expire=3600000, minimum=86400
; ftime=862396105, xaddr=[0.0.0.0], state=0041, pid=0
; 48.168.198.in-addr.arpa (type 1, class 1, source NAMED.REV)
; time=0, lastupdate=862321422, serial=91,
; refresh=0, retry=600, expire=3600000, minimum=86400
; ftime=862321422, xaddr=[0.0.0.0], state=0041, pid=0
; 0.0.127.in-addr.arpa (type 1, class 1, source NAMED.LOCAL)
; time=0, lastupdate=850919099, serial=6001,
; refresh=0, retry=600, expire=3600000, minimum=86400
; ftime=850919099, xaddr=[0.0.0.0], state=0041, pid=0
;; --zone table--
; Note: Cr=(auth,answer,addtnl,cache) tag only shown for non-auth RR’s
; Note: NT=milliseconds for any A RR which we’ve used as a nameserver
; --- Cache & Data ---
$ORIGIN .. 279304 IN NS D.ROOT-SERVERS.NET.
;Cr=answer [198.168.48.105]
279304 IN NS E.ROOT-SERVERS.NET.
;Cr=answer [198.168.48.105]
.
.
.
The NAMESERVER.LOG file shows the following SIGNAL entries:
%%%%%%%%%%%% NAMED 1-MAY-2021 10:55:57.73 %%%%%%%%%%%%
%TCPWARE_NAMED-I-SIGNAL, Request to dump current cache received.
%%%%%%%%%%%% NAMED 1-MAY-2021 10:55:57.77 %%%%%%%%%%%%
%TCPWARE_NAMED-I-SIGNAL, dumping nameserver cache
%%%%%%%%%%%% NAMED 1-MAY-2021 10:55:58.13 %%%%%%%%%%%%
%TCPWARE_NAMED-I-SIGNAL, nameserver cache dump completed
2. Dumps the current NAMED statistics in the NAMESERVER.LOG file, as
in the following example:
NETCU> DUMP NAMED STATS
%TCPWARE_NETCU-S-NORMAL, normal successful completion
%%%%%%%%%%%% NAMED 1-MAY-2021
10:55:57.72 %%%%%%%%%%%%
%TCPWARE_NAMED-I-SIGNAL, Request to dump statistics received.
%%%%%%%%%%%% NAMED 1-MAY-2021 10:55:57.73 %%%%%%%%%%%%
%TCPWARE_NAMED-I-STATUS, dumping nameserver stats
+++ Statistics Dump +++ (862478765) Thu May 1 09:26:05 2021
723 time since boot (secs)
723 time since reset (secs)
0 Unknown query types
++ Name Server Statistics ++
(Legend)
RQ RR RIQ RNXD RFwdQ
RFwdR RDupQ RDupR RFail RFErr
RErr RTCP RAXFR RLame ROpts
SSysQ SAns SFwdQ SFwdR SDupQ
SFail SFErr SErr
(Global) 0 1 0 0 0 0 0 0 0 0 0 0 0 0 0 1 0 0 0 0 0 0 0
[192.168.12.34] 0 1 0 0 0 0 0 0 0 0 0 0 0 0 0 1 0 0 0 0 0 0 0
-- Name Server Statistics --
--- Statistics Dump --- (862478765) Thu May 1 09:26:05 2021
%%%%%%%%%%%% NAMED 1-MAY-2021 09:26:05.87 %%%%%%%%%%%%
%%TCPWARE_NAMED-I-STATUS, done dumping nameserver stats
ENABLE FORWARDING
Enables the forwarding of IP datagrams not destined for this host. This is necessary if this host is to act as a router. Requires OPER privilege. TCPware disables forwarding by default. When you enable forwarding, the host receiving IP datagrams forwards them to another network if needed.
Format
ENABLE FORWARDING
Synonym
ENABLE GATEWAY
Qualifier
/ARP
Enables ARP reply messages for remote internet addresses (also referred to as PROXY ARP). The network sends a reply only if there is a known route to the target internet address of the ARP request.
ENABLE REDIRECTS
Enables ICMP redirects to notify sending hosts to redirect IP datagrams to another host. This can be set if this host is to act as a router. Requires OPER privilege. Enabling redirects is only valid if forwarding is also enabled through ENABLE FORWARDING. ENABLE REDIRECTS is the default if forwarding is enabled. To disable redirects, use the DISABLE REDIRECTS command.
Format
ENABLE REDIRECTS
EXIT
Saves the current configuration, if it has been modified, then quits. Exits NETCU and returns to the DCL prompt.
Format
EXIT
FIND ARP
Displays a single entry from an ARP table. ARP tables map internet addresses to physical hardware addresses for FDDI, Ethernet, and HYPERchannel interfaces. You can display the entire ARP table for a network device using the SHOW ARP command. For the format of the ARP table entries, see the SHOW ARP command.
Format
FIND ARP destination-ia
Parameter
destination-ia
Internet address or host name of the ARP table entry.
Qualifier
/LINE=line
Line ID of the ARP table where you want NETCU to locate the entry. You must use this qualifier if the internet address is not a local network address. If omitted, TCPware determines the ARP table based on the internet address.
Example
Finds the hardware (physical) address of the FLOWER.EXAMPLE.COM internet address.
NETCU> FIND ARP
_Internet address: FLOWER.EXAMPLE.COM
Internet Address Physical
Address Flags
---------------- ---------------- -----
192.168.5.1 AA-00-04-00-01-08
FIND PROXY
Locates and displays a single entry in the PROXY database. Requires read access to the TCPWARE:NFS_PROXY.DAT file.
On the client, use this command to find the UIC assigned a specific user.
On the server, use this command to determine which OpenVMS username the server uses when it receives a request from the specified UID, GID, and host name.
Format
FIND PROXY
Qualifiers
|
Note: You must specify all three of the following qualifiers.
|
/HOST=host-name
Host on which the user is valid. This qualifier is required.
/UID=uid
User’s ID (UID). This qualifier is required.
/GID=gid
User’s group ID (GID). This qualifier is required.
Example
Locates an OpenVMS username for an NFS user with UID=210, GID=5, at host ROSE.
NETCU> FIND PROXY /UID=210 /GID=5
/HOST=ROSE
NFS PROXY Database V6.1 Copyright (c) Process Software
Username UID GID
Host(s)
-------- --- --- -------
SMITH 210 15 ROSE
FIND ROUTE
The FIND ROUTE command displays an existing route from the routing table for a specified host or network.
Format
FIND ROUTE destination-ia
Parameter
destination-ia
The internet address or host name of the host or network of the routing table entry.
Example
Finds the routing table entry for the 192.168.5.21 host internet address.
The UNIL flag entry indicates that the route is "up" (functional), that it is a network (N) route, that the route is a network interface (I), and that someone locked the route (L) using the /LOCK qualifier. The number 2300 indicates that many datagrams have been transmitted using this route.
NETCU> FIND ROUTE
_Destination internet address: 192.168.5.21
Destination
Gateway Flags RefCnt UseCnt Line
----------- ------- _____ ______ ______ _____
192.168.5.0 192.168.5.21 UNIL 0 2300 SVA-0
FLUSH
Flushes the entire ARP table or routing table. Requires OPER privilege.
Format
FLUSH
Qualifiers
/ARP
Flushes the ARP tables and removes all but permanent entries. /NETWORK is an equivalent qualifier. Use the REMOVE command to remove a permanent ARP entry.
/LINE=line
Line ID of the ARP table to flush. If omitted, NETCU flushes all the ARP tables.
/ROUTE
Flushes the routing table by removing all non-interface routes. An interface route is for an actual network interface.
HELP
Brings up the NETCU online help. NETCU uses the OpenVMS interactive help facility. To exit the help facility, press Return until you return to the NETCU> prompt.
Format
HELP [topic]
Parameter
topic
(Optional) Topic for which you want help.
KILL CONNECTIONS
Resets the TCP connection on the specified device or the connections matching the internet address or port specification. Requires PHY_IO and either SYSPRV or BYPASS privileges.
Format
KILL CONNECTIONS [device | qualifier]
Specify either a device, or one or both qualifiers listed below.
Parameter
device
One of the following devices: TCPn, BGn, INETn.
When specifying a device, KILL CONNECTIONS kills active and listening connections for that device. TCPware resets the TCP connection and completes any pending QIOs with the SS$_THIRDPARTY status. When you omit the device, KILL CONNECTIONS kills only active connections (those not in a CLOSED or LISTEN state) that match the local or remote specification.
Qualifiers
/LOCAL=ia.port
Local address and port for incoming connections, in the format ia.port, where ia is the IP address or host name followed by a period, and port is the port number or service name. Use an asterisk (*) as a wildcard in place of ia or port.
/REMOTE=ia.port
Remote address and port for outgoing connections, in the format ia.port, where ia is the IP address or host name followed by a period, and port is the port number or service name. Use an asterisk (*) as a wildcard in place of ia or port.
Examples
1. Kills all outgoing TELNET (port 23) connections.
NETCU> KILL CONNECTIONS /REMOTE=*.23
2. Kills all outgoing connections to host NIC.NEAR.NET.
NETCU> KILL CONNECTIONS /REMOTE=NIC.NEAR.NET.*
3. Kills all incoming connections to any local IP address and port.
NETCU> KILL CONNECTIONS /LOCAL=*.*
LOAD GATED CONFIGURATION
Tells the GATED process to load a configuration file. If no file is specified, the default file TCPWARE:GATED.CONF is loaded.
|
CAUTION! If the GATED process detects an error in the configuration file being loaded, it stops running.
|
Format
LOAD GATED CONFIGURATION [file]
Parameter
file
Name of the configuration file to load. If omitted, defaults to TCPWARE:GATED.CONF.
Example
This example tells the GATED process to load a new configuration file called TEST_CONFIG.CONF from the system manager’s current working directory.
NETCU> LOAD GATED CONFIGURATION TEST_CONFIG.CONF
MODIFY SERVICE
Modifies information associated with an existing service. Requires OPER privilege.
Format
MODIFY SERVICE port protocol [image]
Parameters
port
Name or port number for the service to modify. Any service name or port number (except 0) defined in the TCPWARE:SERVICES. file. The service must be active.
protocol
Protocol to service the connection. The below table lists the valid values.
|
Enter This Value... |
For... |
|
BG_TCP |
UCX-based servers on TCP |
|
BG_UDP |
UCX-based servers on UDP |
|
TCP |
TCPDRIVER-based servers |
|
UDP |
UDPDRIVER-based servers |
|
STREAM, DGRAM |
INETDRIVER-based servers |
image
File specification of the server you want executed. DO NOT use with BG_TCP or BG_UDP; use the /INPUT qualifier instead.
Qualifiers
See the ADD SERVICE command for valid qualifiers. Remove an access list for a service by specifying /ACCESS_LIST=0.
Examples
The commands in this example:
· Add access list number 1, permitting access for the host given.
· Modify the service on port 23 (creating a TELNET session) to correspond to access list number 1. This allows access only to those hosts on that access list (in this case just the host at address 192.168.5.3).
NETCU> ADD ACCESS_LIST 1 PERMIT
192.168.5.3
NETCU> MODIFY
SERVICE 23 TCP /ACCESS_LIST=1
NETCU> SHOW
SERVICE /FULL 23 TCP
TCPware(R) for OpenVMS NETCP Services:
Protocol Port Active Limit Connects Errors Image
-------- ---- ------ ----- -------- ------ ----
TCP TELNET 0 NONE 0 0
/ROUTINE=CREATE_TELNET_SESSION
/ACCESS_LIST=1
NETCU> SHOW ACCESS_LISTS 1
TCPware(R) for OpenVMS NETCP Access Lists:
List Condition InternetAddress AddressMask Access Denied Message
---- --------- --------------- -------------- ---------------------
1 PERMIT 192.168.5.3 255.255.255.255
RELOAD GROUP
Implements changes made to the GROUP database without having to restart the client system. Requires SYSLCK privilege.
|
Note: The GROUP database is normally static. The REL command puts the changes into effect. Use this command sparingly. The client can take a significant amount of time to reload the database. The reloading process blocks NFS activity.
|
Format
RELOAD GROUP
RELOAD NAMED
Reloads the Domain Name Services (DNS) name server’s database files, if needed, by reading the NAMED.BOOT file and checking the zone information.
For example, if your name server is primary for five zones and you change the SOA record for one zone, RELOAD NAMED notices the change and reloads that zone. If you add a zone in the NAMED.BOOT file (for example, a secondary), it notices the change and starts a zone transfer to the primary to gain that zone.
Format
RELOAD NAMED
Examples
NETCU> RELOAD NAMED
%TCPWARE_NETCU-S-NORMAL, normal successful completion
If executing this command after editing NAMED.BOOT and adding a secondary zone 95.168.192.in-addr.arpa with the primary nameserver to be 192.168.95.1, the following entry displays in the NAMESERVER.LOG file:
%%%%%%%%%%%% NAMED 30-APR-2021
10:40:36.11 %%%%%%%%%%%%
%TCPWARE_NAMED-I-SIGNAL, Request to reload databases received.
%%%%%%%%%%%% NAMED 30-APR-2021 10:40:36.12 %%%%%%%%%%%%
%TCPWARE_NAMED-I-RELOAD, reloading name server
%%%%%%%%%%%% NAMED 30-APR-2021 10:40:36.16 %%%%%%%%%%%%
%TCPWARE_NAMED-I-MAIN, Ready to answer queries.
%%%%%%%%%%%% NAMED 30-APR-2021 10:40:36.48 %%%%%%%%%%%%
%TCPWARE_NAMED-I-SUBPROC, created process 000001D4 to transfer zone
95.42.192.in-addr.arpa
%%%%%%%%%%%% NAMED 30-APR-2021 10:40:37.51 %%%%%%%%%%%%
%TCPWARE_NAMED-I-XFERSUCCESS, zone 95.42.192.in-addr.arpa
transferred successfully
%%%%%%%%%%%% NAMED 30-APR-2021 10:40:37.65 %%%%%%%%%%%%
%TCPWARE_NAMED-I-ZONEINFO,secondary zone “95.42.192.in-addr.arpa” loaded
(serial 237)
NETCU> RELOAD NAMED
%TCPWARE_NETCU-S-NORMAL, normal successful completion
If executing this command after editing NAMED.BOOT and increasing the serial number, the following entry displays in the NAMESERVER.LOG file:
%%%%%%%%%%%% NAMED 30-APR-2021
10:28:39.84 %%%%%%%%%%%%
%TCPWARE_NAMED-I-SIGNAL, Request to reload databases received.
%%%%%%%%%%%% NAMED 30-APR-2021
10:28:39.84 %%%%%%%%%%%%
%TCPWARE_NAMED-I-RELOAD, reloading name server
%%%%%%%%%%%% NAMED 30-APR-2021 10:28:40.04 %%%%%%%%%%%%
%TCPWARE_NAMED-I-ZONEINFO, primary zone “yours.com” loaded (serial 6002)
%%%%%%%%%%%% NAMED 30-APR-2021 10:28:40.07 %%%%%%%%%%%%
%TCPWARE_NAMED-I-MAIN, Ready to answer queries.
RELOAD PROXY
Implements changes made to the PROXY database without having to restart the client or server. Not necessary if the TCPWARE_NFS_DYNAMIC_PROXY logical was defined as CLIENT or SERVER. Requires SYSLCK privilege.
|
Note: The PROXY database is normally static. The RELOAD PROXY command puts the changes into effect. Use this command sparingly. The client can take a significant amount of time to reload the database. The reloading process blocks NFS activity.
|
Format
RELOAD PROXY [vms-username[, vms-username, …]
Parameter
vms-username
Reloads only the PROXY database entries for the specified username (or list of usernames separated by commas). This is useful for notifying the client or server of changes to the OpenVMS SYSUAF.DAT file, such as changes to the rights list or user privileges.
Qualifiers
|
Note: If you omit both qualifiers, the PROXY database reloads on both the client and server.
|
/CLIENT
/NOCLIENT
/CLIENT reloads the PROXY database on the client only. /NOCLIENT does not reload the database on the client.
/SERVER
/NOSERVER
/SERVER reloads the PROXY database on the server only. /NOSERVER does not reload the database on the server.
REMOVE ACCESS_LIST
Removes an incoming access restrictions list or a specific entry from a list. Requires write access to the appropriate file.
Format
REMOVE ACCESS_LIST list [condition [ia [mask]]]
Parameters
list
Number of the incoming access restrictions list (1 to 65535).
condition
Sets the condition if access is permitted or denied. Valid keywords are PERMIT and DENY. DENY is the default for hosts not specified on the list.
ia
Internet address of the network or host specified on the list.
mask
Internet address mask, which specifies which bits to use when matching hosts against the incoming access restrictions list. Use set bits when matching hosts against the ia.
If you omit mask and the host portion of ia is 0, NETCU uses the network or subnet mask. If the host portion of ia is not 0, NETCU uses 255.255.255.255, where only the specified host is allowed access.
Examples
1. Removes list 56.
NETCU> REMOVE ACCESS_LIST 56
2. Removes all PERMIT entries from list 56.
NETCU> REMOVE ACCESS_LIST 56 PERMIT
3. Removes the specified entry from list 56.
NETCU> REMOVE ACCESS_LIST 56 PERMIT 192.168.5.0 255.255.255.0
REMOVE ARP
Deletes an entry from an ARP table. Requires OPER privilege.
Each ARP table entry consists of an internet address paired with a physical address.
|
Note: You do not need to use this command under normal circumstances. ARP automatically maps internet addresses to physical addresses. Use this command in rare instances when a particular host does not support ARP.
|
Format
REMOVE ARP destination-ia
Synonym
SET NOARP destination-ia
Parameter
destination-ia
Internet address or host name of the ARP table entry.
Qualifier
/LINE=line
Line id of the ARP table that contains the entry you want removed. If omitted, NETCU determines the ARP table based on the internet address. You require /LINE when the internet address is not a local network address.
RELEASE DHCP
Forces the Dynamic Host Configuration Protocol (DHCP) server to act as if it heard a DHCP release message from a client. This command can be used for dynamically assigned IP addresses only. Requires SYSPRV or OPER privilege.
To address the DHCP V4 server, use DHCP4 instead of DHCP in the command.
|
Note: The DHCP Protocol has no way for the server to tell the client that the address has been released, so this command must be used with caution.
|
Format
RELEASE DHCP ip-address
RELEASE DHCP4 ip-address
Synonym
REMOVE DHCP ip-address
REMOVE DHCP4 ip-address
Parameter
ip-address
The IP address of the lease to release.
Example
Releases the lease for IP address 192.168.5.220.
NETCU> RELEASE DHCP 192.168.5.220
REMOVE EXPORT
Removes an entry from the EXPORT database so that you can remove access to an exported directory for a single host or a list of hosts. Requires write access to the TCPWARE:NFS_EXPORT.DAT file.
|
Note: The EXPORT database is dynamic. Any path that you remove from the database becomes invalid immediately. You do not need to restart the server.
|
Format
REMOVE EXPORT "nfs-path"
Parameter
"nfs-path"
NFS-style pathname used to reference the exported directory. Typically expressed as a UNIX-style pathname. You must enclose the pathname in quotation marks (" ").
Qualifier
/HOST=(host[,host…])
Removes access to an nfs-path for a single host or a list of hosts. If omitted, NETCU removes nfs-path for all hosts.
Example
Removes a record from the EXPORT database so that NFS host ORCHID can no longer mount an OpenVMS directory on the /vax/records pathname.
NETCU> REMOVE EXPORT “/vax/records” /HOST=ORCHID
REMOVE GROUP
Removes a group mapping from the GROUP database on an NFS client. Requires write access to the TCPWARE:NFS_GROUP.DAT file.
|
Note: The GROUP database is static. The REL command puts changes into effect.
|
Format
REMOVE GROUP nfs-group [vms-identifier, …]
Parameters
nfs-group
NFS group number. If you specify nfs-group alone, NETCU removes the entire group from the database.
vms-identifier
OpenVMS rights identifier(s) or UIC(s) associated with the NFS group. If you specify one, NETCU removes only that identifier from the database; NETCU does not change the remaining entries for that group. See the ADD command for the valid format of vms-identifier entries.
Qualifier
/HOST=(server[,server…])
Server host(s) on which the group number is valid. Either host names or internet addresses are valid. This qualifier removes the GROUP entry for the specified host(s) only. Use the parentheses with multiple server specifications.
Example
Removes a record from the GROUP database so that you can no longer associate group number 15 with a group account on the client.
NETCU> REMOVE GROUP 15
REMOVE MULTICAST_GROUP
Removes a multicast host group address from the table of joined addresses for the interface or all interfaces. Requires OPER privilege.
Once you remove a multicast from an interface, applications can no longer receive datagrams sent to that address.
Multicast host group address entries have a reference count. This command decrements the reference count and, if zero, removes the address.
TCPware does not issue an error message if you try to remove an address you never added.
Format
REMOVE MULTICAST_GROUP internet-address
Parameter
internet-address
Internet address or host name of the multicast host group address.
Qualifier
/LINE=line-ID
Line ID of the interface for which to remove the address. If omitted, TCPware removes the address from all active interfaces.
Example
Removes the all-routers multicast address (224.0.0.2) from the SVA-0 Ethernet interface.
NETCU> REMOVE MULTICAST_GROUP 224.0.0.2 /LINE=SVA-0
REMOVE PROXY
Removes an entry from the NFS PROXY database. Requires SYSPRV privilege and write access to the TCPWARE:NFS_PROXY.DAT file.
|
Note: If you omit the /CLIENT or /SERVER qualifier, or do not define the TCPWARE_NFS_DYNAMIC_PROXY logical accordingly, you must use the RELOAD PROXY command to reload the database. (For details, see Reloading the PROXY Database in Chapter 14 of the TCPware Management Guide.)
|
Format
REMOVE PROXY vms-username
Parameter
vms-username
OpenVMS account you want to remove from the PROXY database. You can use the wildcard * in place of vms-username if you use one of the qualifiers below to be more selective about the update.
Qualifiers
If you omit a /HOST, /GID, or /UID qualifier, the command removes all entries containing the vms-username account from the database.
/HOST=(server[,server…])
Server host(s) on which the user is valid. NETCU removes the PROXY entry for the specified host(s) only. Use the parentheses with multiple server specifications.
/GID=gid
User’s group ID (GID). NETCU removes the PROXY entry for the specified GID only.
/UID=uid
User’s ID (UID). NETCU removes the PROXY entry for the specified UID only.
/CLIENT
/NOCLIENT
/CLIENT notifies the client to immediately update its loaded PROXY database with an entry for vms-username. /NOCLIENT (the default) does not notify the client. This overrides any default action specified using the TCPWARE_NFS_DYNAMIC_PROXY logical.
/SERVER
/NOSERVER
/SERVER notifies the server to immediately update its loaded PROXY database with an entry for vms-username. /NOSERVER (the default) does not notify the server. This overrides any default action specified using the TCPWARE_NFS_DYNAMIC_PROXY logical.
Examples
1. Removes authorization for an NFS user at host MARIGOLD with UID=210 and GID=5 to use the OpenVMS username SMITH.
NETCU> REMOVE PROXY SMITH /UID=210 /GID=5 /HOST=MARIGOLD
2. Removes authorization for all users at host CROCUS to use OpenVMS username JONES.
NETCU> REMOVE PROXY JONES /HOST=CROCUS
3. Removes authorization for any user at host MARIGOLD to use any OpenVMS username.
NETCU> REMOVE PROXY * /HOST=MARIGOLD
4. Removes all entries containing the OpenVMS username SMITH.
NETCU> REMOVE PROXY SMITH
5. Removes authorization for a user with UID=210 and GID=5 to use the OpenVMS username SMITH and dynamically reloads the PROXY database on both the client and server.
NETCU> REMOVE PROXY SMITH /UID=210 /GID=5 /CLIENT /SERVER
REMOVE ROUTE
Deletes an entry from the routing table. Requires OPER privilege. (See also ADD.)
Format
REMOVE ROUTE destination-ia gateway-ia
Synonym
SET NOROUTE destination-ia gateway-ia
Parameters
destination-ia
Internet address or host name of the destination host or network.
gateway-ia
Gateway used to reach the host or network identified by the destination-ia parameter.
|
Note: If you added a route by specifying a line, specify 0.0.0.0 as the gateway address when removing the route.
|
Qualifiers
{/HOST | /NETWORK}
Type of route. If omitted, NETCU determines the type of route by looking at the host number portion of the destination-ia. If the host number is zero (0), NETCU assumes the route is a network route.
/MASK=mask
Internet address mask for the Classless Inter-domain Routing (CIDR) protocol. The mask specifies the bits to use for the network portion of a mask. Thus the traditional network masks would be specified as:
Class A Network 255.0.0.0 Class B Network 255.255.0.0 Class C Network 255.255.255.0
If the mask is omitted, the destination address is derived by first checking interfaces for the same network number, and if one is found, the mask for that interface is used. Otherwise, the address is examined to determine if it is a class A, B, C, D, or E address and a mask will be created based on the class.
Network routes are sorted such that the routes with the most restrictive mask are searched before routes with a less restrictive mask. For example, a route with mask 255.255.255.0 is searched before a route with mask 255.255.0.0.
Do not create noncontiguous subnet masks. For example, a mask of 255.0.255.0 is not allowed.
REMOVE SECONDARY
Removes a secondary address previously added with the ADD SECONDARY command. If holding a cluster lock, you must use the /ABORT qualifier to force the removal of the secondary address. Requires OPER privilege.
Format
REMOVE SECONDARY ia
Parameter
ia
Internet address to remove and no longer recognize as a local address.
Qualifier
/ABORT
Forces the release of a cluster lock and the removal of the secondary address. If omitted, TCPware removes only queued requests for the resource lock. /ABORT has no effect when someone added the secondary address without the /CLUSTER_LOCK qualifier. TCPware always removes the secondary address.
Example
Release the cluster lock on the address 192.168.5.101 and no longer recognize the address as a local address.
NETCU> REMOVE SECONDARY 192.168.5.101 /ABORT
REMOVE SERVICE
Stops listening for connections on the specified port. Requires OPER privilege. Removes non-active server connections only unless you use the /ABORT qualifier, which removes all active connections. The TCPWARE:NETCP.LOG file logs each connection serviced. Review this file to obtain details on server errors, and to monitor access and security violations.
|
CAUTION! If you omit both port and protocol, NETCP removes all services from all ports.
|
Format
REMOVE SERVICE [port protocol]
Parameters
port
Service name or port to stop servicing. Any port number is acceptable. A service name must be defined in the TCPWARE:SERVICES. file. If specifying a port or protocol, you must use both. Use 0 as a wildcard to stop servicing all ports for the specified protocol.
protocol
Protocol for the service you want removed: TCP, UDP, STREAM, DGRAM, BG_TCP, or BG_UDP.
Qualifier
/ABORT
Deletes all created active server processes.
/ADDRESS=ip-address
Removes the service for the specified address or hostname only. The default is 0.0.0.0.
Examples
1. Stops listening for UDP connections on all ports.
NETCU> REMOVE SERVICE 0 UDP
2. Stops listening for UDP connections on the TFTP port. NETCP retrieves the TFTP port number from the TCPWARE:SERVICES. file.
NETCU> REMOVE SERVICE TFTP UDP
3. Stops listening for connections on all ports on host BART. Does not affect connections that are currently active.
NETCU> REMOVE SERVICE/ADDRESS=BART
4. Stops listening for connections on all ports and removes all active server processes.
NETCU> REMOVE SERVICE/ABORT
SET
Sets the value for the networking parameters described below. Requires OPER privilege.
|
CAUTION! Be careful when using SET to change parameter values. Make sure you fully understand the effect of these changes before making them. Use the defaults whenever possible.
|
Format
SET parameter value
Parameters and Values
BACKLOG_DROP_THRESHOLD connections
Sets the connection backlog threshold at which TCPware’s "random drop" feature is enabled to address half-open connection flooding problems. When there are more half-open TCP connections on the backlog of a socket than the value set for the BACKLOG_LIMIT parameter, and the BACKLOG_DROP_THRESHOLD value is equal to or less than the BACKLOG_LIMIT value, TCPware drops the oldest half-open connection from the request queue. This makes room for new connections. (If you set BACKLOG_DROP_THRESHOLD greater than BACKLOG_LIMIT under the same conditions, TCPware drops each new connection request.) The default BACKLOG_DROP_THRESHOLD value is 64.
BACKLOG_LIMIT connections
Sets the maximum backlog of waiting connections that can be requested for a listening socket. (For a listen request on a socket that specifies a backlog value higher than the BACKLOG_LIMIT, the latter value is still used, with no error returned.) Set BACKLOG_LIMIT relatively high (together with a relatively lower value for BACKLOG_DROP_THRESHOLD) to deal with half-open connection flooding problems that denial-of-service attacks can cause. The default BACKLOG_ LIMIT value is 1024. Use the following formula to set an optimum BACKLOG_LIMIT value in view of denial-of-service attacks:
Backlog-limit > (Attack-rate x Average-round-trip-time-per-connection)
For example, if the attack rate is 1000 connections per second and the average round trip time is 0.1 seconds, you should set the backlog limit to greater than 100 (=1000 x 0.1).
GATEWAY_MTU maximum-transmission-unit
Maximum transmission units (MTU) of the interface, which determines the size of TCP segments for connections to non-local hosts. The default value is 0.
IPDEFAULTTOS default-type-of-service
Default type-of-service used for all outgoing datagrams that do not explicitly specify a value. The default value is 0.
IPDEFAULTTTL default-time-to-live-hops
Default time-to-live value transmitted in outgoing IP datagrams. The default value is 60.
IPMAXFRAGMENTS max-fragmented-datagrams
Maximum number of fragmented datagrams IPDRIVER holds for reassembly. TCPware discards any fragmented datagrams above the indicated value. The default value is 24. (Use SHOW IPXMAXFRAGMENTS to check the current value.)
IPMAXROUTES max-routing-table-entries
Maximum number of routing table entries allowed by IPDRIVER. The default value is 512. (Use SHOW IPMAXROUTES to check the current value.)
IPMTTL default-multicast-time-to-live
Default multicast time-to-live value used when sending multicast datagrams directly using IP. The default value is 1.
IPREASMTIMEOUT reassembly-timeout-time
IP datagram reassembly timeout time. If you do not receive all the datagrams for a fragment within this time interval, the system discards the partially received datagram. The default value is 30 seconds.
SUBNETSARELOCAL
NOSUBNETSARELOCAL
SUBNETSARELOCAL (the default) treats subnets as being local, where the MTU of the interface determines the maximum segment size of TCP segments for connections to other subnets on the same local network. NOSUBNETSARELOCAL specifies to use the GATEWAY_MTU parameter value for the size of TCP segments.
TCPDEFAULTTOS default-type-of-service
Default type-of-service used for TCP connections. The default value is 0.
TCPDEFAULTTTL default-time-to-live-hops
Default time-to-live used for TCP connections. The default value is 64.
TCPPERSIST persistence-timer-value
TCP persistence timer’s initial value (in milliseconds). The default value is 400 milliseconds (0.4 seconds).
TCPRTOMAX maximum-retransmission-time
Maximum TCP retransmission time (in milliseconds). The default value is 62,000 milliseconds (62 seconds). If you configure TCPware with IP-over-X.25 support, you should reset the maximum retransmission time to 15000.
TCPRTOMIN minimum-retransmission-time
Minimum TCP retransmission time (in milliseconds). The default value is 600 milliseconds (0.6 seconds). If you configure TCPware with IP-over-X.25 support, you should reset the minimum retransmission time to 2000.
UDPRECVLIMIT unsolicited-receives
Default limit of UDP unsolicited receives, or datagrams buffered on a socket if there is no outstanding read before they are dropped.
XMIT_QUEUE_LIMIT maximum-queue-length
Maximum transmit queue length. The default value is 100.
SET BG_
Sets the TCP, UDP, and IP (raw) parameters for the BGDRIVER devices for UCX compatibility.
Formats
SET BG_TCP {DROP_TIMER | PROBE_TIMER} seconds
SET BG_TCP {SEND | RECEIVE} bytes
SET BG_UDP {SEND | RECEIVE} bytes
SET BG_RAW {SEND | RECEIVE} bytes
BG_TCP Parameters and Values
BG_TCP DROP_TIMER seconds
Maximum number of seconds to probe for idle TCP connections before a TCP connection close request times out.
BG_TCP PROBE_TIMER seconds
Number of seconds between probes for idle TCP connections. Also indicates the maximum number of seconds before a TCP connection request times out.
BG_TCP SEND bytes
Sets the message queue size for sending TCP messages.
BG_TCP RECEIVE bytes
Sets the message queue size for receiving TCP messages.
BG_UDP Parameters and Values
BG_UDP SEND bytes
Sets the message queue size for sending UDP messages.
BG_UDP RECEIVE bytes
Sets the message queue size for receiving UDP messages.
BG_RAW Parameters and Values
BG_RAW SEND bytes
Sets the message queue size for sending IP messages.
BG_RAW RECEIVE bytes
Sets the message queue size for receiving IP messages.
SET DHCP
Performs the operations listed here (/debug, /newlog, /partnerdown) on the Dynamic Host Configuration Protocol (DHCP) server. Requires SYSPRV or OPER privileges.
To address the DHCP V4 server, use DHCP4 instead of DHCP in the command.
Format
SET DHCP
SET DHCP4
Qualifiers
/DEBUG=value
Sets the debug logging level to the given value. The value is a decimal integer that is a bitmask of debugging levels used to select messages to log to the debug log file and OPCOM (if configured). The debugging levels are (in decimal):
1 Severe Errors
3 Warnings
7 Informationals
15 Debug Messages
31 Dump Packets (Formatted)
63 Dump Packets (Hex)
By default, Severe Errors and Warnings are logged.
/NEWLOG
Starts a new debug log file. The existing log file is closed immediately. A new log file is created when the next log message is ready to be written.
/PARTNERDOWN
For DHCP failover: Causes the DHCP server to transition into Partner Down state, which indicates that its failover DHCP partner is down.
Example
Sets the debug logging level to log severe error, warning, and informational messages.
NETCU> SET DHCP/DEBUG=7
SET DOMAINNAME
Sets the local host’s domain name. Requires SYSNAM or SYSPRV privilege, and uses the setdomainname() socket library subroutine.
|
Note: The TCPware startup command procedure, STARTNET.COM, sets the domain name to the name specified during network configuration.
|
Format
SET DOMAINNAME domain-name
Parameter
domain-name
Domain name or host name of the local host. Must be the name of the local host as other systems within the network know it.
SET FILTER
SET FILTER loads the specified packet filter file and associates the filter list with the specified line(s). SET NOFILTER removes a previously associated filter list from the specified line(s). SET FILTER and SET NOFILTER require OPER privilege.
Formats
SET FILTER line[, line…] file
[/LOG=logfile/INTERVAL=interval/FORMAT=format]
SET NOFILTER line[, line …]
Parameters
line
Line ID of the network device.
file
Packet filter file that contains the packet filter list. The default file extension is .DAT.
See Chapter 21, Packet Filtering, of the TCPware Management Guide for the format of a packet filter file.
|
Note: An implicit deny terminates the list of entries in the packet filter file. Therefore, an entry in the list must explicitly permit a datagram. If the file has no entries and you set filtering for a line based on that file, it implicitly filters out all datagrams on that line. You can also filter out all traffic on a line using the command SET FILTER line NLA0:.
|
Qualifiers
/LOG=logfile
/NOLOG
Defines the destination for logged filter activity. This may be a file name or OPCOM to log the information to OPCOM. When logging to OPCOM, the operator console must be enabled with either NETWORK or SECURITY.
/INTERVAL=interval
Sets the logging interval in seconds.
/FORMAT=format
Sets the output format of the logged data. If set to normal, the output will be the same as displayed via NETCU SHOW FILTER.
If set to comma, the output will be in comma-separated (CSV) format, which may be imported into a spreadsheet or other program. The file contains a header line (comma-separated) which describes each field.
Examples
1. Sets lines ESA-0 and FZA-0 to check the filters in the TCPWARE:FILTER-1.DAT file.
NETCU> SET FILTER ESA-0,FZA-0 TCPWARE:FILTER-1.DAT
2. Removes an associated filter list from lines ESA-0 and FZA-0.
NETCU> SET NOFILTER ESA-0,FZA-0
3. Filters out all traffic on line ESA-0.
NETCU> SET FILTER ESA-0 NLA0:
SET GATED TRACE
Tells the GATED process to turn on or off various tracing flags. This controls what is placed in the TCPWARE:GATED.LOG file. By default, minimal tracing is done.
Format
SET GATED TRACE qualifier
Qualifiers
/ADVERTISE
/NOADVERTISE
Sets tracing of route advertising.
/ALL
Turns on all tracing.
/DETAILS
/NODETAILS
Sets tracing of all send and receive information.
/RECV_DETAILS
/NORECV_DETAILS
Sets tracing of receive information.
/SEND_DETAILS
/NOSEND_DETAILS
Sets tracing of send information.
/EVENTS
/NOEVENTS
Sets tracing of normal events.
/INTERFACES
/NOINTERFACES
Sets tracing of network interface information.
/NONE
Turns off all tracing.
/PACKETS
/NOPACKETS
Sets tracing of packet sends and receives.
/RECV_PACKETS
/NORECV_PACKETS
Sets tracing of packet receives.
/SEND_PACKETS
/NOSEND_PACKETS
Sets tracing of packet sends.
/PARSING
/NOPARSING
Sets tracing of configuration file parsing.
/POLICY
/NOPOLICY
Sets tracing of policy decisions.
/ROUTING
/NOROUTING
Sets tracing of routing table changes.
/STATES
/NOSTATES
Sets tracing of state machine transitions.
/SYMBOLS
/NOSYMBOLS
Sets tracing of kernel symbols.
/TASKS
/NOTASKS
Sets tracing of task and job functions.
/TIMER
/NOTIMER
Sets tracing of timer functions.
Example
This example tells the GateD process to turn on tracing of policy decisions and turn off tracing of state machine transitions.
NETCU> SET GATED TRACE /POLICY /NOSTATES
SET GATEWAY
Defines a default gateway. Requires OPER privilege.
The system uses a default gateway whenever you need to send an IP datagram to a host that is not on a local network and for which no other route is known.
|
Note: Traffic for a host routes through a default gateway unless a routing table entry exists for that host or its network. You can add entries to the routing table manually (see the ADD command) or you can add them automatically (using ICMP redirect messages from a gateway).
|
Format
SET GATEWAY ia [ia…]
Parameter
ia
Internet address or host name of a default gateway on one of the local networks.
You can have any number of default gateways. Subsequent SET GATEWAY commands add an additional default gateway. To remove an individual default gateway, use the REM command. To remove all default gateways, use the SET GATEWAY 0.0.0.0 command.
When you use multiple SET GATEWAY commands, TCPware uses the first gateway on the list. If TCPware finds that the gateway is marked possibly down, it goes to the next gateway on the list in a round robin fashion until one responds.
SET INET
Sets the TCP parameters for the INET devices. These commands affect services added using the STREAM protocol.
Formats
SET INET_TCP DROP_TIMER value
SET INET_TCP PROBE_TIMER value
INET_TCP Parameters and Values
INET_TCP DROP_TIMER value
Maximum number of seconds to probe for idle TCP connections before a TCP connection close times out.
INET_TCP PROBE_TIMER value
Number of seconds between probes for idle TCP connections. Also indicates the maximum number of seconds before a TCP connection request times out.
SET INTERFACE
Sets interface related parameters and options. The command is only meaningful if used with one or more of the allowed qualifiers.
The /ARP_*, /COMMON_LINK, and /RECEIVE_LIMIT qualifiers are only valid for Ethernet, FDDI, Token Ring, and Classical IP over ATM or LAN Emulation over ATM devices.
The /RECEIVE_LIMIT qualifier is only valid for interfaces that use the VMS Communications Interface (VCI). If issued for other interfaces, the limit is set but not honored. Interfaces that do not implement this support show 0 for the maximum receive packet rate displayed by the SHOW INTERFACE command.
Format
SET INTERFACE line-id qualifier [qualifier …]
Parameter
line-id
Line ID of the interface.
Qualifiers
/ARP_AGE_INTERVAL=seconds
Controls how often to check the Address Resolution Protocol (ARP) times. The default is 30 seconds.
/ARP_AGE_LIMIT=seconds
Controls how long an unused ARP entry is left in the cache. The default is 600 seconds (10 minutes).
/ARP_WAIT_LIMIT=seconds
Controls how long to wait for an initial ARP entry that is unresolved to be removed from the cache, or when a CONFPEND entry times out and is removed from the cache. The default is 20 seconds, which translates into 30 seconds under most instances because a check is done only every 30 seconds (see /ARP_AGE_INTERVAL).
|
Note: Use the above /ARP_* qualifiers carefully. They should not normally be changed.
|
/ARP_ENTRY_LIMIT=entries
Controls the size of the ARP cache (number of ARP entries) for an interface. The default is 512 entries.
/COMMON_LINK=line-ids
The /COMMON_LINK qualifier works for systems that have multiple interfaces on a common Ethernet, FDDI, or Token Ring cable. The system manager configures this support using the following command:
NETCU> SET INTERFACE line-id/COMMON_LINK=(line-id,line-id,...)
With this command TCPware adds ARP entries for each device into the other device's ARP caches and internally links the interfaces together. A performance benefit of this linking occurs if data is to be transmitted on an interface that happens to be busy, TCPware assigns the data to the least busy linked interface for transmission.
This linking also provides a level of redundancy. If a linked interface is shut down using NETCU STOP/IP or if a fatal error is detected with the interface and an automatic restart cannot be attempted, then any routing table entries or pseudo devices associated with the shutdown interface will be failed over to one of the common link interfaces.
|
Note: If failover does occur, the interface is removed from the list of interfaces on the common link. If the interface is restarted, you must re-issue the NETCU SET INTERFACE/COMMON_LINK command.
|
· The joined interfaces must be connected to the same cable.
· The joined interfaces must have the same MTU.
· The NETCU DEBUG/IP command shows the interface that a write is queued to. However, with linked interfaces, the datagram might be transmitted from a linked interface.
· If an interface on the common link is shut down and restarted via the NETCU START/IP command, you must re-issue the NETCU SET INTERFACE/COMMON_LINK command to rejoin the interfaces.
It is also possible that when the interface is restarted some ARP entries for the interface may remain in other interfaces' ARP caches leading to a "Duplicate IP address!" message on the console. If the address reported is for another interface on the same machine, you can ignore this warning.
/RECEIVE_LIMIT=packets-per-second
Sets the receive packet rate to the specified limit. Can be used to impose a limit on the number of packets to be received per second on an interface. If more than the specified number of packets are received in any one second period, the additional packets are dropped and, in some cases, an OPCOM message is generated (see below). If the value is set to 0, limiting is turned off (the default).
While you should not normally use a limit, you can in some situations do so where the network is unstable or prone to packet storms. In these cases, you need to determine an appropriate normal packet rate to determine the proper receive limit.
Use the SHOW INTERFACE command to display the packet rate limit and maximum receive packet rate values. The maximum receive packet rate can be useful in determining an appropriate limit for a system.
The OPCOM message Warning - maximum receive packet rate exceeded on line line-id (rate packets/second) is generated only when both the limit and previous maximum rate are exceeded. TCPware keeps a maximum rate for each interface and SET resets this rate.
The line ID for the offending interface is displayed in numeric form. To convert this to an ASCII line ID, use the SHOW FILTER numeric-id command to display the corresponding ASCII line ID, or see (Line ID Values) in Chapter 5, IPDRIVER Services, of the TCPware Programmer's Guide.
Example
The SET INTERFACE command in this example resets the receive packet rate for the SVA-0 interface to 400 packets/second, with a resulting maximum receive packet rate change from 484 to 309 packets/second. The ARP entry limit parameter was reset to 1024 entries.
NETCU> SHOW INTERFACE SVA-0
For Network Line SVA-0:
No receive packet rate limit has been set.
The maximum receive packet rate was 484 packets/second.
The ARP entry limit is 512 entries.
The ARP age check interval is 30 seconds.
The ARP entry age limit is 600 seconds.
The ARP entry wait limit is 20 seconds.
NETCU> SET INTERFACE SVA-0 /RECEIVE_LIMIT=400
/ARP_ENTRY_LIMIT=1024
NETCU> SHOW
INTERFACE SVA-0
For Network Line SVA-0:
The receive packet rate limit is set at 400 packets/second.
The maximum receive packet rate was 309 packets/second.
The ARP entry limit is 1024 entries.
The ARP age check interval is 30 seconds.
The ARP entry age limit is 600 seconds.
The ARP entry wait limit is 20 seconds.
SET IPS
Enables or disables line-specific or system-specific processing of DoD Security Options (IPSO). Requires OPER privilege.
Format
SET IPS { /DEBUG=n | /RELOAD | /RESTART | /START | /STOP }
Qualifiers
/DEBUG=n
Change the debug level for the server. Levels above 4 should never be set without instructions from Process Software.
/RELOAD
Re-read and parse the configuration files. Note that this will not wipe out existing state (event and rule) information; it will simply update it so no potential filter information will be lost.
/RESTART
Stop and restart the filter server process. All existing event and rule information will be lost and reloaded from the configuration file.
/START
Start the filter server process if it’s not already running.
/STOP
Stop the filter server process from running. All existing event and rule information will be lost.
Examples
$ NETCU SET IPS /DEBUG=3
This causes the debug level of the server to be set to 3.
SET IPSO
Enables or disables line-specific or system-specific processing of DoD Security Options (IPSO). Requires OPER privilege.
Format
SET [NO]IPSO { /LINE | /SYSTEM }
Qualifiers
/LINE[=(line-id, line-id …)]
Defines the line or set of lines for which to set security options. (Lines are equivalent to ports or network interfaces, such as SVA-0.) Use parentheses for multiple lines separated by commas. If you omit line-id, the SET IPSO command affects all lines. You must use /LINE if you do not use /SYSTEM.
/[IN_ | OUT_]LABEL=(LEVEL=(min-level[,max-level]) -
,AUTHORITY={(auth1[,auth2,…]) | ANY | NONE})
Sets the minimum and maximum security levels and list of authorities for incoming or outgoing datagrams. /IN_LABEL specifies a label for incoming datagrams. /OUT_LABEL specifies a label for outgoing datagrams. /LABEL by itself specifies a label for both incoming and outgoing datagrams. Use parentheses for multiple parameters separated by commas.
LEVEL sets the single (if just min-level) or minimum and maximum security levels. Use parentheses if setting both min-level and max-level separated by a comma. Valid security levels appear in the below table. Specify the level either by its name (such as Top_Secret) or hexadecimal value (such as %X3D). If you omit the LEVEL keyword (or, for that matter, the entire /LABEL type qualifier), the default level is Unclassified.
|
Security Level |
Hexadecimal Value |
|
Top_Secret |
%X3D |
|
Secret |
%X5A |
|
Confidential |
%X96 |
|
Unclassified |
%XAB |
AUTHORITY sets a protection authority (authority) or a list of authorities. Use parentheses for multiple authorities separated by commas. The predefined authorities appear in the below table. Specify the authority either by its name (such as GENSER) or its hexadecimal value (such as %X80).
|
Protection Authority |
Hexadecimal Value |
Point of Contact |
|
GENSER |
%X80 |
Designated Approving Authority per DOD 5200.28 |
|
SIOP-ESI |
%X40 |
DoD Joint Chiefs of Staff |
|
SCI |
%X20 |
Director of Central Intelligence |
|
NSA |
%X10 |
National Security Agency |
|
DOE |
%X08 |
Department of Energy |
A single authority field can also be in the form "auth1+auth2+..." (such as "GENSER+SCI"), with a plus sign (+) between values embedded in quotes. Alternatively, you can use the logically OR'd hexadecimal value of the combined authorities (such as %X30 for "SCI+NSA"), or you can use the site-specific value from the TCPWARE:IPSO_AUTHORITIES. file.
An AUTHORITY value of ANY means that the port will accept all authority fields in datagrams. If you omit the AUTHORITY keyword (or, for that matter, the entire /LABEL type qualifier), the default is a null authority (NONE).
/SYSTEM
Specifies that the parameters on the command line are SYSTEM parameters. If set, these parameters are the first ones tested on outgoing datagrams and the last ones tested on incoming datagrams destined for the host. You must use /SYSTEM if you do not use /LINE.
/ERROR_LABEL={(LEVEL=level, AUTH={auth | NONE}) | NONE}
Sets labels for ICMP error messages to allow originators of out-of-range datagrams to receive these messages. Set a single level and single authority only. If omitted, the default is LEVEL=Unclassified and AUTHORITY=NONE. /ERROR_LABEL=NONE means that the system should not return ICMP errors.
/EXTENDED_ALLOWED[=([NO]IN, [NO]OUT)]
/NOEXTENDED_ALLOWED[=(IN, OUT)]
/EXTENDED_ALLOWED specifies that you want Extended Security Option fields allowed on incoming or outgoing datagrams. You can selectively disallow security options using the NOIN and NOOUT keywords, or disallow them more generally using /NOEXTENDED_ALLOWED. The default is /EXTENDED_ALLOWED=(IN, OUT).
/FIRST
/NOFIRST
Specifies that the IPSO Basic Option be the first option in the datagram header on outgoing datagrams. Some security systems require this.
If you previously specified /STRIP on a line, make sure to /NOSTRIP before using /FIRST. You cannot use /FIRST with /STRIP in a single command. The default is /NOFIRST.
/RECEIVE_IMPLICIT_LABEL={(LEVEL=level, AUTHORITY=auth
-
[, {REQUIRED | NOREQUIRED}]) | NONE}
Associates an implicit label with a received datagram. Use a single level and single authority only. REQUIRED specifies that you require a label and not to use an implicit one. NOREQUIRED specifies that you do not require a label and to use an implicit one. The default is NONE, which is Unclassified and a null authority.
/TRANSMIT_IMPLICIT_LABEL={(LEVEL=level, AUTHORITY=auth
-
[, {ADD | NOADD}][, {REQUIRED | NOREQUIRED}]) |NONE}
Associates (or adds) an implicit label with a transmitted datagram. Use a single level and single authority only. See /RECEIVE_IMPLICIT_LABEL for a description of keywords and values.
The additional ADD keyword ensures that you actually add the basic security option containing this label to the datagram header.
If you previously specified /STRIP on a line, make sure to /NOSTRIP before using /TRANSMIT_IMPLICIT. You cannot use the ADD keyword with /TRANSMIT_IMPLICIT together with the /STRIP qualifier in a single command.
/STRIP
/NOSTRIP
/STRIP strips security options from the datagram header on outgoing datagrams. Useful for routers and forwarding datagrams on which you do not want to impose security restrictions. Be careful using /STRIP if you want to have further IPSO checks performed. The default is /NOSTRIP.
Examples
1. Sets the IPSO system parameters with a security level of Secret and a protection authority of DOE for both incoming and outgoing datagrams.
NETCU> SET IPSO /SYSTEM /LABEL=(LEVEL=SECRET, AUTHORITY=DOE)
2. Sets a Secret security level and a DOE protection authority for incoming labeled datagrams on lines SVA-0 and ENA-0.
NETCU> SET IPSO /LINE=(SVA-0,ENA-0) /IN_LABEL=(LEVEL=SECRET, AUTHORITY=DOE)
3. Specifies that all incoming datagrams on line SVA-0 should have a Secret security level and a protection authority of either SCI+NSA or just DOE.
NETCU> SET IPSO /LINE=SVA-0 /IN_LABEL=(LEVEL=SECRET, AUTHORITY=("SCI+NSA",DOE))
4. Identical to the previous example except that the command uses hexadecimal values for the level and authorities.
NETCU> SET IPSO /LINE=SVA-0 /IN_LABEL=(LEVEL=%X3D, AUTHORITY=(%X30,%X08))
5. Sets an error label value for ICMP error messages in response to out-of-range datagrams. Note that you can specify only one level and one authority.
NETCU> SET IPSO /ERROR_LABEL=(LEVEL=SECRET, AUTHORITY=DOE)
6. Specifies that any unlabeled transmitted datagrams implicitly use a Secret DOE label and to process any unlabeled received datagrams with an Unclassified Null Authority label.
NETCU> SET IPSO /LINE=SVA-0 /TRANSMIT_IMPLICIT_LABEL=(LEVEL=SECRET, AUTHORITY=DOE) /RECEIVE_IMPLICIT_LABEL=NONE
7. Like Example 6 except that this adds a basic security option with the specified label to the transmitted datagram.
NETCU> SET IPSO /LINE=SVA-0 /TRANSMIT=(LEVEL=SECRET, AUTHORITY=DOE, ADD) /RECEIVE=NONE
8. Specifies requiring a label and not using an implicit one.
NETCU> SET IPSO /LINE=SVA-0 /RECEIVE_IMPLICIT_LABEL=REQUIRED
9. Specifies not to process datagrams with Extended Security
Option fields. The default is
/EXTENDED_ALLOWED.
NETCU> SET IPSO /LINE=SVA-0 /NOEXTENDED_ALLOWED
SET LOG
Sets the file for logging Network Control Program (NETCP) activity. When TCPware starts, it automatically logs to the TCPWARE:NETCP.LOG file. SET NOLOG stops NETCP logging. If no logging is set, SET LOG resets NETCP logging to another log file.
SET LOG/FTP/NEW
Causes the FTP listener to open a new log file without being restarted.
SET LOG /NFS
Sets the NFS server file for logging NFS server activity. When TCPware starts, it automatically logs to the TCPWARE:NFSSERVER.LOG file. SET NOLOG /NFS stops NFS server logging. If no logging is set, SET LOG /NFS resets NFS server logging to another log file.
SET NOLOG/FTP
Causes the FTP listener to stop logging anonymous connection information.
Format
SET LOG
SET NOLOG
SET LOG/FTP/NEW
SET LOG /NFS
SET NOLOG/FTP
SET NOLOG /NFS
Qualifiers
/NEW [file]
Closes the current NETCP log file and creates a new revision of that file. If a filename is indicated, the new log file name will be used for logging.
/NEW/NFS [file]
Closes the current NFSSERVER.LOG file and creates a new revision of that file. If a filename is indicated, the new log file name will be used for logging.
/NEW/FTP file
Closes the current FTP_LISTENER.LOG file and opens a new file with the specified name.
Examples
1. Closes the current NETCP log file (if open) and creates a new NETCP2.LOG file.
NETCU> SET LOG /NEW TCPWARE:NETCP2.LOG
2. Closes the current NETCP log file and creates a new revision of that file.
NETCU> SET LOG /NEW
3. Closes the current NFSSERVER.LOG file (if open) and creates a new NFSSERVER2.LOG file.
NETCU> SET LOG /NEW /NFS TCPWARE:NFSSERVER2.LOG
4. Closes the current NFSSERVER log file and creates a new revision of that file.
NETCU> SET LOG /NEW /NFS
SET NAMED DEBUG
Sets the debug level for NAMED. The larger the debug value, the more verbose the output. A debug value of 0 sets the debug level to off.
Format
SET NAMED DEBUG n
Example
Defines the debug logical.
$ NETCU SET NAMED DEBUG 2
%TCPWARE_NETCU-S-NORMAL, normal successful completion
SET NAMED MAXIMUM_TTL
This command changes the maximum time-to-live (TTL) that resource records are cached from the default 604800 seconds (1 week) to the value given.
Format
SET NAMED MAXIMUM_TTL n
Parameter
n
An integer value representing the maximum number of seconds the nameserver should cache a non-authoritative answer.
Example
NETCU> SET NAMED MAXIMUM_TTL 302400
SET NAMED MINIMUM_TTL
This command changes the minimum time-to-live (TTL) that resource records are cached from the default of zero (0) seconds to the value given.
|
Note: It is recommended you use this command only if there is a specific need. This could cause problems in that you may be caching resource records for longer than the authoritative administrator intended.
|
Format
SET NAMED MINIMUM_TTL n
Parameter
n
An integer value representing the minimum number of seconds the nameserver should cache a non-authoritative answer.
Example
NETCU> SET NAMED MINIMUM_TTL 0
SET OUTGOING_ACCESS_RESTRICTIONS
SET OUTGOING_ACCESS_RESTRICTIONS loads the specified outgoing access restrictions file. The default file specification is TCPWARE:TCPWARE_OUTGOINGRESTRICT.DAT.
SET NOOUTGOING_ACCESS_RESTRICTIONS removes the outgoing access restrictions file. Both commands require OPER privilege.
|
Note: An outgoing access restrictions list loaded using this command supersedes any previously existing one.
|
Formats
SET OUTGOING_ACCESS_RESTRICTIONS file
SET NOOUTGOING_ACCESS_RESTRICTIONS
Parameter
file
Outgoing access restrictions file. The default file is TCPWARE:TCPWARE_OUTGOINGRESTRICT.DAT. You can locate the file in system-specific directories such as TCPWARE_SPECIFIC.
See Chapter 20, Access Restrictions, of the TCPware Management Guide for the format of an outgoing access restrictions file entry. You can also deny all access using the command:
NETCU> SET OUTGOING_ACCESS_RESTRICTIONS NLA0:
Examples
1. Loads the BARTRESTRICT.DAT file that contains outgoing access restrictions in the system-specific directories.
NETCU> SET OUTGOING_ACCESS_RESTRICTIONS TCPWARE_SPECIFIC:BARTRESTRICT.DAT
2. Restricts all outgoing access on the local system.
NETCU> SET OUTGOING_ACCESS_RESTRICTIONS NLA0:
3. Removes all outgoing access restrictions for the local system.
NETCU> SET NOOUTGOING_ACCESS_RESTRICTIONS
SET SSH /DEBUG
Sets the debug level.
Format
SET SSH /DEBUG
Parameter
level
Entering zero turns off all debug information in the SSHD.LOG file. Entering a non-zero number turns on debug.
Example
Set the SSH debug level to 2:
$ NETCU SET SSH /DEBUG=2
|
Note: Enabling higher levels of debug may have serious performance impacts on a system, as well as consuming significant disk space for logs. Therefore, debug levels higher than 4 should only be used when recommended by Process Software Technical Support.
|
SET TIMEZONE
Sets the offset from universal time and optional time zone name for the IP layer (used for ICMP timestamp replies). Requires SYSNAM and OPER privilege.
Formats
SET TIMEZONE +hh[mm[ss]] [name]
SET TIMEZONE name
Parameters
+hh[mm[ss]]
Hours, minutes, and seconds offset from the universal time (UT). Use + for east of the central meridian, - for west. For example, +0400 is 4 hours east of the central meridian at Greenwich. In another example, Eastern Standard Time (EST) is five hours west of UT, so the offset is -0500.
name
(Optional) Name of the time zone. For example, EDT is for Eastern Daylight time. When using the SET TIMEZONE name syntax, use only the following known time zone names:
|
Time |
Time Zone Name |
|
Universal Time |
UT, UTC or GMT |
|
North American Time |
EST, EDT, CST, CDT, MST, MDT, PST, PDT |
|
Military Time |
Any single uppercase letter A through Z except J. We do not recommend using this format. |
Examples
NETCU> SET TIMEZONE -0500
NETCU> SET TIMEZONE EDT
NETCU> SET TIMEZONE +0100 MET
NETCU> SET TIMEZONE +0100 BST
SHOW
Shows the values for a variety of networking parameters. See the SET command for additional details on these parameters.
Format
SHOW parameter
Parameters
BACKLOG_DROP_THRESHOLD
Minimum backlog limit required on a listening port for "random" drop to take effect. (See the SET BACKLOG_DROP_THRESHOLD command.)
BACKLOG_LIMIT
Maximum listen backlog allowed for listening ports. (See the SET BACKLOG_LIMIT command.)
BG_TCP {DROP_TIMER | PROBE_TIMER | SEND | RECEIVE}
DROP_TIMER, PROBE_TIMER, SEND, and RECEIVE parameters for BG_TCP devices. (See the SET BG_ commands for details on these parameters.)
BG_UDP {SEND | RECEIVE}
SEND and RECEIVE parameters for BG_UDP devices. (See the SET BG_ commands for details on these parameters.)
BG_RAW {SEND | RECEIVE}
SEND and RECEIVE parameters for BG_RAW (IP) devices. (See the SET BG_ commands for details on these parameters.)
GATEWAY_MTU
Maximum size of TCP segments for connections to non-local hosts. A value of 0 means that TCPware uses the maximum transmission unit (MTU) of the interface to determine the size.
IPDEFAULTTOS
Type-of-service used for all outgoing datagrams that do not explicitly specify a value.
IPDEFAULTTTL
Time-to-live value transmitted in outgoing IP datagrams.
IPMAXFRAGMENTS
Maximum number of fragmented datagrams IPDRIVER holds for reassembly.
IPMAXROUTES
Maximum number of routing table entries allowed by IPDRIVER.
IPMTTL
Default multicast time-to-live value used when sending multicast datagrams directly using IP.
IPREASMTIMEOUT
IP datagram reassembly time-out time (in seconds).
INET_TCP {DROP_TIMER | PROBE_TIMER}
DROP_TIMER and PROBE_TIMER parameters for INET devices. (See the SET commands for details on these parameters.)
SM[_BAK]
Shows the contents of the NFS server Network Status Monitor file, SM.DAT (or in the case of SHOW SM_BAK, the backup file, SM_BAK.DAT, that appears after a reboot). Use ADD SM[_BAK] or REMOVE SM[_BAK] to add nodes to or remove nodes from the file. (Do not edit the file directly.)
SHOW SM and SHOW SM_BAK truncate host names at the 120th character so it is good practice to limit names to less than 120 characters when adding hosts to the table.
SUBNETSARELOCAL
Shows if the system treats subnets as being local. A value of 1 means to treat subnets as being local. 0 means not to treat subnets as being local.
TCPDEFAULTTOS
Default type-of-service value used for TCP connections.
TCPDEFAULTTTL
Default time-to-live value used for TCP connections.
TCPPERSIST
TCP persistence timer's initial value (in milliseconds).
TCPRTOMAX
Maximum TCP retransmission time (in milliseconds).
TCPRTOMIN
Minimum TCP retransmission time (in milliseconds).
UDPRECVLIMIT
Default limit of UDP unsolicited receives, or datagrams buffered on a socket if there is no outstanding read before they are dropped.
Qualifier
/OUTPUT=filespec
Sends output to the specified file. If omitted, output displays on the terminal screen.
Troubleshooting
%TCPWARE_NLM-F-TIMEOUT, device timeout
UDP send timeout
%TCPWARE_NLM-F-TIMEOUT, device timeout
NLM_RPC: Portmapper call failed
%TCPWARE_NLM-F-NOSUCHNODE, remote node is unknown
NLM_RPC: network error
One or more of these messages may indicate that a node being monitored by the NFS Server Network Status Monitor has gone down or is unreachable. Use the SHOW SM (or SHOW SM_BAK) command as indicated under the SM[_BAK] parameter description.
SHOW ACCESS_LISTS
Displays all incoming access restrictions lists or a specific list. Requires OPER privilege.
DENY entries usually appear before PERMIT entries for each list number. The exception is when there is a duplicate address (or network part of the address) with a more restrictive address mask, in which case the PERMIT entry comes first.
The Access Denied Message always appears next to the first entry for a list number, although the message may originally have been entered with another item in that list (using ADD ACCESS_LIST /MESSAGE).
Format
SHOW ACCESS_LISTS [list]
Parameter
list
Incoming access restrictions list number, from 1 to 65535.
Qualifier
/OUTPUT=filespec
Sends output to the specified file. If omitted, output displays on the terminal screen.
Example
Shows access entries for list 16 and prints them in the ACCESS.TXT file.
NETCU> SHOW ACCESS_LISTS 16 /OUTPUT=ACCESS.TXT
TCPware(R) for OpenVMS NETCP
Access Lists:
List Condition Internet Address Address Mask Access Denied Message
---- --------- ---------------- --------------- ---------------------
16 DENY 192.168.5.23 255.255.255.255 "access not
authorized"
PERMIT 192.168.45.21 255.255.255.255
PERMIT 192.168.5.0 255.255.255.0
PERMIT 192.168.30.0 255.255.255.0
SHOW ARP
Displays the entire Address Resolution Protocol (ARP) table for the specified Ethernet, FDDI, or HYPERchannel line. Returns and displays the internet address, its corresponding physical address (or incomplete if the address has not been resolved), and a flags field. The flags field can consist of:
|
Flags Field |
Description |
|
PERM |
You cannot remove the entry from the table (created using ADD ARP /PERMANENT) |
|
PUBL |
Local host can respond to ARP requests for this entry (created using ADD ARP /PUBLISH) |
|
LOCK |
ARP messages cannot change the entry's physical address (created using ADD ARP /LOCK) |
|
LASU |
Last reference to this entry was a use rather than an update |
|
CONF |
Next use of this entry requires confirmation |
|
PEND |
Confirmation attempt is pending |
The first table entry is for the local host's internet address.
Format
SHOW ARP line
Parameter
line
Network device line ID for the ARP table. You can only display one ARP table.
Qualifiers
/HOST_NAMES
Shows host names, if available, instead of IP addresses.
/OUTPUT=filespec
Sends output to the specified file. If omitted, output displays on the terminal screen.
Example
This command displays the ARP table for the QNA-0 network device. The Flags entries in this example indicate that the system manager used the /PERMANENT, /PUBLISH, and /LOCK qualifiers to set up the ARP table.
NETCU> SHOW ARP QNA-0
TCPware(R) for OpenVMS Address Resolution Table for Network Line QNA-0:
Internet Address Physical Address Flags
---------------- ----------------- ------
192.168.5.21 AA-00-04-00-15-08 PERM, PUBL, LOCK
192.168.5.1 AA-00-04-00-01-08 LASU, PEND
192.168.5.8 AA-00-04-00-08-08 CONF
SHOW CONNECTIONS
Displays a list of the currently active internet connections (equivalent to the UNIX netstat -a command). The following information appears for each connection:
· Connection ID - TCP, UDP, INET, or BG device name.
· Receive queue count - Number of bytes in the receive queue.
· Send queue count - Number of bytes in the transmit queue.
· Local host internet address and port number.
· Remote host internet address and port number.
· State - Displayed for TCP connections only.
NETCU SHOW CONNECTIONS displays 1024 TCP connections and 512 UDP connections before displaying ???. These characters mean there are more connections than NETCU SHOW CONNECTIONS can print.
Format
SHOW CONNECTIONS
Qualifiers
/ALL
Displays all listening connections.
/CONTINUOUS
Display of the information uses the OpenVMS Screen Management Facility, which updates it every two seconds. (NETCU does not highlight areas of change.) Do not use together with /OUTPUT. See the /CONTINUOUS qualifier for the SHOW COUNTERS command for the commands to use in the display.
/HOST_NAMES
Displays the host name for an internet address if it is available. TCPware ignores /CONTINUOUS if SYS$OUTPUT is not a terminal class device, or the terminal is not a scope.
/LOCAL
Includes the address and port for incoming and outgoing connections.
/NUMERIC
Displays port numbers in numeric form. If omitted, NETCU tries to translate these numbers into service names using the TCPWARE:SERVICES. file.
/PID
Displays the process ID associated with each device.
/REMOTE
Includes the address and port for incoming and outgoing connections.
/TCP
/NOTCP
Displays (/TCP) or does not display (/NOTCP) TCP connections. /TCP is the default.
/UDP
/NOUDP
Displays (/UDP) or does not display (/NOUDP) UDP connections. /UDP is the default.
/OUTPUT=filespec
Sends output to the specified file. If omitted, output displays on the terminal screen. Do not use together with /CONTINUOUS.
SHOW COUNTERS
Displays the TCPDRIVER and UDPDRIVER statistics counters.
Format
SHOW COUNTERS
Qualifiers
/CONTINUOUS
Display of the information uses the OpenVMS Screen Management Facility, which updates it every two seconds. (NETCU does not highlight areas of change.) Do not use together with /OUTPUT. Use the following commands when in the display:
|
Ctrl/B |
Scroll display back one line |
|
Ctrl/B |
Scroll display one line |
|
Ctrl/W |
Repaint the screen |
|
Ctrl/C or Ctrl/Z |
Return to the NETCU> prompt |
TCPware ignores /CONTINUOUS if SYS$OUTPUT is not a terminal class device or the terminal is not a scope.
/OUTPUT=filespec
Sends output to the specified file. If omitted, output displays on the terminal screen. Do not use together with /CONTINUOUS.
/RESET
Resets the counters after their display. Requires OPER privilege.
Example
For details on the TCP counters in the above example, see the IO$_SENSEMODE | IO$M_RD_COUNT description in Chapter 3, TCPDRIVER Services, in the TCPware Programmer's Guide. For details on the UDP counters in the above example, see the IO$_SENSEMODE | IO$M_RD_COUNT descriptions in Chapter 4, UDPDRIVER Services, in the TCPware Programmer's Guide.
NETCU> SHOW COUNTERS
TCPware(R) for OpenVMS Counters:
Seconds since zeroed: 1776384
TCP segments transmitted: 2814 TCP segments received:2214
Delayed ACKS: 1491 Out of sequence: 28
Window updates: 18 Receive errors: 0
Segments retransmitted: 58 Concatenated RDBs: 10
Keep-alives/Persists: 56
Transmit errors: 0
Concatenated XDBs: 10
Seconds since zeroed: 1776382
UDP datagrams transmitted: 15 UDP datagrams received:3008
Transmit errors: 0 Receive errors: 0 Undelivered datagrams: 2923
SHOW DHCP
Displays a variety of information about the Dynamic Host Configuration Protocol (DHCP) server and its configuration, depending on the qualifiers specified. The /LEASES qualifier is the default.
To address the DHCP V4 server, use DHCP4 instead of DHCP in the command.
Format
SHOW DHCP
SHOW DHCP4
Qualifier
/ALL
Displays SHOW DHCP/SUBNET output for all subnets in the DHCP server configuration, then it displays brief information about all static assignments.
/CLIENT_IDENTIFIER=client-id
Displays details about all leases and static assignments that match the given client ID. Clients can have leases on multiple subnets simultaneously.
/CONFIGURATION
Writes all DHCP server configuration and lease information to a dump file. The default dump file is TCPWARE:DHCPD.DUMP. Use the /OUTPUT qualifier to specify a different dump file.
/HARDWARE_ADDRESS=hardware-address
Displays details about all leases and static assignments that match the given hardware address. Clients can have leases on multiple subnets simultaneously.
/IP_ADDRESS=ip-address
Displays the current lease binding details for the given IP address. The IP address must be in the dynamic pool. Statically bound IP addresses are not supported.
/ISKNOWN
After specifying the /ISKNOWN qualifier, specify one of the following:
HOST hardware-address-or-client-id
SUBCLASS class-name subclass-data
If HOST is specified, shows whether the given hardware address or client identifier is "known", that is if there is a HOST declaration for that hardware address or client identifier. If SUBCLASS is specified, shows whether the given subclass data exists as a subclass within the given class.
/LEASES
For all subnets, displays brief information about the IP addresses that have leases (pending, active, or expired). Statically assigned IP addresses are not shown. This is the default for the SHOW DHCP command if no qualifiers are specified.
/OUTPUT=filespec
Sends output to the specified file. If not specified, output appears on the terminal screen (except for the SHOW DHCP/CONFIGURATION command; see the separate description).
/POOLS
Displays a table showing the number of IP addresses that are available for each IP address pool. An IP address pool corresponds to a shared-network statement, a subnet statement, or a POOL statement in the DHCP configuration file.
/STATUS
Verifies whether the DHCP server is running and displays a message accordingly.
/SUBNET=ip-address
Displays brief information about each IP address in the same shared network as the given IP address. Statically assigned IP addresses are not shown.
/VERIFY=(option, [option…])
Inspects the syntax of the DHCP server configuration file and optionally the lease file and update file and displays any errors found. By default, the standard DHCP configuration file (TCPWARE:DHCPD.CONF) is checked. The options are as follows:
|
config[=filename] |
Specifies the name and location of the configuration file to verify. If not specified, the default configuration file is used. |
|
lease[=filename] |
Specifies the name and location of the lease file to verify. If the filename is not specified, the default lease file is used (TCPWARE:DHCPD.LEASES). If the lease option is not specified, the lease file is not checked. |
|
update[=filename] |
Specifies the name and location of the update file to verify. If the filename is not specified, the default update file is used (TCPWARE:DHCPD.UPDATES). If the update option is not specified, the update file is not checked. |
/VERSION
Displays the version of the DHCP server.
Examples
NETCU> SHOW DHCP/VERIFY
Process Software DHCP Server for TCPWARE
Copyright Process Software. Internet Systems Consortium DHCP Server
Copyright Internet Systems Consortium.
For info, please visit
https://www.isc.org/software/dhcp/
reading config file: tcpware:dhcpd.conf
tcpware:dhcpd.conf line 8: Expecting numeric value
ping-retries no;
^
exiting.
NETCU> SHOW DHCP/IP_ADDRESS=10.10.10.100
TCPware(R) for OpenVMS DHCP IP Address Information
IP Address 10.10.10.100
Subnet Mask 255.255.255.0
Default Gateway 10.10.10.1
State Leased (expired)
Lease Length 300 secs
Lease Obtained 10-Mar-2021 20:29:56 GMT
Lease Expires 10-Mar-2021 20:34:56 GMT (-33 secs)
Hardware Address 11 22 33 44 55 66
Client ID 74 65 73 74
"test"
NETCU> SHOW DHCP/ISKNOWN HOST 01:02:03:04:05:06
Host 01:02:03:04:05:06 is known by hardware address
NETCU> SHOW DHCP/SUBNET=10.10.10.100
TCPware(R) for OpenVMS DHCP Configured Addresses on Subnet
Address Expires (GMT) Client Address/Identifier
-------- ------------- -------------------------
Shared Network 10.10.10.0
Pool 1
10.10.10.104 <available>
10.10.10.102 <abandoned>
10.10.10.100 <expired> 74 65 73 74
"test"
10.10.10.103 10-Mar-2021 18:49:26 00 00 F8 00 00 BB "..ø..»"
|
Column |
Content |
|
Address |
Shows the IP address. |
|
Expires |
Identifies the date and time the lease expires in Greenwich Mean Time (GMT), also known as Universal Coordinated Time (UTC). If there is no active lease, this column shows the state of the IP address. |
|
Client Address/Identifier |
Shows either the hardware address or the client identifier in two-digit hexadecimal groupings followed by the ASCII text equivalent. |
NETCU> SHOW DHCP/POOLS
TCPware(R) for OpenVMS DHCP Address Pool Availability
< Shared Network Pool Total Abandoned Reserved Available
< -------------- ---- ----- --------- -------- ---------
< local total 44 5 0 15
< 1 44 5 0 15
< 10.12.1.0 total 128 2 0 57
< 1 111 0 0 54
< 2 11 2 0 0
< 3 6 0 0 3
|
Pool Heading |
Description |
|
Shared Network |
The name from the shared-network statement or the subnet number from the subnet statement. |
|
Pool |
“Total” for the complete information for the shared network, otherwise a number identifying the pool. You can see which IP addresses are in which pools using the SHOW DHCP/ALL or SHOW DHCP/SUBNET command. |
|
Total |
The total number of IP addresses in the pool. |
|
Abandoned |
The number of IP addresses in the pool which were found in use on the network when they were thought to be free. |
|
Reserved |
If DHCP safe-failover is in use, the number of IP addresses in the pool reserved for the secondary DHCP server. These addresses are unassigned but reserved for the secondary. |
|
Available |
The number of IP addresses in the pool available to be leased. |
SHOW DNIP
Displays information about the currently configured DECnet over IP tunnels.
Format
SHOW DNIP
Qualifier
/OUTPUT=filespec
Sends output to the specified file. If omitted, output displays on the terminal screen.
Example
The status displayed by this command is the status of the TCP connection associated with the DNIP tunnel. NETCU has no knowledge of the state of the DECnet line and circuit associated with this tunnel. Use the DECnet NCP utility to show information about the DECnet state.
NETCU> SHOW DNIP
TCPware(R) for OpenVMS DECnet-over-IP Tunnels:
DECnet Line Remote Host Local Port Remote Port Status
----------- ----------- ---------- ----------- ------
DNIP-0-0 alpha.example.com 64215 64215 Established
DNIP-0-1 beta.example.com 777 654 Established
SHOW EXPORT
Displays the NFS server's EXPORT database, the filesystem pathnames that the server exports, and any access restrictions that the server imposes on each pathname. If a local file, requires read access to the TCPWARE:NFS_EXPORT.DAT file.
Format
SHOW EXPORT [server-host]
Parameter
server-host
NFS server host for which you want to display the EXPORT database. If omitted, NETCU examines the local server's EXPORT database.
Qualifiers
/BINDINGS
Shows the device bindings for the NFS server, as a device name and 32-bit value.
/FULL
Shows the full range of options. (See the ADD EXPORT command description for details on the qualifiers used for these options.)
/PATH="server-path"
Displays only filesystems matching the specified server path. You can include the standard OpenVMS wildcard characters (* and %). Enclose the pathname in quotation marks (" ").
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
/UDP
Use UDP (instead of TCP) to contact the remote system for the export list. When using UDP the TCPware RPC processing has a limit of 8800 bytes in the response.
Examples
1. Displays the local NFS server's EXPORT database. If there is no local NFS server, NETCU displays an error message. The display for a local NFS server includes the directory header for the device and directory to which each exported pathname is equivalent on the local OpenVMS system.
NETCU> SHOW EXPORT
NFS EXPORT Database Copyright (c) Process Software
Path Directory Host(s)
---- --------- -------
/user SYS$SYSDEVICE:[USER]
/root SYS$SYSDEVICE:[000000]
2. Displays a remote NFS server's export database. The display for the remote server does not include the directory header.
NETCU> SHOW EXPORT IRIS.EXAMPLE.COM
NFS EXPORT Database Copyright (c) Process Software
Server: iris.example.com
Path Host(s)
---- -----
/user lambda.example.com
/root
SHOW FILTER
Displays the current packet filter list for the specified line(s). Requires OPER privilege. The display also includes the number of permitted and denied packet hits so that you can flag potential access violations.
In addition, if the /EXTRACT qualifier is used, the current filters loaded in the kernel for the specified interface are written in packet filter file format to the specified output file.
Format
SHOW FILTER line[, line …] [/OUTPUT=filespec][/EXTRACT=filespec]
Parameter
line
Line ID of the network device.
Qualifier
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
/EXTRACT=filespec
Writes the list of filters currently loaded in the kernel on the specified interface, to the specified file. The format of the output information is the same as that used as input to the NETCU SET FILTER interface file command. If a list of interfaces is specified, only the filters for the first interface are output.
Example
Displays the filters for lines SVA-0. Note that source and destination address masks appear on the second line of each entry. In this partial filter list example, the entries:
· Permit local traffic. The number of packets permitted has been 47.
· Deny UDP datagrams on NFS port 2049. The number of packets denied has been 3.
· Permit TCP datagrams on ports greater than 1023 at a particular destination address. The number of packets permitted has been 11.
· Permit TCP datagrams at the same address on SMTP port 25. The number of packets permitted has been 19.
· Permit UDP datagrams at the same address on DNS port 53. The number of packets permitted has been 12.
· Permit all ICMP datagrams at the same address. The number of packets permitted has been 2.
NETCU> SHOW FILTER SVA-0
TCPware(R) for OpenVMS Packet Filter List for SVA-0:
Source Source Destination Destination
Action Proto Address/Mask Port Address/Mask Port Option Hits
------ ----- ------------- ------ ------------- ----- ------ ----
permit ip 192.168.5.0 0.0.0.0
255.255.255.0 0.0.0.0 47
deny udp 0.0.0.0 0.0.0.0 eq 2049
0.0.0.0 0.0.0.0 3
permit tcp 0.0.0.0 192.168.5.0 gt 1023
0.0.0.0 255.255.255.0 11
permit tcp 0.0.0.0 192.168.5.0 eq 2519
0.0.0.0 255.255.255.0 19
permit udp 0.0.0.0 192.168.5.0 eq 53\
0.0.0.0 255.255.255.0 12
permit icmp 0.0.0.0 192.168.5.0
0.0.0.0 255.255.255.0 2
SHOW GATED TRACE
Shows what GATED tracing TCPware is currently doing. There may be a delay of several seconds before the GATED process returns the tracing information.
Format
SHOW GATED TRACE
Example
This example shows how to get the GateD tracing status.
NETCU> SHOW GATED TRACE
Summary of GateD tracing
---------------------------------------------
State Machine Transitions Logging is : 'ON'
Internal Events Logging is : 'ON'
Policy Decision Logging is : 'ON'
Task Information Logging is : 'ON'
Timer Logging is : 'ON'
Routing Information Logging is : 'ON'
General Send and Receive Logging is : 'ON'
General Receive Logging is : 'ON'
General Send Logging is : 'ON'
Packet Send and Receive Logging is : 'ON'
Packet Receive Logging is : 'ON'
Packet Send Logging is : 'ON'
Configuration File Parsing Logging is : 'ON'
Route Advertisement Logging is : 'ON'
Kernel Symbols Logging is : 'ON'
Network Interface Logging is : 'ON'
SHOW GROUP
Displays entries in the NFS client's GROUP database. Requires read access to the TCPWARE:NFS_GROUP.DAT file.
Format
SHOW GROUP [nfs-group]
Parameter
nfs-group
NFS group number for which to show database entries. If omitted, NETCU displays entries for all groups on the local client.
Qualifiers
/HOST=(server[,server …])
Server host(s) on which the group number is valid. NETCU accepts either host names or internet addresses. Use the parentheses with multiple server specifications.
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
Example
Shows the NFS group number on host IRIS and corresponding OpenVMS group name and value.
NECU> SHOW GROUP /HOST=IRIS
NFS GROUP Database Copyright (c) Process Software
Group Name Value Host(s)
----- ---- ----- -------
15 USER [200,*] IRIS
SHOW HOST
Displays the official host name, internet address (or addresses), and alias host names for a host, if found.
Format
SHOW HOST host[,host …]
Synonym
FIND HOST host[,host …]
Parameter
host
Host name or internet address of the host whose information you want displayed.
Qualifier
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
Example
Displays the official host name, internet address(es), and alias host names for a host.
NETCU> SHOW HOST
_Host name or Internet address: DAISY
Host DAISY.EXAMPLE.COM
Internet address 192.168.5.16
SHOW INTERFACE
Displays the following information for the specified interface:
· Packet rate limit (if set)
· Maximum rate seen since the interface was started or the last SET command was issued
· Address Resolution Protocol (ARP) entry limit, age check interval, entry age limit, and entry wait limit values
· The interface data rage (Mbits per second)
· The buffer size (bytes) of the interface.
For details on packet rate and ARP setting, see the SET command.
Format
SHOW INTERFACE line-id
Parameter
line-id
Line ID of the interface.
Qualifier
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
Example
This example shows the packet rate limit and maximum receive packet rate for the SVA-0 interface. The subsequent SET command resets the receive packet rate to 400 packets/second. The final SHOW INTERFACE command shows the reset values. The ARP entry limit parameter was reset to 1024 entries.
NETCU> SHOW INTERFACE SVA-0
For Network Line SVA-0:
No receive packet rate limit has been set.
The maximum receive packet rate was 484 packets/second.
The ARP entry limit is 512 entries.
The ARP age check interval is 30 seconds.
The ARP entry age limit is 600 seconds.
The ARP entry wait limit is 20 seconds.
NETCU> SET INTERFACE
SVA-0 /RECEIVE_LIMIT=400 /ARP_ENTRY_LIMIT=1024
NETCU> SHOW INTERFACE SVA-0
For Network Line SVA-0:
The receive packet rate limit is set at 400 packets/second.
The maximum receive packet rate was 309 packets/second.
The ARP entry limit is 1024 entries.
The ARP age check interval is 30 seconds.
The ARP entry age limit is 600 seconds.
The ARP entry wait limit is 20 seconds.
The linespeed is 100 (Mbps).
The MTU is 1500.
SHOW IPS
Write the current filter server configuration to a file. Requires OPER privilege.
Format
SHOW IPS /CONFIG{=filename}
If you omit the filename for the /CONFIG qualifier, the output will be written to SYS$DISK:[]FILTER_SERVER.TXT.
Qualifiers
/CONFIG_FILE=filename
Write the configuration information to the specified filename.
Example
Displays the full IPSO information for the system, including counter information.
$ netcu show ips/config
$ type filter_server.txt
Filter server snapshot 2-JUN-2021 09:34:42.43
Debug level 6
Block at destination port or system: PORT
Log to:
OPCOM via OPCOM targets "NETWORK,DEVICES,OPER3,OPER12,SECURITY"
SNMP trap, specific ID "38", generic ID "24", enterprise string "this is the string"
Logfile (tcpware:filter_logfile.log)
Component: ftp
Rule: ftp_invaliduser
IPV6 address = FALSE
Dest address = 192.168.0.11/32
Dest port = 21
Interface name = se0
Max event count = 10
Delta time = 0 00:05:00.00
Filter durations = 300 600 1800 3600 -1
hourly hits = 0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
hourly filters = 0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
Rule: ftp_userauth
IPV6 address = FALSE
Dest address = 192.168.0.11/32
Dest port = 21
Interface name = se0
Max event count = 21
Delta time = 0 00:03:00.00
Filter durations = 300 600 1800 3600 -1
hourly hits = 0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
hourly filters = 0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
Rule: ftp_authfailed
IPV6 address = FALSE
Dest address = 192.168.0.11/32
Dest port = 21
Interface name = se0
Max event count = 21
Delta time = 0 00:01:30.00
Filter durations = 300 600 1800 3600 -1
hourly hits = 0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
hourly filters = 0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
Rule: ftp_timeout
IPV6 address = FALSE
Dest address = 192.168.0.11/32
Dest port = 21
Interface name = se0
Max event count = 21
Delta time = 0 00:01:30.00
Filter durations = 300 600 1800 3600 -1
hourly hits = 0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
hourly filters = 0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
SHOW IPSO
Displays IPSO information on datagrams. Requires OPER privilege.
Format
SHOW IPSO
If you omit all qualifiers, displays basic information for all lines and SYSTEM. You must use the /FULL qualifier to display additional counter information.
Qualifiers
/FULL
Displays additional counter information.
/LINE[=(line-id, line-id …)]
Shows the IPSO options for a specific line or lines.
/SYSTEM
Shows the SYSTEM options.
Example
Displays the full IPSO information for the system, including counter information.
NETCU> SHOW IPSO /SYSTEM /FULL
TCPware(R) for OpenVMS IPSO Configuration for line SVA-0:
Label Level Authorities
----- ----- -----------
In: UNCLASSIFIED to SECRET SIOP-ESI
GENSER
Out: SECRET to SECRET C1(DOE+SCI+SIOP-ESI)
Implied
Receive: None None
Transmit: SECRET None
ICMP Error: SECRET C1(DOE+SCI+SIOP-ESI)
Label on received datagrams is required
Incoming datagrams screened by IPSO
0 contained a BSO
0 were delivered to receivers
0 contained extended options
0 used implicit labeling
0 were rejected as out-of-range
0 were rejected due to containing ESO
3226 lacked a required BSO
Outgoing datagrams screened by IPSO
12 contained a BSO
8 were successfully transmitted
0 contained extended options
0 used implicit labeling
0 were rejected as out-of-range
0 were rejected due to containing ESO
0 lacked a required BSO
SHOW MOUNT
Displays a list of client hosts that mounted a file system served by a specified NFS server. Returns the mounted directories by the pathnames NETCU uses to export them, not the directory names as the OpenVMS system knows them.
Format
SHOW MOUNT [server-host]
Parameter
server-host
NFS server host from which to get the list of mounted file systems. If omitted, NETCU uses the local server.
Qualifier
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
Examples
1. Because the user did not specify the server host name, the system displays the full domain name for the local server ZETA. In this example no client hosts have mounted any of the server file system.
NETCU> SHOW MOUNT
NFS Mount List Copyright (c) Process Software
Server: ZETA.example.com
Path Host
---- ----
2. Displays the list of client hosts and directories by pathnames for mounted file systems served by the specified server IRIS.
NETCU> SHOW MOUNT IRIS
NFS Mount List Copyright (c) Process Software
Server: IRIS
Path Host
---- ----
/sales/records bart.example.com
/exported/spool bart.example.com
SHOW MULTICAST_GROUPS
Displays the joined multicast host group address table for the specified interface or all interfaces.
Format
SHOW MULTICAST_GROUPS [line-id]
Parameter
line-id
Line ID of the interface for which to display the table. If omitted, the table includes all active interfaces.
Qualifier
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
Example
Displays the multicast host groups for the SVA-0 Ethernet interface. Note that the RefCnt (reference count) for 224.0.0.1, the all-hosts group address, is -perm-, which means that it is permanent and you cannot remove it.
NETCU> SHOW MULTICAST_GROUPS
TCPware(R) for OpenVMS Multicast Host Groups:
Host Group Address RefCntLine Name
------------------ ---------- ----
224.0.0.1 -perm-SVA-0 ALL-SYSTEMS.MCAST.NET
226.1.1.1 1SVA-0?
SHOW NETWORKS
Displays the IPDRIVER network information for each line, any active secondary addresses, and the IPDRIVER datagram counters. The command is equivalent to the UNIX netstat -i command.
Format
SHOW NETWORKS
Qualifiers
/CONTINUOUS
Display of the information uses the OpenVMS Screen Management Facility, which updates it every two seconds. (NETCU does not highlight areas of change.) Do not use together with /OUTPUT.
TCPware ignores /CONTINUOUS if SYS$OUTPUT is not a terminal class device or the terminal is not a scope. See the SHOW COUNTERS command for the screen commands to use.
/OUTPUT=filespec
Sends output to the specified file. If omitted, output displays on the terminal screen. Do not use together with /CONTINUOUS.
Example
NETCU> SHOW NETWORKS
TCPware(R) for OpenVMS Internet Network Information:
Line Local Address Subnet MaskMTU Xmits Errs Recvs Errs RBU
---- ------------- -------------- ----- ---- ----- ---- ---
SVA-0 192.168.5.33 255.255.255.0 1500 1 0 1197 0 0
LPB-0 127.0.0.1 255.0.0.0 64512 0 0 0 0 0
Secondary Address State
----------------- -----
192.168.5.102 Active, holding cluster lock
192.168.5.101 Inactive, queued for cluster lock
0 IP datagrams were transmitted, of which
0 were fragmented
0 were forwards
0 were ICMP requests/replies
0 were IGMP reports
263 IP datagrams/fragments were received, of which
0 were fragments
0 were forwarded
0 were ICMP requests/replies
0 were IGMP queries/reports
259 IP datagrams were delivered to receivers.
SHOW OSPF
Queries OSPF routers. You can obtain a wide variety of detailed information from these routers using these commands.
All of the SHOW OSPF commands use a file called TCPWARE:OSPF_DESTS.DAT. This is a file of OSPF destination records. Each record is a single line entry listing the destination IP address, the destination host name, and an optional OSPF authentication key (if the destination activates authentication).
|
CAUTION! Since the OSPF_DESTS.DAT file may contain authentication information, you should restrict access to it.
|
Format
SHOW OSPF option
Options
ADVERTISE area-id
type
ls-id
adv-router
index
/OUTPUT=file
/FILE=file
/TIMEOUT=seconds
Displays link state advertisements. The parameters and qualifiers for SHOW OSPF ADVERTISE are as follows:
|
Parameter and Qualifier |
Description |
|
area-id |
OSPF area for which the query is directed. |
|
type |
The available types are
INTERFACES - Requests the router links advertisements. Describes the collected states of the router's interfaces. For this request, the ls-id field should be set to the originating router's Router ID.
ROUTERS - Requests the network links advertisements. Describes the set of routers attached to the network. For this request, the ls-id field should be set to the IP interface address of the network's Designated Router.
NETWORK_ROUTES - Requests the summary link advertisements describing routes to networks. Describes the inter-area routes and enables the condensing of routing information at area borders. For this request, the ls-id field should be set to the destination network's IP address.
BOUNDARY_ROUTES - Requests the summary link advertisements describing routes to AS boundary routers. Describes the inter-area routes and enables the condensing of routing information at area borders. For this request, the ls-id field should be set to the Router ID of the described AS boundary router.
EXTERNAL_ROUTES - Requests the AS external link advertisements. Describes routes to destinations external to the AS. For this request, the ls-id field should be set to the destination network's IP address. |
|
ls-id |
See the type parameter. |
|
adv-route |
Router ID of the router that originated this link state advertisement. |
|
index |
Indexes into a file of OSPF destination records. |
|
/OUTPUT=file |
Name of an output file to write the results to. |
|
/FILE=file |
Alternate file of OSPF destination records to use. |
|
/TIMEOUT=seconds |
Interval to wait for a response. Default is 20 seconds. |
AS index
/OUTPUT=file
/FILE=file
/TIMEOUT=seconds
Shows the Autonomous System (AS) external database entries. This table reports the advertising router, forwarding address, age, length, sequence number, and metric for each AS external route. The parameters and qualifiers for SHOW OSPF AS are as follows:
|
index |
Indexes into a file of OSPF destination records. |
|
/OUTPUT=file |
Name of an output file to write the results to. |
|
/FILE=file |
Alternate file of OSPF destination records to use. |
|
/TIMEOUT=seconds |
Interval to wait for a response. Default is 20 seconds. |
DESTINATIONS/OUTPUT=file
/FILE=file
This command displays the list of destinations and their indices described in an OSPF destination records file. The parameters and qualifiers for SHOW OSPF DESTINATIONS are as follows:
|
/OUTPUT=file |
Name of an output file to write the results to. |
|
/FILE=file |
Alternate file of OSPF destination records to use. |
ERRORS index
/OUTPUT=file
/FILE=file
/TIMEOUT=seconds
Shows the error log. This reports the different error conditions that can happen between OSPF routing neighbors and shows the number of occurrences for each. The parameters and qualifiers for SHOW OSPF ERRORS are as follows:
|
index |
Indexes into a file of OSPF destination records. |
|
/OUTPUT=file |
Name of an output file to write the results to. |
|
/FILE=file |
Alternate file of OSPF destination records to use. |
|
/TIMEOUT=seconds |
Interval to wait for a response. Default is 20 seconds. |
HOPS index
/OUTPUT=file
/FILE=file
/TIMEOUT=seconds
Shows the set of next hops for the OSPF router being queried. The parameters and qualifiers for SHOW OSPF HOPS are as follows:
|
index |
Indexes into a file of OSPF destination records. |
|
/OUTPUT=file |
Name of an output file to write the results to. |
|
/FILE=file |
Alternate file of OSPF destination records to use. |
|
/TIMEOUT=seconds |
Interval to wait for a response. Default is 20 seconds. |
INTERFACES index
/OUTPUT=file
/FILE=file
/TIMEOUT=seconds
Displays all interfaces. This shows all the interfaces configured for OSPF. The information includes the area, interface IP address, interface type, interface state, cost, priority, and the IP address of the DR and BDR of the network. The parameters and qualifiers for SHOW OSPF INTERFACES are as follows:
|
index |
Indexes into a file of OSPF destination records. |
|
/OUTPUT=file |
Name of an output file to write the results to. |
|
/FILE=file |
Alternate file of OSPF destination records to use. |
|
/TIMEOUT=seconds |
Interval to wait for a response. Default is 20 seconds. |
LOG index
/OUTPUT=file
/FILE=file
/TIMEOUT=seconds
Shows the cumulative log. This log includes input and output statistics for monitor requests, hellos, database descriptions, link state updates, and link state ACK packets. Area statistics are provided that describe the total number of routing neighbors and number of active OSPF interfaces. Routing table statistics are summarized and reported as the number of intra-area routes, inter-area routes, and AS external database entries.
The parameters and qualifiers for SHOW OSPF LOG are as follows:
|
index |
Indexes into a file of OSPF destination records. |
|
/OUTPUT=file |
Name of an output file to write the results to. |
|
/FILE=file |
Alternate file of OSPF destination records to use. |
|
/TIMEOUT=seconds |
Interval to wait for a response. Default is 20 seconds. |
NEIGHBORS index
/OUTPUT=file
/FILE=file
/TIMEOUT=seconds
/RETRANSMIT
This command shows all OSPF routing neighbors. The information shown includes the area, local interface address, router ID, neighbor IP address, state, and mode. The parameters and qualifiers for SHOW OSPF NEIGHBORS are as follows:
|
index |
Indexes into a file of OSPF destination records. |
|
/OUTPUT=file |
Name of an output file to write the results to. |
|
/FILE=file |
Alternate file of OSPF destination records to use. |
|
/TIMEOUT=seconds |
Interval to wait for a response. Default is 20 seconds. |
|
/RETRANSMIT |
Displays the retransmit list of neighbors. |
ROUTING index
/OUTPUT=file
/FILE=file
/TIMEOUT=seconds
Shows the OSPF routing table. This table reports the AS border routes, area border routes, summary AS border routes, and the networks managed using OSPF. The parameters and qualifiers for SHOW OSPF ROUTING are as follows:
|
index |
Indexes into a file of OSPF destination records. |
|
/OUTPUT=file |
Name of an output file to write the results to. |
|
/FILE=file |
Alternate file of OSPF destination records to use. |
|
/TIMEOUT=seconds |
Interval to wait for a response. Default is 20 seconds. |
STATE index
/OUTPUT=file
/FILE=file
/TIMEOUT=seconds
/RETRANSMIT
Shows the link state database (except for ASEs). This describes the routers and networks making up the AS. The parameters and qualifiers for SHOW OSPF STATE are as follows:
|
index |
Indexes into a file of OSPF destination records. |
|
/OUTPUT=file |
Name of an output file to write the results to. |
|
/FILE=file |
Alternate file of OSPF destination records to use. |
|
/TIMEOUT=seconds |
Interval to wait for a response. Default is 20 seconds. |
|
/RETRANSMIT |
Displays the retransmit link state database. |
Examples
1. Displays the OSPF cumulative log for index 1 in the OSPF_DESTS.DAT file.
NETCU> SHOW OSPF LOG 1
Source <<192.168.5.31 izar.example.com>>
IO stats
Input Output Type
2 0 Monitor request
0 0 Hello
0 0 DB Description
0 0 Link-State Req
0 0 Link-State Update
0 0 Link-State Ack
ASE: 0 checksum sum 0
LSAs originated: 39 received: 0
Router: 39
Area 0.0.0.0:
Neighbors: 0 Interfaces: 0
Spf: 1 Checksum sum CE9D
DB: rtr: 1 net: 0 sumasb: 0 sumnet: 0
Routing Table:
Intra Area: 0 Inter Area: 0 ASE: 0
2. Displays the OSPF interface log for index 1 in the OSPF_DESTS.DAT file.
NETCU> SHOW OSPF INTERFACE 1
Source <<192.168.5.31 izar.example.com>>
IO stats
Input Output Type
6 0 Monitor request
0 0 Hello
0 0 DB Description
0 0 Link-State Req
0 0 Link-State Update
0 0 Link-State Ack
ASE: 0 checksum sum 0
LSAs originated: 39 received: 0
Router: 39
Area 0.0.0.0:
Neighbors: 0 Interfaces: 0
Spf: 1 Checksum sum CE9D
DB: rtr: 1 net: 0 sumasb: 0 sumnet: 0
Routing Table:
Intra Area: 0 Inter Area: 0 ASE: 0
3. Displays the OSPF destination records in the OSPF_DESTS.DAT file.
NETCU> SHOW OSPF DESTINATIONS
1: 192.168.5.31 izar.example.com
4. Displays the OSPF link state database log for index 1 in the OSPF_DESTS.DAT file.
NETCU> SHOW OSPF STATE 1
Source <<192.168.5.31 izar.example.com>>
LS Data Base:
Area: 0.0.0.0
Type LinkState ID AdvRouter Age Len Sequence Metric Where
----------------------------------------------------------------
Rtr 192.168.5.31 192.168.5.31 986 24 80000027 0 SpfTree
5. Displays the OSPF next hops log for index 1 in the OSPF_DESTS.DAT file.
NETCU> SHOW OSPF HOPS 1
Source <<192.168.5.31 izar.example.com>>
Next hops:
Address Type Refcount Interface
---------------------------------------------------------
192.168.5.31 Direct 1 192.168.5.31 SVA-0
6. Displays the OSPF error log for index 1 in the OSPF_DESTS.DAT file.
NETCU> SHOW OSPF ERRORS 1
Source <<192.168.5.31 izar.example.com>>
Packets Received:
3: Monitor request 0: Hello
0: DB Description 0: Link-State Req
0: Link-State Update 0: Link-State Ack
Packets Sent:
0: Monitor response 0: Hello
0: DB Description 0: Link-State Req
0: Link-State Update 0: Link-State Ack
Errors:
0: IP: bad destination 0: IP: bad protocol
0: IP: received my own packet 0: OSPF: bad packet type
0: OSPF: bad version 0: OSPF: bad checksum
0: OSPF: bad area id 0: OSPF: area mismatch
0: OSPF: bad virtual link 0: OSPF: bad authentication type
0: OSPF: bad authentication key 0: OSPF: packet too small
0: OSPF:packet size > ip length 0: OSPF: transmit error
0: OSPF: interface down 0: OSPF: unknown neighbor
0: HELLO: netmask mismatch 0: HELLO: hello timer mismatch
0: HELLO: dead timer mismatch 0: HELLO: extern option mismatch
0: HELLO: router id confusion 0: HELLO: virtual neighbor unknown
0: HELLO: NBMA neighbor unknown 0: DD: neighbor state low
0: DD: router id confusion 0: DD: externoption mismatch
0: DD: unknown LSA type 0: LS ACK: neighbor state low
0: LS ACK: bad ack 0: LS ACK: duplicate ack
0: LS ACK: Unknown LSA type 0: LS REQ: neighbor state low
0: LS REQ: empty request 0: LS REQ: bad request
0: LS UPD: neighbor state low 0: LS UPD: newer self-gen LSA
0: LS UPD: LSA checksum bad 0: LS UPD:received less recent LSA
0: LS UPD: unknown LSA type
SHOW OUTGOING_ACCESS_RESTRICTIONS
Displays all outgoing access restrictions. Requires OPER privilege. You can also direct output to a file that you can subsequently load as a new outgoing access restrictions file.
Format
SHOW OUTGOING_ACCESS_RESTRICTIONS
Qualifier
/OUTPUT=file
File output for the outgoing access restrictions. TCPware formats the information in the output file so that you can use it as an input file for the SET OUTGOING_ACCESS_RESTRICTIONS command.
See Chapter 20, Access Restrictions, in the TCPware Management Guide for the format of an outgoing access restrictions file entry.
Example
Logs all connections, denies local users access to the SMTP port (25) over the network, and only permits general outgoing access for users with the INTERNET_USER rights identifier.
NETCU> SHOW OUTGOING_ACCESS_RESTRICTIONS
TCPware(R) for OpenVMS Outgoing Access Restrictions List
Actions Userid Destination Address Destination Mask Port
------- ------ -------------------- ---------------- ----
LOG * 0.0.0.0 0.0.0.0
DENY * 0.0.0.0 0.0.0.0 EQ 25
PERMIT INTERNET_USER 0.0.0.0 0.0.0.0
SHOW PROXY
Displays the contents of the NFS PROXY database. Requires read access to the TCPWARE:NFS_PROXY.DAT file.
Format
SHOW PROXY [vms-username]
Parameter
vms-username
OpenVMS account entries you want to display. If omitted, the system displays the contents of the PROXY database determined by the qualifiers listed below.
Qualifiers
/HOST=(server[,server …])
Displays the PROXY entries restricted to the specified server host(s) only, or for which there are no host restrictions given. Specify one or more server hosts (if multiple, separate by a comma and use the parentheses).
/GID=gid
NFS user's group ID (GID). NETCU displays only entries containing the specified GID.
/UID=uid
NFS user's ID (UID). The system displays only entries containing the specified UID.
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
Example
Displays the PROXY database entries for user SMITH.
$ NETCU SHOW PROXY SMITH
NFS PROXY Database Copyright (c) Process Software
Username UID GID Host(s)
-------- --- --- -------
SMITH 100 101
SHOW RIP
Used to request all routes known by a RIP gateway. The routing information in any routing packets returned is displayed numerically and symbolically. This command is intended to be used as a tool for debugging gateways, not for network management.
Format
SHOW RIP gateway-ia
Parameter
gateway-ia
Internet address or name of the gateway to be queried.
Qualifiers
/AUTHENTICATION=authkey
Authentication password to use for queries. If specified, an authentication type of SIMPLE is used. The default authentication type is NONE.
/NONAME
Prevents the responding host's address from being looked up to determine the symbolic name.
/POLL
Requests information from the gateway's routing table. This is the default. If there is no response to the /POLL qualifier, the /REQUEST qualifier is tried.
/REQUEST
Requests information from the gateway's routing table. Unlike the /POLL qualifier, all gateways should support this command. If there is no response, the /POLL qualifier is tried.
/TIMEOUT=seconds
Number of seconds to wait for the initial response from a gateway. Default is 5 seconds.
/TRACE
Traces the RIP packets being sent and received by this command.
/V1
Sends the query as a RIP version 1 packet.
/V2
Sends the query as a RIP version 2 packet.
Example
Shows the routers known by RIP gateway 192.33.23.2.
NETCU> SHOW RIP 192.33.23.2
24 bytes from omega1.example.com(192.33.23.2):
net/mask router metric tag
192.168.5.0/255.255.255.0 192.33.23.1 2 0000
SHOW ROUTES
Displays the following internet routing information for each route:
· Destination internet address
· Gateway internet address
· Mask - Destination mask (displayed with /FULL only)
· Flags - Each flag is a one character code. The following list defines each flag:
|
Flag |
Description |
|
U |
Route is "up" (functional) |
|
D |
Route may be “down” |
|
N |
Network route |
|
H |
Host route |
|
G |
Gateway - Route uses a specific gateway |
|
I |
Interface route - Route is an actual network interface |
|
L |
Locked - Someone created the route with the /LOCK qualifier |
|
R |
Dynamic route - Someone created the route using an ICMP redirect message |
|
A |
Automatic route - Someone created the route using RIP or RAP |
|
X |
Route marked for delete, will be deleted when no longer referenced |
· Reference count - Number of connections currently using the route
· Use count - Number of datagrams transmitted using this route
· Line ID - Line identification of the network interface used to send datagrams to this route's destination
· Path MTU associated with the route (displayed with /FULL only)
SHOW ROUTES is equivalent to the UNIX netstat -r command.
Format
SHOW ROUTES
Qualifiers
/CONTINUOUS
Display of the information uses the OpenVMS Screen Management Facility, which updates it every two seconds. (NETCU does not highlight areas of change.) Do not use together with /OUTPUT. See the SHOW COUNTERS command for the screen commands to use. TCPware ignores /CONTINUOUS if SYS$OUTPUT is not a terminal class device or the terminal is not a scope.
/FULL
Displays the full routing information.
/HOST_NAMES
Shows host names, if available, instead of IP addresses.
/OUTPUT=filespec
Sends output to the specified file. If omitted, output displays on the terminal screen. Do not use together with /CONTINUOUS.
Examples
1. Displays the normal routing information for your current host.
NETCU> SHOW ROUTES
TCPware(R) for OpenVMS Internet Routing Table:
Destination Gateway Flags RefCnt UseCnt Line
------------ ------- ----- ------ ------ ----
255.255.255.255 192.168.5.0 UH 0 0 SVA-0
all others (default) 192.168.5.126 UNG 0 665 SVA-0
192.168.5.0 192.168.5.21 UNIL 0 2300 SVA-0
127.0.0.0 127.0.0.1 UNIL 0 0 LPB-0
2. Displays the full routing information for your current host.
NETCU> SHOW ROUTES /FULL
TCPware(R) for OpenVMS Internet Routing Table:
Destination Gateway Flags RefCnt UseCnt Line
----------- ------- ----- ------ ------ ----
192.168.142.0 192.168.142.7 UNIL 0 2196 SVA-0
MASK=255.255.255.0
PATH_MTU=1500
127.0.0.0 127.0.0.1 UNIL 0 1 LPB-0
MASK=255.0.0.0
PATH_MTU=64512
SHOW SERVICES
Displays information on the protocols and ports the NETCP master server process services. The below table describes each piece of information SHOW SERVICES displays.
|
Output Heading |
Provides |
|
Protocol |
Protocol name (TCP or UDP). |
|
Port |
Service name or number of the port. |
|
Active |
Count of how many servers are active for the port (except the TELNET server). |
|
Limit |
Maximum number of servers that can be active for the port. |
|
Connects |
Total number of connections made to this service since someone added it. |
|
Errors |
Total number of errors associated with the service. (For example, errors result when resources are insufficient to run the server, or the server image does not exist.) The TCPWARE:NETCP.LOG file logs each connection serviced. You can have this file obtain details on errors, and monitor access and security violations. |
|
Image |
Name of the server image. |
Format
SHOW SERVICES [port protocol]
Parameters
port
Service name or port for which to display information. Accepts any service name defined in the TCPWARE:SERVICES. file. If you specify a port, you must also specify a protocol. If you omit both, shows service information for all ports and protocols. Use 0 as a wildcard.
protocol
Protocol for which to display information. Enter TCP, UDP, STREAM, DGRAM, BG_TCP, or BG_UDP. If you specify a port, you must also specify a protocol. If you omit both, NETCP shows service information for all ports and protocols.
Qualifiers
/FULL
Displays complete information for each service.
/NUMERIC
Displays port numbers in numeric form. If omitted, NETCU tries to translate these numbers into service names using the TCPWARE:SERVICES. file.
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
Examples
1. Displays a summary of activity for all ports using the STREAM protocol. This is especially useful for determining if the R services are running so that you can use RCP.
NETCU> SHOW SERVICES
TCPware(R) for OpenVMS TCP Services:
Protocol Port Active Limit Connects Errors Image
-------- ---- ------ ------ -------- ------ -----
TCP discard 0 none 0 0 TCPWARE:DISCARDD
TCP daytime 0 none 0 0 TCPWARE:DAYTIMED
TCP telnet 0 none 2 0
SHOW SERVICES 0 STREAM
TCPware(R) for OpenVMS NETCP Services:
Protocol Port Active Limit Connects ErrorsImage
-------- ---- ------ ----- -------- -----------
STREAM exec 0 none 0 0
STREAM login 0 none 0 0
STREAM shell 0 none 1 1
2. Displays a full summary for the DISCARD service.
NETCU> SHOW SERVICES/FULL DISCARD TCP
TCPware(R) for OpenVMS NETCP Services:
Protocol Port Active Limit Connects Errors Image
-------- ---- ------ ----- -------- ------ -----
TCP discard 0 none 0 0 TCPWARE:DISCARDD
/ROUTINE=create_server_process
/PROCESS_NAME=DISCARDD
/LOG
/NOLISTEN
/INACTIVITY_TIMER=(TIME:30, CHECK_INTERVAL:5)
/INPUT=NLA0:
/OUTPUT=NLA0:
/ERROR=NLA0:
/PRIVILEGES=(TMPMBX,NETMBX)
/UIC=[SYSTEM]
/PRIORITY=4
/AST_LIMIT=10
/IO_BUFFERED=6
/BUFFER_LIMIT=10240
/IO_DIRECT=6
/ENQUEUE_LIMIT=6
/FILE_LIMIT=20
/PAGE_FILE=10000
/SUBPROCESS_LIMIT=0
/QUEUE_LIMIT=8
/WORKING_SET=200
/EXTENT=500
/MAXIMUM_WORKING_SET=300
/NOACCOUNTING
SHOW SNMP
Displays the SNMP counters maintained by the local host.
|
Note: This command can only display the local counters. It does not use the SNMP protocol to obtain the counters and therefore cannot display the counters maintained by a remote host.
|
Format
SHOW SNMP group[,group …]
Parameter
group
Can be one or more of IP, ICMP, MIB_VARIABLE, TCP, or UDP separated by commas.
MIB_VARIABLE[=variable]
MIB_VARIABLE returns the value of the variable specified, or the entire MIB tree if no variable is specified. When MIB_VARIABLE is used /HOST can be used to get information from a host other than the one that NETCU is running on. /COMMUNITY is used to specify the SNMP community string; the default value is public.
Qualifier
/COMMUNITY=community_name
/HOST=host_name
These are only valid when MIB_VARIABLE is specified. The default value for /HOST is 127.0.0.1 (localhost).
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
Examples
1. Displays the TCP SNMP counters.
NETCU> SHOW SNMP TCP
2. Displays the TCP and UDP SNMP counters.
NETCU> SHOW SNMP TCP,UDP
SHOW STATISTICS
Displays statistics information on the NFS server, useful in troubleshooting if problems occur. Appends the statistics to the TCPWARE:NAMED.STATS file and appends the memory statistics to the TCPWARE:NAMED.MEMSTATS file. See below for the statistics returned. The server must be running.
Format
SHOW STATISTICS
Qualifiers
/RESET
Displays the counter information, then resets the counters. Requires OPER privilege.
/TIMES
Displays the additional average and maximum times (in milliseconds) for certain NFS requests listed.
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
Description
The NFS statistics returned by the command are:
|
Started |
Date and time someone started the server. |
|
Uptime |
Total amount of time the server has been running. |
|
Memory in use |
Total amount of dynamic memory (in bytes) the NFS server uses. This includes memory allocated for the RPC server routines. |
|
Threads |
NFS thread counters give the total threads available, the current number of threads in use, and the maximum number of threads that have been in use at one time. These statistics can give an indication of server load. If the maximum number of threads in use at one time is equal to the total threads available, you may want to increase the number of threads defined by the parameter NFS_THREADS. |
|
Files |
File system counters include the number of opens and closes performed by the server, the number of files currently open, and the maximum open files at one time since someone started the server.
The number of files currently open and the maximum open files at one time can be an indication of the load on the server. |
|
NFS |
NFS counters return the total NFS procedure calls, and the total calls for each NFS procedure since you started the server. These counters can give an indication of the load on the server.
total is the
total number of calls |
|
RPC |
RPC counters provide information on RPC operations. This includes the total number of receives, transmits, XID hits, and duplicate receives.
The XID hits counter gives the number of cached replies the NFS server retransmitted. The duplicate receives counter gives the number of times the server received a duplicate request for an operation that was in progress at the time of the request. If either of these counters is excessive you may need to increase the timeout time on the NFS-client host(s). |
|
RPC Errors |
RPC counters also returns the following error conditions: receive and transmiterrors, authentication errors, decode errors, and RPC program errors. |
|
MOUNT |
MOUNT counters return the total MOUNT procedure calls, the calls for each MOUNT procedure since someone started the server, the total number of directory mounts since someone started the server, and the number of directories currently mounted.
total is the
number of MOUNT calls |
Example
The command description section describes the output parameters for this example. The /TIME qualifier includes the average and maximum times for the indicated NFS requests.
NETCU> SHOW STATISTICS /TIME
NFS Show Statistics Copyright (c) Process Software
Started: 1-FEB-2021 07:24:05 Uptime: 14 07:05:53 Memory in use: 1414850
Threads: total 40 current 0 max 11
Files: opens 54 closes 54 cur. open 0 max.open 5
NFS: total 2519 bad call 0 fail 0
null 6 getattr 149 setattr 6 read 396 lookup 1381
ave: 0 ms 7 ms 82 ms 78 ms 20ms
max: 0 ms 40 ms 100 ms 180 ms 50 ms
mkdir 0 write 396 create 6 remove 12 rename 18
ave: 0 ms 38 ms 83 ms 38 ms 117 ms
max: 0 ms 510 ms 90 ms 120 ms 130 ms
rmdir 0 readdir 51 statfs 1 link 0 symlink 0
ave: 0 ms 32 ms 10 ms 0 ms 0 ms
max: 0 ms 230 ms 10 ms 0 ms 0 ms
readlink 0 other 0 adfread 97 adfwrite 6
ave: 0 ms 0 ms 7 ms 27 ms
max: 0 ms 0 ms 50 ms 30 ms
RPC: recv 2520 xmit 2520 xid hits 0 dup recv 0
RPC errors: recv 0 xmit 0
authweak 0 authother 0 decode 0 noproc 0 noprog 0
progvers 2 systemerr 0
MOUNT: total 1 bad call 0 fail 0
mount 1 unmount 0 null 0 dump 0 mnt export 0
mounts 1 cur. mount 1
SHOW TIMEZONE
Displays the offset from universal time and optional time zone name.
Format
SHOW TIMEZONE
Examples
1. This is displayed if the time was set by the numerical value -0500.
$ NETCU SHOW TIMEZONE
Offset from universal time (UT) is -05:00:00
2. This is displayed if the time was set by the value EST.
$ NETCU SHOW TIMEZONE
Offset from universal time (UT) is -05:00:00 (EST)
SHOW NAMED VERSION
Prints the current BIND version number.
Format
SHOW NAMED VERSION
Qualifiers
/ALL
Displays any patch versions of the executables along with their link date and times.
/OUTPUT=filespec
Uses the specified file instead of the terminal for output.
SHOW VERSION
Displays the current version of TCPware.
Format
SHOW VERSION
Qualifiers
/ALL
Displays any patch versions of the executables along with their link data and times. Also shows your maintenance agreement number (MAS) if you entered it during CNFNET configuration.
/OUTPUT=filespec
Uses the specified instead of the terminal for output.
Example
$ NETCU SHOW VERSION /ALL
TCPware(R) for OpenVMS V6.1 Copyright (c) Process Software
Build Revision 31
MAS number : <none entered in configuration>
TCPware Image
Version Link Date/Time
-----------------------------------------------------------------
TCPWARE:BGDRIVER.EXE TCPWARE V6.0 3-NOV-2021 14:15:23
TCPWARE:CHARGEND.EXE TCPWARE V6.0 3-NOV-2021 14:17:23
TCPWARE:CHAT.EXE TCPWARE V6.0 3-NOV-2021 14:16:49
Shows the current TCPware version along with any patches and their link and date times.
SPAWN
Executes DCL commands within NETCU.
Format
SPAWN [command-line]
Parameter
command-line
DCL command line you want executed. If omitted, NETCU spawns an interactive subprocess. To return to NETCU from an interactive subprocess, enter LOGOUT.
Examples
1. Displays the time on your local host without leaving the NETCU utility.
NETCU> SPAWN SHOW TIME
1-MAY-2021 14:02:48
NETCU>
2. Initiates DCL command mode and returns the DCL prompt.
NETCU> SPAWN
$ SHOW TIME
1-MAY-2021 14:02:51
$ LOGOUT
Process SMITH_1 logged out at 1-MAY-2021 14:02:54.34
SSHKEYGEN
Generates authentication key pairs. The format of the keys is incompatible between SSH1 and SSH2. Therefore, the correct format keys must be generated for each version of the protocol to be supported.
Each key may be protected via a passphrase, or it may be left empty. Good passphrases are 10-30 characters long and are not simple sentences or otherwise easily guessable. Note that the passphrase can be changed later, but a lost passphrase cannot be recovered, as a “one-way” encryption algorithm is used to encrypt the passphrase.
Refer to the section on SSHKEYGEN in the TCPware Users Guide, Chapter 16, "Accessing Remote Systems with the Secure Shell (SSH) Utilities", for details on using SSHKEYGEN.
START/DNIP
Configures and starts a single DECnet over IP tunnel between the local host and another host.
|
Note: You would normally not use this command directly. Instead, you should configure DECnet over IP tunnels through CNFNET (as described in Chapter 28 of the TCPware Management Guide). TCPware then issues the START/DNIP command during STARTNET.
If you decide to use this command directly, keep in mind that it only establishes the TCP connection for the tunnel. It does not inform DECnet that the tunnel exists. For DECnet to use the tunnel, perform the following commands:
$ MCR NCP SET LINE dev-n-u STATE ON $ MCR NCP SET CIRCUIT dev-n-u STATE ON
|
Format
START/DNIP line-name remote-host local-port remote-port
Parameters
line-name
DECnet line name (format dev-c-n) of the DECnet-over-IP tunnel to configure and start.
remote-host
Internet host name of the remote host establishing the tunnel.
local-port
TCP port number on the local host establishing the tunnel.
remote-port
TCP port number on the remote host establishing the tunnel.
Example
Configures the tunnel DNIP-0-1 to connect to node BETA using TCP port number 777 on the local host and TCP port 654 on BETA. Attempts to establish a connection and start up the tunnel.
NETCU> START/DNIP DNIP-0-1 BETA 777 654
START/INET
Instructs the Network Control Process (NETCP) to start the INET device driver. Requires OPER privilege.
|
Note: Use the TCPware startup command procedure, STARTNET.COM, to start TCPware. See the TCPware Installation & Configuration Guide for details.
|
Format
START/INET
START/IP
Instructs NETCP to start the IP protocol. Issue this command for each network device that the local host supports. Requires OPER privilege.
|
Note: Use the TCPware startup command procedure, STARTNET.COM, to start TCPware. See the TCPware Installation & Configuration Guide for details.
|
Format
START/IP line ia [line-specific-info]
Parameters
line
Line ID for the network device. You can use a wildcard symbol for the specific device number. For example, you can specify:
NETCU> START/IP SLIP-* ...
This assigns the lowest unused and unique line ID for the interface type. This also defines the TCPWARE_LINE (global) symbol with the assigned line ID. For example:
NETCU> START/IP SLIP-* 1.2.3.4 TTA2:
$ SHOW SYMBOL
TCPWARE_LINE
TCPWARE_LINE = "SLIP-0"
Use this wildcard feature with any line type. However, it is less meaningful for line IDs related to physical device names (such as Ethernet and FDDI interfaces).
ia
Local host's internet address or host name for the line.
line-specific-info
Parameter used only for SLIP, IP-over-DECnet, HYPERchannel, and HP Wide Area Network Device Drivers lines, as in the below table.
|
For Line Type... |
Line-specific-info is... |
|
SLIP Lines |
OpenVMS terminal device name for the SLIP line. If omitted for a SLIP line, NETCU assumes the TCPWARE_SLIP_n system logical defined the device (where n is the line’s controller number). |
|
IP-over-DECnet Lines |
Required DECnet link information. Enter it in the format:
node-name::”TASK=object-name”
node-name is the listener node when issued from the master node, and the master node when issued from the listener node and object-name is the object used on the listener node; both the master and listener nodes must specify the same object-name:
An IP-over-DECnet line has a master node at one end and a listener node at the other end. |
|
HYPERchannel Lines |
Local HYPERchannel interface address. The format for this parameter is aa-bb-cc-dd, where aa, bb, cc, and dd are hexadecimal values representing each byte of the address as follows:
The value aa is the global network address domain (if none, specify 00) The value bb is the global network address network (if none, specify 00) The value cc is the physical unit The value dd is the logical unit
NETCU uses the cc-dd portion of the address as the path address in the H269 driver’s IO$_ATTACH function. Always specify the 32-bit HYPERchannel address. |
|
HP Wide Area Network Device (WAN) Lines |
Quoted string of the line configuration options shown in the below table. An example of line-specific-info is:
“PROTO DDCMP POINT CLOCK INTER LINE SPEED 6400”
Note that for the option specifications: · You must include the quotation marks · You can use keyword abbreviations |
|
Parameter |
Option/Value |
Description |
|
PROTOCOL |
DDCMP POINT |
Line protocol used. |
|
DUPLEX |
HALF |
Defines whether the line operates in full or half duplex mode. |
|
CLOCK |
INTERNAL |
Defines whether the line uses internal or external clocking. |
|
CRC |
type |
Type of CRC used. Not recommended. |
|
LINE SPEED |
speed |
Line speed. This setting is only useful if you specify CLOCK INTERNAL. |
|
RECEIVE BUFFERS |
number |
Number of receive buffers. |
|
RETRANSMIT TIMER |
time |
Retransmission time (for DDCMP only). |
For details on these parameters, such as the possible values for the line speed or CRC, see the VAX Wide Area Network Device Drivers Programmer’s Guide.
Qualifiers
/ARP_SERVER=HC-address
For HYPERchannel lines, the optional ARP server's HYPERchannel address. If specified, NETCU uses the ARP server to resolve all unknown addresses. If omitted, you must populate the Address Resolution Table before communicating with a peer.
The address format is the same as for the line-specific-info parameter for HYPERchannel lines. This must be a 32-bit HYPERchannel address.
/FLAGS=(option[,option …])
The below table includes the options for Ethernet, FDDI, and Token Ring, as well as LAN emulation in an Asynchronous Transfer Mode (ATM) network environment (known as Classical IP over ATM, or CLIP). The second following table includes these options for PPP, SLIP, and CSLIP, and the third following table includes them for DECnet over IP.
|
/FLAGS Option |
Description |
|
NOBACKTOBACK |
Disables transmitting back-to-back packets to the same physical address. TCPware uses back-to-back transmission by default. |
|
NOBROADCAST |
Disables receiving broadcast packets. Especially useful if an OpenVMS system has multiple Ethernet controllers connected to the same Ethernet. You must disable all but one controller to receive broadcasts. |
|
[NO]RARP |
Enables (RARP) or disables (NORARP) Reverse Address Resolution Protocol (RARP) support. The TCPware system only responds to RARP requests for permanent address entries in its ARP cache. RARP support is enabled by default for all Ethernet, FDDI, and Token Ring interfaces. RARP support is disabled for Classical IP over ATM (CLIP-n) lines. |
|
[NO]TRAILERS |
Enables (TRAILERS) or disables (NOTRAILERS) trailer packet support. NOTRAILERS is the default.
Note: VCI and Classical IP over ATM do not support trailer packets. |
|
[NO]VCI |
Enables (VCI) or disables (NOVCI) VMS Communications Interface (VCI) support. If starting VCI fails or you use /FLAGS=NOVCI, TCPware uses the alternate interface. |
|
/FLAGS Option |
Description |
|
AUTOENABLE |
Enables sending compressed TCP/IP headers in SLIP packets if receiving compressed TCP/IP headers from the peer. |
|
COMPRESSED |
Enables sending compressed TCP/IP headers in SLIP packets. |
|
DOUBLEEND |
Enables sending the “end” character at the start of SLIP packets. This action is optional.
Note: We do not recommend the use of this option when both ends of the SLIP line connect to TCPware hosts - increases processing overhead. |
|
FLOWCONTROL |
Enables a TCPware private extension to the SLIP protocol to allow use of XON/XOFF flow control over the serial ink. You can use this option only when both ends of the SLIP line connect to TCPware hosts. It is especially useful when using reliable compression modems. |
|
(RCV=n) |
Sets the number of receive buffers used for the serial line. n may be from 1 to 9. The default is 6. |
|
/FLAGS Option |
Description |
|
LISTENER |
Issues commands for the passive end of the DECnet link. If omitted, NETCU assumes you issued the command for the master node. |
|
(RETRY=seconds) |
Specifies the retry interval when losing a DECnet link. When entered for the master node, it is the time interval between retries to establish a link. When entered for the listener node, it is the time interval between retries to create the object. The maximum retry time is 65535 seconds (about 18 hours). The default is 60 seconds. |
/MASK=ia
Sets the subnet mask to the specified address.
Use this qualifier to support subnets and supernets. If not specified, NETCU uses the default network mask for the internet address class. NETCU determines the network number from the internet address by ANDing the specified address with the mask.
The below table shows the default network masks for the network classes.
|
Class |
Network Mask |
Internet Address Range |
|
A |
255.0.0.0 |
0.rrr.rrr.rrr—127.rrr.rrr.rrr |
|
B |
255.255.0.0 |
128.000.rrr.rrr—191.255.rrr.rrr |
|
C |
255.255.255.0 |
192.000.000.rrr—223.255.255.rrr |
/MTU=n
Sets the maximum transmission unit (MTU) to n for the line.
The maximum transmission unit is the byte size of the data portion of the largest packet you can transmit. If omitted, TCPware uses the default value for the line. The maximum allowable MTU value is 64512 bytes. The below table lists the default MTU for the line type.
|
Line Type |
Default MTU |
Comments |
|
Classical IP over ATM |
1500 |
|
|
Ethernet |
1500 |
|
|
FDDI |
4352 |
|
|
HYPERchannel |
4096 |
|
|
IP-over-DECnet |
2048 |
|
|
IP-over-X.25 |
1500 |
Set the MTU to 576 bytes if the system should communicate with older version of IP-over-X.25 (RFC 877). Configure the MTU over 1500 bytes only be prearrangement with the other sites. |
|
LAN Emulation over ATM |
1500 |
|
|
proNET |
2040 |
|
|
Token-Ring |
4092 |
|
|
WAN |
1500 |
|
/UNNUMBERED_INTERFACE
Use this qualifier when starting an unnumbered interface, especially for SLIP lines. NETCU does not assign unnumbered interfaces a local address. However, you must specify an internet address (ia), as TCPware uses this address when originating datagrams for the interface if you do not explicitly specify a source address.
Examples
1. Starts the IP protocol for the QNA-0 line and sets the line's local internet address to 10.0.0.1.
NETCU> START/IP QNA-0 10.0.0.1
2. Starts the IP protocol for the SLIP-0 line on device TXA7: and sets the line's local internet address to 192.168.5.6.
NETCU> START/IP SLIP-0 192.168.5.6 TXA7:
3. Starts the IP protocol for DECnet line 4 for the listener node. The internet address is 192.168.5.2. LILAC is the master node and DGCFF is the object name of the listener.
NETCU> START/IP DECNET-4 192.168.5.2-LILAC::"TASK=DGCFF"/FLAGS=LISTENER
4. Starts the IP protocol for the HYPERchannel HYP-0 line and sets the local internet address to 10.0.0.1. The local HYPERchannel address is 01-01-13-01 and ARP server's HYPERchannel address is 01-01-12-11.
NETCU> START/IP HYP-0 10.0.0.1 01-01-13-01/ARP_SERVER=01-01-12-11
5. Starts the IP protocol for SJA1: (the second line on the first DSV11 controller). The device will run the DDCMP protocol at 19200 baud.
NETCU> START/IP DSV-1 10.0.0.5 "PROTOCOL DDCMP POINT LINE SPEED 19200"
Pseudo devices
You can start pseudo devices by using the START/IP command. Refer to Chapter 1 of the TCPware Management Guide for more information on pseudo devices.
Format
START/IP PSD-n Internet-Address Real-Line-ID
Parameters
n
This is the pseudo device line-id number (from 0 to 255). The number is not meaningful but must be unique for each pseudo device; it identifies the instance of the pseudo device.
Internet-Address
This is the Internet address of the TCPware system on the network.
Real-Line-ID
This is the line-id of the physical device.
Qualifiers
/MASK
This qualifier can be used to specify the network mask for the network.
/ARP
/FLAGS
/UNNUMBERED
These qualifiers are not allowed and result in an error if specified.
/MTU
This qualifier, if specified, is ignored as the MTU used is that of the physical device.
Example
In this example, a pseudo device is started that is associated with the ISA-0 device (this is the Ethernet network to which the system is connected). The Ethernet network has two IP network numbers assigned to it (192.116.1.0 and 192.168.2.0) and the system has two Internet addresses assigned to it, one on each network, 192.168.1.1 and 192.168.2.1.
NETCU> START/IP ISA-0 192.168.1.1
NETCU> START/IP
PSD-0 192.168.2.1 ISA-0
START/PWIP
Instructs NETCP to start the PWIPDRIVER. Requires OPER privilege. PATHWORKS Version 5.0 and later and DECnet/OSI Version 6.0 and later use PWIPDRIVER for TCP/IP support.
Format
START/PWIP
START/TCP
Instructs NETCP to start the TCP protocol. Requires OPER privilege. You must start the Internet Protocol (IP) before you can start the TCP protocol. See the START/IP command.
|
Note: If you already started TCP, you can issue this command to change a parameter value. However, if you do not explicitly specify a parameter, it reverts to its default value as described below.
|
Use the TCPware startup command procedure, STARTNET.COM, to start TCPware. See the TCPware Installation & Configuration Guide for details.
Format
START/TCP
Qualifiers
/KEEPALIVE
/NOKEEPALIVE
Determines if TCP sends KEEPALIVE probes to a peer to see if the peer is still there. If a connection is idle, TCP periodically sends KEEPALIVE probes to solicit a response. The KEEPALIVE probe assumes the peer is down and closes the connection if a specified time period elapses and there is no response. To change this qualifier, edit the STARTNET.COM file or add the appropriate command to the ROUTING.COM file. /KEEPALIVE is the default.
/MSS=bytes
Sets the maximum segment size (MSS) to bytes. MSS is a TCP parameter that specifies the maximum number of bytes that TCP transmits in a single segment, which is the IP datagram size minus 40 bytes. The minimum MSS value is 512 bytes, the maximum is 61440, and the default is 16384 bytes. A host cannot send datagrams larger than the lesser of MSS and the MTU the network interface uses. Path MTU discovery (see /PATH_MTU_DISCOVERY) may dynamically adjust the MSS to the value advertised by the peer and will never exceed it. If omitted, the value is set to 0, which means no limit, which is the preferred setting for most cases.
/MWS=bytes
Sets the maximum window size (MWS) to bytes. The MWS is a TCP parameter that specifies the number of bytes the peer is willing to receive (in one or more segments). The default MWS is 24576 bytes. The TCP protocol allows a top maximum window size of 65535.
TCPware supports a maximum MWS value of 262144 bytes.
Restrict use of a window size of more than 65535 bytes to situations where
there is a high bandwidth-times-round-trip-delay product; for example, in some
satellite links. TCPware uses the Window Scale option by default (see the
/WINDOW_SCALE qualifier).
Communication over a high bandwidth times round trip delay product (like some satellite links) works best if you:
· Configure all systems with the same window size.
· Choose a window size that matches the actual bandwidth and delay. For example, a window size of 112500 should be about optimum for a bandwidth of 1.5 Mbit and round-trip delay of 600 msec as shown here.
· Choose a window size that is slightly larger than the calculated value, rather than slightly smaller than the calculated value.
In some cases, a window size in excess of 65535 may slightly degrade Ethernet performance. This should not cause visible problems.
/NODELAY
Normally TCP may delay a transmit for a short period of time so that if there are multiple rapid transmits, they can be coalesced into larger packets, placing fewer packets on the network and in general causing improved network performance. For some applications though, this ends up providing a poor user experience. /NODELAY allows this feature of the TCP protocol to be disabled.
/NODELACK
Normally TCP will delay the ACK of a received segment for a short period of time (up to 200ms) so that if multiple segments are received in that time and no data is being sent back, multiple received segments can all be ACKed in one ACK segment. This will (in general) lead to improved network performance. /NODELACK allows this feature of the TCP protocol to be disabled.
/PATH_MTU_DISCOVERY
/NOPATH_MTU_DISCOVERY
Enables or disables Path MTU discovery logic, which prevents excessive datagram fragmentation by dynamically discovering the maximum transmission unit (MTU) of an arbitrary internet path. Path MTU discovery is enabled by default.
Path MTU discovery is an IP protocol (described in RFC 1191) that uses the least value of the MTUs it finds among the hops on a datagram's path. It starts with the MTU set for the interface and looks for a smaller value embedded in an ICMP reply from any traversed router, until it can estimate an MTU low enough to prevent fragmentation. The host also periodically sends out an increased MTU value to test for upward changes in MTUs along the path.
/PROTECTED_PORTS
/NOPROTECTED_PORTS
Enables or disables protection for ports below 1024. When protected, an application program must have BYPASS or SYSPRV privilege to listen on a port below 1024. /PROTECTED_PORTS is on by default.
/WINDOW_SCALE
/NOWINDOW_SCALE
Enables or disables sending the Window Scale option (one of the TCP extensions for high performance options described in RFC 1323) when establishing connections. Some TCP/IP implementations cannot handle this option or need to be updated to do so. With /NOWINDOW_SCALE, TCPware does not send the Window Scale option, but continues to acknowledge its support for incoming connections specifying it. /WINDOW_SCALE is on by default.
START/UCX
Instructs NETCP to start the BGDRIVER protocols. Requires OPER privilege.
Format
START/UCX
START/UDP
Instructs NETCP to start the UDP protocol. Requires OPER privilege.
You must start the Internet Protocol (IP) before you start the UDP protocol. See the START/IP command.
|
Note: If you already started UDP, you can issue this command to change a parameter value. However, if you do not explicitly specify a parameter, it reverts to its default value as described below.
|
Format
START/UDP
Qualifiers
/MDS=n
Sets the maximum datagram size (MDS) to n bytes. UDPDRIVER will not transmit datagrams larger than n. The default MDS value is 16384. The maximum MDS value is 61440 bytes.
/PROTECTED_PORTS
/NOPROTECTED_PORTS
Enables or disables protection for ports below 1024.
When protected (the default), an application program must have BYPASS or SYSPRV privilege to open a port for a port number below 1024.
/UNSOLICITED_RECEIVE_LIMIT=n
Sets the default limit of UDP unsolicited receives, or datagrams buffered on a socket if there is no outstanding read before they are dropped.
STOP/DHCP
Shuts down the Dynamic Host Configuration Protocol (DHCP) server in an orderly manner. Requires SYSPRV or OPER privilege.
To address the DHCP V4 server, use DHCP4 instead of DHCP in the command.
Format
STOP/DHCP
STOP/DHCP4
STOP/DNIP
Shuts down any or all DECnet over IP tunnel(s) currently configured and running on this host.
|
Note: You would normally not use this command directly. Instead, you should stop DECnet over IP tunnels through the SHUTNET.COM procedure described in the Chapter 26 of the TCPware Management Guide.
|
|
Note: If you decide to use this command directly, keep in mind that it only shuts down the TCP connection for the tunnel. It does not inform DECnet that the tunnel no longer exists. For DECnet to stop trying to use the tunnel, perform the following commands:
$ MCR NCP SET LINE dev-n-u STATE OFF $ MCR NCP SET CIRCUIT dev-n-u STATE OFF
|
Format
STOP/DNIP dev-n-u Shuts
down DECnet tunnel dev-n-u
STOP/DNIP/ALL Shuts
down all DECnet over IP tunnels
Parameter
dev-n-u
DECnet line name of the DECnet-over-IP tunnel to shut down.
Qualifier
/ALL
Shuts down all DECnet-over-IP tunnels on this host.
Examples
1. Shuts down the single DECnet-over-IP tunnel DNIP-0-0 on this host.
NETCU> STOP/DNIP DNIP-0-0
2. Shuts down all DECnet-over-IP tunnels on this host.
NETCU> STOP/DNIP/ALL
STOP/DNS
Instructs the nameserver to shut down. Stops the Domain Name Services (DNS) Resolver process (TCPware_DNS).
|
CAUTION! Do not use this command in most cases. The DNS Resolver process is the last one shut down with SHUTNET.COM and the first one started with STARTNET.COM. If you use STOP/DNS and then restart TCPware without the DNS Resolver process present, you will get a series of error messages beginning with:
%SYSTEM-F-NOLOGNAM, no logical name match %TCPWARE_NETCU-E-IVPORT, invalid port number or service name
|
To restart the DNS Resolver after having used STOP/DNS, run TCPWARE:STARTUP_RESOLVER.COM as follows:
$ @TCPWARE:STARTUP_RESOLVER DETACH
Format
STOP/DNS
STOP/GATED
Tells the GATED process to halt in an orderly manner.
|
Note: Do not use this command in most cases. Use the SHUTNET.COM GATED command instead.
|
Format
STOP/GATED
STOP/INET
Instructs NETCP to stop the INET device driver. Requires OPER privilege.
Format
STOP/INET
STOP/IP
Instructs NETCP to stop a line. Requires OPER privilege.
Format
STOP/IP line
Parameter
line
Line ID of the network device to be stopped.
Examples
1. Stops the IP protocol on the SLIP-0 line.
NETCU> STOP/IP SLIP-0
2. Stops the IP protocol on the SVA-0 ethernet interface.
NETCU> STOP/IP SVA-0
STOP/NAMED
Stops the nameserver.
Format
STOP/NAMED
STOP/NETCP
Stops the Network Control Process (NETCP) process. Requires OPER privilege. When you enter this command, NETCP shuts down the network and terminates itself.
|
Note: This command is for use by the SHUTNET.COM procedure only. To stop TCPware, use the SHUTNET.COM procedure. See the TCPware Installation & Configuration Guide for details.
|
Format
STOP/NETCP
STOP/PWIP
Stops the PWIPDRIVER. Requires OPER privilege. PATHWORKS Version 5.0 and later and DECnet/OSI Version 6.0 and later use PWIPDRIVER for TCP/IP support.
Format
STOP/PWIP
STOP/SERVER
Stops the NFS server. Requires OPER privilege.
|
Note: We recommend you use the NFS-OpenVMS server shutdown command procedure, SHUTNET.COM NFS, to stop the NFS server.
|
Format
STOP/SERVER
STOP /SSH
Shuts down all SSH server processes, terminating all active SSH sessions to this system. Does not affect SSH sessions outgoing from this system to other systems.
Format
STOP /SSH
Example
$ NETCU STOP /SSH
Starting shutdown of SSH Master server
STOP/TCP
Instructs NETCP to stop the TCP protocol. Requires OPER privilege.
Format
STOP/TCP
STOP/UCX
Instructs NETCP to stop the BGDRIVER protocols. Requires OPER privilege.
Format
STOP/UCX
STOP/UDP
Instructs NETCP to stop the UDP protocol. Requires OPER privilege.
Format
STOP/UDP
TCPDUMP
TCPDUMP prints out the headers of packets on a network interface that match the Boolean expression. The OpenVMS implementation currently only works with HP-compatible Ethernet cards. Some of the command line switches were changed from the UNIX version to support OpenVMS's case-insensitive command line.
PHY_IO privilege is required to use TCPDUMP unless reading packets from a file. If using the TCPware drivers for packet capturing, LOG_IO and SYSPRV or BYPASS privileges are also needed.
Format
TCPDUMP [ options/qualifiers ] [ expressions ]
Options and Qualifiers
|
Note: The command qualifiers are not available if using TCPDUMP as a foreign command on the DCL level. You can mix and match options and qualifiers on the NETCU level only. For a full description of the TCPDUMP command and its options, qualifiers, and expressions, see the TCPware Management Guide, Chapter 31, Network Testing Tools, the TCPDUMP section.
|
TOGGLE GATED TRACING
Toggles GATED tracing on and off. This command opens and closes the GATED log file TCPWARE:GATED.LOG as needed.
Format
TOGGLE GATED TRACING
UNMOUNT ALL
Removes all the mount list entries for the local client host on the specified NFS server or servers. Useful for notifying the remote server host that the server file systems are no longer mounted on the client if the client system goes down and you need to reboot it.
|
Note: Unmounting is not the same as dismounting. UNMOUNT ALL does not dismount a mounted file system.
|
After using UNMOUNT, you can use SHOW MOUNT (in TCPware) or show mount (on a UNIX system server) to verify that the list entry you requested to be unmounted on the specified server(s) is no longer there. The mount list entries are in the /etc/rmtab file on most UNIX systems.
Format
UNMOUNT ALL
Qualifier
/HOST=(server,server…)
Server host or hosts. The parentheses are required for multiple servers. If omitted, the client sends a broadcast message to all local network servers to remove the list entry for the local client host.
Examples
1. Sends a broadcast message to all local network servers to remove the mount list entry for the local client host.
NETCU> UNMOUNT ALL
2. Sends a request to hosts TAU and SIGMA to remove the mount list entry for the local client host.
NETCU> UNMOUNT ALL /HOST=(TAU,SIGMA)
|
Note: The following message can occur after an UNMOUNT ALL request sent to a UNIX system server: %TCPWARE_NETCU_E-CLNTCALLFAIL, RPC Client call failed, RPC: Remote system error
Ignore this message. However, confirm through a SHOW MOUNT command that the mount list entry was, in fact, removed.
|
UPDATE DHCP
Instructs the Dynamic Host Configuration Protocol (DHCP) server to process the update file and add or remove the specified host and subclass declarations. See Chapter 4, DHCP/BOOTP Server in the TCPware Management Guide for a description of the update file and commands.
To address the DHCP V4 server, use DHCP4 instead of DHCP in the command.
Format
UPDATE DHCP
UPDATE DHCP4
Qualifiers
/OUTPUT=filespec
Sends output to the specified file. If not specified, output appears on the terminal screen.
/FILENAME=filespec
Specifies the name and location of the file containing the update commands. Optional. The default is TCPWARE:DHCPD.UPDATES.
UPDATE GATED INTERFACES
Tells the GATED process to rescan the network interfaces.
Format
UPDATE GATED INTERFACES
WRITE
Writes the current TCPware SMTP configuration to SMTP configuration files. (Functionally equivalent to SAVE.)
FORMAT
WRITE config_file
PARAMETERS
config_file
Specifies the name of the file to which to write the current TCPware SMTP configuration. By default, the configuration is saved to the same file from which it was read.